Experts warn of ongoing attacks targeting QNAP network-attached storage (NAS) devices to abuse them in cryptocurrency mining.
Researchers at 360Netlab are warning of a cryptocurrency malware campaign targeting unpatched network-attached storage (NAS) devices.
via the unauthorized remote command execution vulnerability (CVE-2020-2506 & CVE-2020-2507)
Threat actors are exploiting two unauthorized remote command execution vulnerabilities, tracked as CVE-2020-2506 & CVE-2020-2507, in the Helpdesk app that have been fixed by the vendor in October 2020.
The flaws affect QNAP NAS firmware versions prior to August 2020.
The malware involved in the campaign was dubbed UnityMiner by 360 Netlab experts.
“On March 2, 2021, 360Netlab Threat Detection System started to report attacks targeting the widely used QNAP NAS devices via the unauthorized remote command execution vulnerability (CVE-2020-2506 & CVE-2020-2507, upon successful attack, the attacker will gain root privilege on the device and perform malicious mining activities.” reads the analysis published by 360 Netlab.
Threat actors customized the program by hiding the mining process and the real CPU memory resource usage information to hide the malicious activity to QNAP owners that could check their system usage via the WEB management interface.
The mining program is composed of unity_install.sh and Quick.tar.gz. unity_install.sh downloads, set up and execute cryptocurrency miner and hijack the manaRequest.cgi program of the NAS. Quick.tar.gz contains the miner program, the miner configuration file, the miner startup script and the forged manaRequest.cgi. Unity is an XMRig cryptocurrency miner.
360 Netlab shared its findings with the vendor on March 3rd, and due to the possible big impact, the researchers publicly disclosed the attacks.
All NAS devices with QNAP firmware released before August 2020 are currently vulnerable to these attacks.
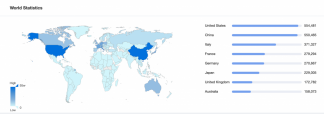
The experts reported 4,297,426 QNAP NAS potentially vulnerable devices exposed online, 951,486 having unique IP addresses, most of them are located in the United States, China, and Italy.
QNAP NAS users should check and update their firmware as soon as possible.
In January, the Taiwanese vendor QNAP published a security advisory to warn customers of a new piece of malware named Dovecat that was targeting NAS devices. The malware was designed to abuse NAS resources and mine cryptocurrency.
In December, QNAP released security updates to fix eight vulnerabilities that could be exploited by attackers to over unpatched NAS devices.
The list of vulnerabilities addressed by QNAP is available here, it includes XSS and command injection issues. The flaws fixed by the vendor are rated as medium and high severity security.
In September, while the AgeLocker ransomware was continuing to target QNAP NAS systems, the Taiwanese vendor urged customers to update the firmware and apps.
In early August, the Taiwanese company urged its users to update the Malware Remover app to prevent NAS devices from being infected by the QSnatch malware.
In June the company also warned of eCh0raix ransomware attacks that targeted its NAS devices.
If you want to receive the weekly Security Affairs Newsletter for free subscribe here.
Follow me on Twitter: @securityaffairs and Facebook
 Pierluigi Paganini
Pierluigi Paganini
International Editor-in-Chief
Cyber Defense Magazine


