By Milica D. Djekic
According to many media’s releases – the Shodan is characterized as the scariest searching tool of this modern time. The fact is such a search engine could provide us an access to private, business and critical assets and for such a reason – it can be considered as so frightening due to its capability to – once in hands of malicious actors – threaten our safety and security. The purpose of this chapter would be to discuss all aspects being covered with this emerging technology as well as analyze its security’s capacities being offered to its expert’s community.
The role of this search engine
The Shodan is a quite convenient tool for searching the Internet of Things (IoT). Some sources would describe it as so scary, but we would agree with that in case – it gets in hands of the bad guys. This searching tool would offer an opportunity to obtain feedback information from many devices being connected to the web. At Shodan’s homepage – you would notice that there is a searching bar which would allow you to enter some keywords being the criteria for your crawling. Also, you would notice that there would get provided some accesses to the next page which would deal with the web cameras, refrigerators, industrial control systems and much more. The Shodan’s homepage is illustrated in a Figure 1 as follows. This homepage could offer you a good insight into how this system appears and works as well as remove some misunderstandings about its scariness.
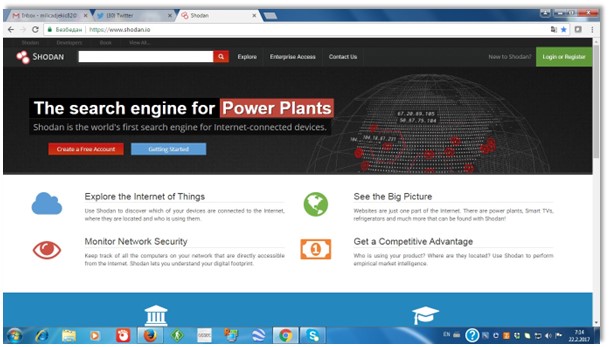
Figure 1. The Shodan’s homepage
As it’s presented through the previous Figure – the Shodan would appear as a quite typical search engine giving you a chance to make a search relying on many different parameters. For instance, you can explore the IoT, monitor network’s security, see the big picture or get a competitive advantage. In addition, this tool would seek from you to create your own account doing some sort of a registration. The reason for so is that would make you leave some information about yourself and support the case if anything gets wrong. We are fully aware of that such a search engine could get exploited by the hacker’s community that could work for organized crime groups or even terrorist organizations. The point is that these guys could try to do something, but they would get caught shortly. The next page within a Shodan’s environment is given in Figure 2 as follows. That illustration would offer us an option to make a closer look at all the possibilities of such a tool.
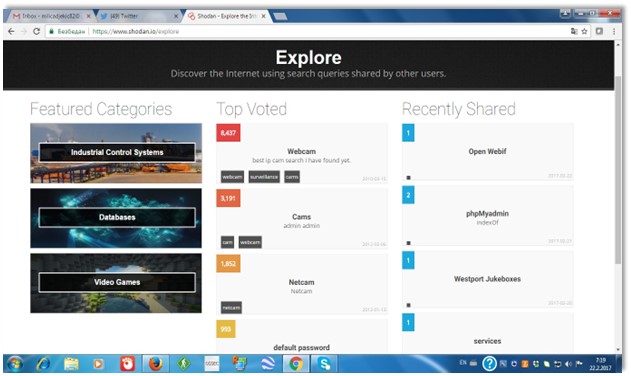
Figure 2. The typical Shodan’s webpage
The illustration being offered in a Figure 2 would show us how it functions if we try to explore this searching tool. As illustrated – there would be many opportunities such as industrial control systems, databases, video games, web cameras, services, default passwords and so on. We would strongly encourage the expert’s community or even an average user to try to play with these options and through such a research – attempt to discover all the potentials of this amazing tool. We are also aware of all the disadvantages that may occur if this service is used inappropriately and illegally. Finally, as already suggested through this learning material – the Shodan could get found at the following web domain – www.shodan.io – so we would recommend to everyone to try to track even their own devices being connected to the web and somehow discover how they could get protected from the malicious operations.
Would the Shodan be good or bad?
