By M. Michael Mitama, THETA432
We live in an era where we are continuously bombarded with marketing campaigns of the next silver-bullet that will stop “The Threat”. Overcompensation on malware and misclassification of malware as the threat is so commonplace, we’ve lost sight in our solutions and of what truly is the threat. With our over-focus on malware which is simply a tool to gain access into a network or just cause harm for ransom, we forget about the operators behind the keyboard who truly are the threat. Instead of modeling the true aspect of a threat and their intentions against an industry or even our businesses we continue with the disproportionate spend on tools we end up not using or are oversold on unneeded tool functionality. We continue to set the rat trap inside of our houses instead of plugging those holes that entice them from moving in in the first place.
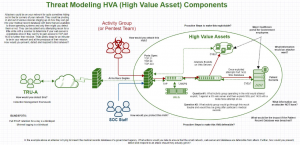
Threat intelligence can be a useful tool for some of this if it is used correctly. Our people’s internal behaviors give rise to interesting data sets instead of buying every feed known to man which may not be tailored for your industry, have duplicate data, overlap, etc. We may have priority intelligence requirements that provide us with directives to assist our understanding of situations or we can model attacks against our “High Valued Assets” and wrap our efforts around those HVAs to harden the holes left open before the rats move in. Codifying this into a process will give rise to useful tools that equip us with the visibility we require and to gain insight into the attack surface of our HVAs and allow us to make our network and services more defensible.
That all being said, it’s time for the industry to take a deeper look at itself and map out the High Valued Assets and data that business exists for. Its time to begin attack simulations and modeling against HVAs and stack and build our defenses accordingly. Obviously, this doesn’t happen overnight but when we identify these assets and simulate an attack scenario, we will find ways to codify processes, model threats, ask questions of our network and data while bringing visibility into our networks and ultimately our customers to make them more defensible.
About the Author
 M. Michael Mitama is CEO of THETA432 and focuses on efficiencies and provides robust frameworks in an innovative array of cyber defense activities. Known as a trusted advisor in cyber defense THETA432 provides deep visibility into company networks providing metrics, KPIs and analysis with their proprietary technique, Dynamically Defined Defense (3D)
M. Michael Mitama is CEO of THETA432 and focuses on efficiencies and provides robust frameworks in an innovative array of cyber defense activities. Known as a trusted advisor in cyber defense THETA432 provides deep visibility into company networks providing metrics, KPIs and analysis with their proprietary technique, Dynamically Defined Defense (3D)