Who planted the Authentication Backdoor in the Juniper ScreenOS? Security experts are making their speculation, but interesting revelations are coming out.
While the FBI is investigating the case searching for responsible for the introduction of a backdoor in a number of Juniper network devices, a number of speculation are circulating on the Internet. Juniper Networks is a technology provider for the US Government and many US federal agencies, including the FBI, this means that attackers may have had access to the traffic related to connections protected through VPNs.
Someone is blaming China, other the NSA, and the majority is pointing a more generic nation-state actor.
The experts that blame the Chinese Government sustain that the compromised appliance was originally developed by the NetScreen Technologies company that was acquired by Juniper Networks in 2004. The NetScreen Technologies was founded by Chinese nationals, for this reason some experts believe that Chinese experts have a deep knowledge of the compromised ScreenOS.
“It’s not hard to find evidence of ongoing work on ScreenOS in Beijing: a quick trawl of LinkedIn turns up several Juniper employees who work on the operating system. The Register in no way suggests that those who work in Juniper’s Beijing offices are in any way associated with the unauthorised code. We nonetheless asked Juniper if the code is known to have come from the Beijing facility.” states a blog post published by The Register.
Many experts speculate the involvement of the NSA, one of the documents leaked by Edward Snowden and disclosed by the German Der Spiegel revealed that the US intelligence had the ability to plant a backdoor in various network equipment, including Juniper firewalls.
There is also speculation that the two backdoors might not be the work of the same state-actor, as they are not connected.
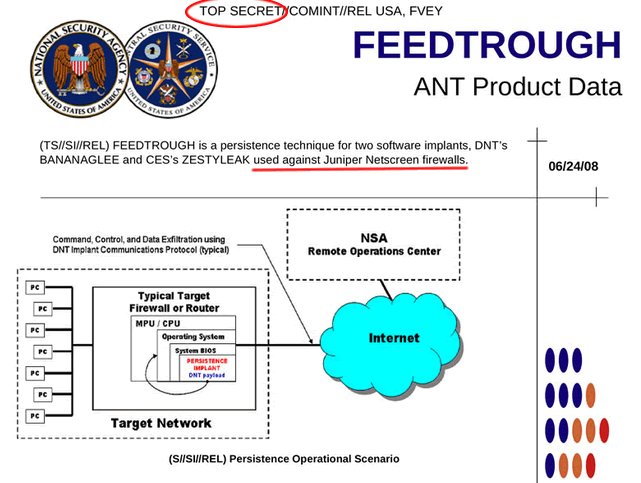
According to the German online magazine, hackers belonging to the ANT division (Advanced or Access Network Technology), operating under the NSA’s department for Tailored Access Operations (TAO),
“In the case of Juniper, the name of this particular digital lock pick is “FEEDTROUGH.” This malware burrows into Juniper firewalls and makes it possible to smuggle other NSA programs into mainframe computers. Thanks to FEEDTROUGH, these implants can, by design, even survive “across reboots and software upgrades.” In this way, US government spies can secure themselves a permanent presence in computer networks. The catalog states that FEEDTROUGH “has been deployed on many target platforms.” states the Der Spiegel online.
HD Moore, the developer of the Rapid7′ Metasploit Framework, confirmed that there are roughly 26,000 Netscreen devices exposed on the Internet with SSH open.
“Shortly after Juniper posted the advisory, an employee of Fox-IT stated that they were able to identify the backdoor password in six hours. A quick Shodan search identified approximately 26,000 internet-facing Netscreen devices with SSH open. Given the severity of this issue, we decided to investigate.” he wrote in a blog post.
HD Moore added that the backdoor might date back to late 2013, and the encryption backdoor to 2012.
“This is interesting because although the first affected version was released in 2012, the authentication backdoor did not seem to get added until a release in late 2013 (either 6.3.0r15, 6.3.0r16, or 6.3.0r17).”
Ronald Prins, founder and CTO of Fox-IT, a Dutch security firm, explained that reverse engineering the patch released by Juniper he was able to discover the master password backdoor (“<<< %s(un=’%s’) = %u,“).
“Once you know there is a backdoor there, … the patch [Juniper released] gives away where to look for [the backdoor] … which you can use to log into every [Juniper] device using the Screen OS software,” he told WIRED. “We are now capable of logging into all vulnerable firewalls in the same way as the actors [who installed the backdoor].” explained Prins.
Fox-IT has also released the Snort rules that can be used by the sys admins to detect unauthorized access to the Juniper devices through the backdoor.
“Since our initial announcement we’ve learned that the number of versions of ScreenO affected by each of the issues is more limited than originally believed. Administrative Access (CVE-2015-7755) only affects ScreenOS 6.3.0r17 through 6.3.0r20. VPN Decryption (CVE-2015-7756) only affects ScreenOS 6.2.0r15 through 6.2.0r18 and 6.3.0r12 through 6.3.0r20,” reported Juniper shared inviting administrators to apply the security updates as soon as possible.
The unique certainly is that someone deliberately inserted a backdoor password into Juniper network devices.