I have been using the Attivo BOTsink by AttivoNetworks as my primary deception platform in the lab for quite some time. I have found it perfect for collecting attacks and analyzing them. I upgraded to the current release – 4.2.3.62 for this review. Upgrading to the next release is easy. Simply go to the Attivo support portal, download the image file and tell BOTsink to use that to upgrade. The process is typical of the overall BOTsink design: easy, intuitive and straightforward.
ADVANCED FEATURE SET
BOTsink has a comprehensive feature set that includes the ability to create both decoys and lures. A complete BOTsink implementation looks exactly like an extension of the internal enterprise to the administrator but to an intruder the two are indistinguishable from each other. Decoy setup is, again, very simple. I set up three decoys for this test and allowed the BOTsink to do the rest. One decoy was a web server sitting at an IP on the Internet – Attivo supplies the web server but you can customize or create your own – and two internal decoys.
Decoys look exactly like legitimate devices except that they gather data for future analysis and any attempt to break out of the decoy is sent to a sinkhole built into the BOTsink. Lures are items of interest to attackers such as documents, email addresses, users, file systems with tempting files and other things that might interest and intruder. One especially nice lure is a document that can report back the address of an intruder who tries to take it.
This is a true AI-based system. It uses unsupervised machine learning to discover the network environment so that the BOTsink can build out the deception net. For example, in this test I made the external web server dual-homed with an internal IP. This mimics the typical configuration of a web server that is accessed internally by web developers and web masters. It took BOTsink just minutes to create decoys of the internal web access – 22 in all. The idea is if an attacker breaks through the external web server into the internal network he will find himself in one of the internal decoys.
Once an attacker has broken into a decoy – SSH, telnet and FTP are favored methods attempted on this decoy – he can work inside the decoy as if it was a real machine. When he does, he leaves forensic footprints that can be followed. I have given the web decoy a simple to guess password for a common account and hackers have had no trouble compromising it. The result has been a treasure trove of forensic data left by the attacker.
BOTsink allows setup of active directory defenses, forensic exam of endpoints and specific endpoint protection pinpointing lateral movement attempts across the enterprise. The forensic capability requires placing the forensic application on the endpoint so it usually is not effective on an attacker device.
ARCHITECTURE
The BOTsink can be an appliance or a virtual system installed in several VM architectures such as VMWare. It also can be installed in the cloud. A separate module called ThreatDirect can collect decoy information – it creates its own decoys – and forward that back to a main BOTsink through a tunnel. This allows a distributed architecture that can span several internal networks.
The BOTsink in our lab is a model 3200 appliance. In the appliance are several virtual machines: CentOS 7, Ubuntu 1.24, Ubuntu 1.31, Windows 7 64 bit, Windows 7 and Windows server 2008. Each of these VMs supports 32 individual addresses so on my appliance I have the possibility of a 192 decoy network to add to my existing network. Of course you probably wouldn’t use all possible IPs since you configure the VM and the configuration is reflected in the IPs. In my case I have the Windows 7 devices set up as user workstations, the Windows server set up as a multipurpose server including AD and the Linux VMs set as web servers. I don’t use all the Windows servers and I don’t use all of the Linux decoys, however.
In addition to the supplied VMs I can add custom VMs. Of course I can add as many applications as I want to the decoys, noting, of course, that some – those that aren’t open source – need to be licensed.
