With the recently passed anti-privacy bill proving to be a nightmare to any and all that value their security and anonymity online, the WannaCry ransomware attack has done no favors and has in fact shown the world how vulnerable everyone online really is.
The ransomware attack that took place on Friday, 12th of May 2017, has been spreading ever since. The entire predicament seems like a scene out of the Terminator movies, where Skynet comes into power.

Even though the attack is not farfetched as the Terminator films, it is does show that such fiction could soon become a reality, with AI already being implemented into everyday life. That being said, let’s focus on the WannaCry ransomware, its origins, its impact along with tips that can be taken into account to prevent such an attack from taking place again.
How the WannaCry Ransomware Worked its Havoc
WannaCry is quite simple in how it works, but it is devious to say the least. Once activated, the malware encrypts all data on the machine it infects. The owner of the infected machine is then asked to pay up in Bitcoins in order to regain access to locked data.
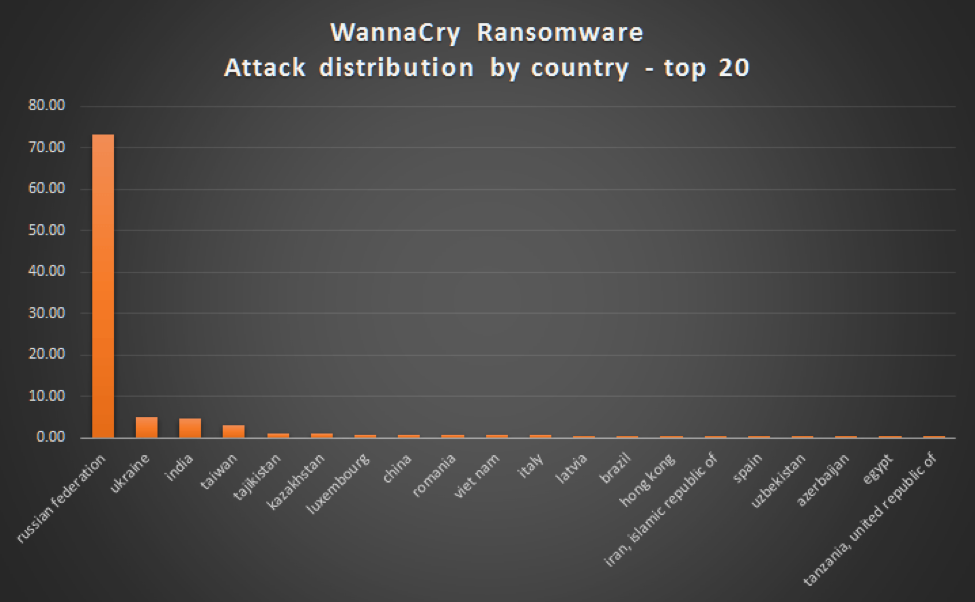
The ransomware exploited a vulnerability in older Windows operating systems, like XP and Windows 7. More than 150 countries were affected, with 200,000 machines being locked for good. Even though a patch was released by Microsoft to prevent further exploitation, it was too late as the damage had been done.

(PC: securelist.com)
The Origin of the WannaCry Attack
What is really alarming is the fact that WannaCry was created by the NSA, although the agency did so unintentionally. The exploit referred to as EternalBlue, was used by Shadow Brokers with the intention of blackmailing users for money, which is what it seems so far. Until now, the three Bitcoin addresses attached to the ransomware have received 151 payments totaling around $50,000.
The WannaCry Ransomware Attack is Just the Beginning
Even though things may have died down, the attack is not over and is in fact just the beginning. A researcher did managed to discover a kill switch which prevented the ransomware from doing further damage, and slowed it down. WannaCry v 1.0 could have been dealt with using the kill switch, but it is highly probable that the next version or versions will not have such exploits.
Experts have suggested that the first wave of the attack may have been dealt with, but the next wave, WannaCry 2.0, which is most likely to hit on Monday, will be much deadlier.
Combatting the WannaCry Ransomware Threat
To prevent the catastrophe from taking place again, owners of machines with older Windows operating systems need to install a new security update/patch. But, the patches won’t be of any help for machines that have already been hit. At the same time, to prevent similar threats, emails from unknown sources are not to be trusted.

So far no tool is present to decrypt systems that have locked out users, although several could be made available soon. For now, the only option is either to pay the ransom or reinstall infected systems. But then again, trusting hackers would not be a wise decision, as there is no certain way to ensure this will not happen again once the required $300 are paid via Bitcoin. What you can do is to take the necessary steps to ensure you aren’t their next victim.
All in all, the WannaCry attack is not to be taken lightly, as it shows how vulnerable internet users really are. Moreover, it also shows how agencies like the NSA are entirely careless and could have had a hand in several major security breaches that took have taken place over the years. This translates to internet users taking more responsibility and upping their game, that is, if they wish to keep their data intact and not be kept hostage in return for a large sum of money.
About the Author:
 Anas Baig is a Cyber Security Expert, a computer science graduate specializing in internet security, science, and technology. Also, a Security Professional with a passion for robots & IoT devices.
Anas Baig is a Cyber Security Expert, a computer science graduate specializing in internet security, science, and technology. Also, a Security Professional with a passion for robots & IoT devices.
Follow him on Twitter @anasbaigdm, or email him directly by clicking here.