USER INTERFACE
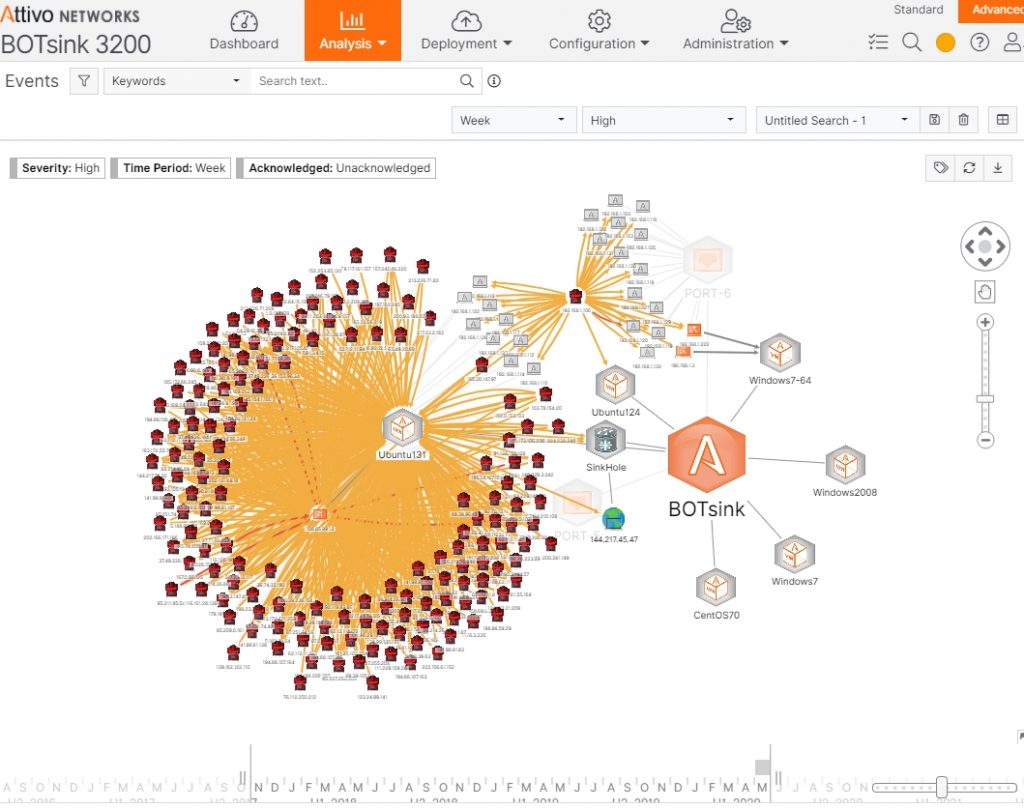
The user interface could not be more straightforward. It consists of three parts: a dropdown set of menus across the top, a set of submenus for each dropdown along the side and additional submenus within various functions. For example, if I select the Analysis dropdown, I can select from several choices such as Events, Endpoints, Network and Endpoint Forensics. If I select Events, I get a display such as Figure 1.
Figure 1 – Analysis-Events Display
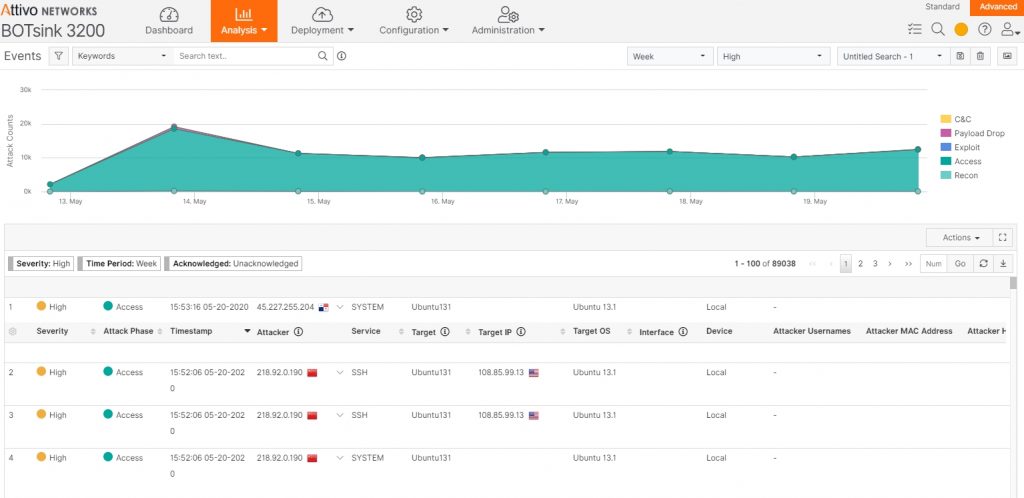
There are additional submenus available. For example, I can search based on keywords, Descriptions, Attacker IP, Target and several others. I can specify the capture period – in this case one week, the severity, high in this case, and I can name the search. I can save the search to return later and I can switch to a tabular view that gives me even more detail as in Figure 2.
Figure 2 – Tabular view of the Analysis-Events Dropdown
Moving all the way to the right of this display I get some very interesting information shown in Figure 3.
Figure 3 – Successful SSH Login From 51.77.66.35 in the UK
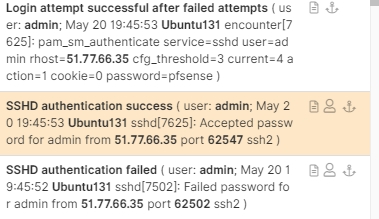
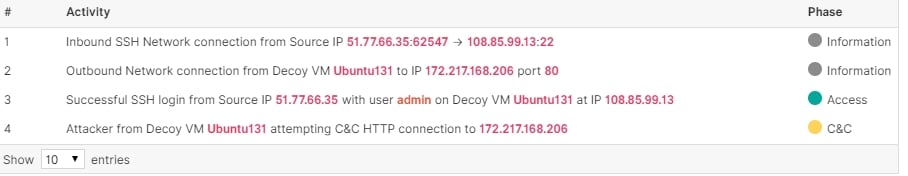
I can expand that even further to get the whole picture of the success (highlighted section) as in Figure 4.
Figure 4 – Activity Log of Successful Login
Note that the attacker attempted to a connection to 172.217.168.206, a command and control server located in the Google cloud.
ANALYSIS of ATTIVO BOTSINK
I have a fair bit of experience with BOTsink and there are two standout features that have made it my primary lab test platform: ease of deployment and comprehensive analysis capability. Deception is showing increasing popularity and there are several deception products on the market. Some are weak on isolation from the enterprise but there are some good ones as well.
BOTsink provides excellent isolation – I have tried unsuccessfully to break out of the deception net – and the sinkhole prevents an attacker from using a decoy as a pivot point for additional attacks or communication with a C&C server. I have seen several examples of attackers trying to use a decoy for spam and an excellent example of a credential stuffing attack. BOTsink identifies attackers quickly by noting attempts to access a decoy or lure. However, should an endpoint be compromised it can be blocked by integrating the BOTsink with any of several smart firewalls.
I have found the functionality excellent but the big win for large enterprises is ease of deployment. The unsupervised machine learning speeds and simplifies deployment in large enterprises. Once the basic BOTsink is deployed the addition of lures, AD protection and forensics is straightforward. Memory forensics can operate at an endpoint or the BOTsink VM.
Monitoring and reporting is about the most comprehensive I’ve seen and it even can analyze executables. Integration with SIEMs and syslog servers as well as its ability to provide distributed deception extend the BOTsink to a full enterprise class security system. By using some configuration tricks, the BOTsink can capture and forward spam and phishing emails safely without compromising the analyst’s computer. This just a simple example of the flexible configuration capabilities of the device.
OPINION
I’ve had the opportunity to see the BOTsink through several versions and it just keeps getting better and better. There is no doubt that it is a true next generation security tool. We are in an environment where malicious acts occur at wire speeds and it is not possible for human operators to keep up. The only real answer today is automation and the only useful automation today is AI, particularly unsupervised machine learning. There is a tendency for security engineers to view deception networks as some sort of souped-up honey pot. That could not be much farther from the truth as BOTsink demonstrates.
Today’s deception network must be able to detect and respond to attacks and – better – to derail the attack completely. With layered capabilities, BOTsink is about as far-removed from its ancestral honeynets as is likely in the near term. As deception networks evolve, I expect to see more innovation coming from Attivo. The core area of growth that I see is leveraging AI to automate the deception, response and forensics capabilities even more than they are today. This growth is not simply the addition of features but, rather, the expansion of the platform to make a more powerful system with growth built in from the start. My opinion is that Attivo is well along this path and I expect to be testing and experimenting with it for some time to come.
BOTsink is highly recommended.
P. R. Stephenson, PhD, CISSP (ret)
Publisher of Future inTense
Exclusively at Cyber Defense Magazine
P.S. Our friends at Attivo reminded me that I have not just the 192 IPs, I actually have many more. I apologize for not calling this out: ‘even though the VMs have 192 total virtual interfaces, the BOTsink can handle up to 2000 decoy IPs that it takes for itself and forwards to the appropriate decoy for engagement’. I should have noted this in the architecture section because it is a very valuable architectural asset. In fact, I use it myself in the lab.