There would be many discussions trying to conclude if the Shodan is good or bad. As we would indicate – that depends on people using it. It’s quite clear that people dealing with their private, business or strategically important infrastructure could use this tool to improve their security’s capacities. So, if it’s applied by good people – the Shodan would be good. On the other hand – if in the hands of bad guys – this tool would get bad. As we would already say – this search engine could support us in resolving the case, but we are quite skeptical about its capacities in terms of preventing the crime even happens.
So, the only reason that could leave the bad guys far away from this service is that they would so commonly get aware of the consequences in case they try anything. Maybe some terrorist organizations would not think like so. They would seek an opportunity to obtain their task even such an operation would lead them into a certain death. Those folks are usually fanatics and we would strongly appeal to the international defense and intelligence to have this in mind any single time they deal with the Shodan and those cases of extremism.
Our recommendation would be that a technology should progress faster in order to alarm the Shodan’s owners about any attempt of logging in from any concerning part of the world. As it’s known, the terrorists could come from the westerns countries as well which would make this task being much complicated and leave this question remaining open as one of the challenges to the future.
The Shodan and expert’s community
The Shodan would so commonly be correlated with the expert’s community that would use it for its researches trying to find some vulnerability within the IoT functioning as well as some ways of improving its security’s capabilities. Even the Shodan’s creators would agree that their primary intent was to make something being so suitable to researchers who got interested to explore all the frontiers of an IoT technology. So, we would suggest to anyone dealing with this search engine to try to find the weaknesses of his own IT system as well as follow the best practice in order to leverage its computing abilities.
The concluding talk
As it’s given through this chapter – we would begin this effort with the attributes such as the scariest searching tool of today and finish our talk with the quite peaceful conclusion saying that the Shodan is not that bad at all. So, what is the truth? The fact is this tool would obtain the tasks depending who would use it for which purposes. If it’s in the hands of good people – it would be good. On the other hand, it would become our nightmare. In conclusion, we would highly recommend to all researchers, scientists and engineers to work hard on the next generation Shodan that would offer us much safer web environment.
References:
[1] Djekic, M. D., 2017. The Internet of Things: Concept, Application and Security. LAP LAMBERT Academic Publishing.
[2] Djekic, M. D., 2021. The Digital Technology Insight. Cyber Security Magazine
[3] Djekic, M. D., 2021. Smart Technological Landscape. Cyber Security Magazine
[4] Djekic, M. D., 2021. Biometrics Cyber Security. Cyber Security Magazine
[5] Djekic, M. D., 2020. Detecting an Insider Threat. Cyber Security Magazine
[6] Djekic, M. D., 2021. Communication Streaming Challenges. Cyber Defense Magazine
[7] Djekic, M. D., 2021. Channelling as a Challenge. Cyber Defense Magazine
[8] Djekic, M. D., 2021. Offense Sharing Activities in Criminal Justice Case. Cyber Defense Magazine
[9] Djekic, M. 2019. The Informant Task. Asia-Pacific Security Magazine
[10] Djekic, M. D., 2020. The Importance of Communication in Investigations. International Security Journal
[11] Djekic, M. D. 2019. The Purpose of Neural Networks in Cryptography, Cyber Defense Magazine
[12] Djekic, M. D. 2020. Artificial Intelligence-driven Situational Awareness, Cyber Defense Magazine
[13] Djekic, M. D. 2019. The Perspectives of the 5th Industrial Revolution, Cyber Defense Magazine
[14] Djekic, M. D. 2019. The Email Security Challenges, Cyber Defense Magazine
[15] Djekic, M. D. 2016. The ESIS Encryption Law, Cyber Defense Magazine
[16] Đekić, M. D., 2021. The Insider’s Threats: Operational, Tactical and Strategic Perspective. LAP LAMBERT Academic Publishing.
About The Author
 Milica D. Djekic is an Independent Researcher from Subotica, the Republic of Serbia. She received her engineering background from the Faculty of Mechanical Engineering, University of Belgrade. She writes for some domestic and overseas presses and she is also the author of the books“The Internet of Things: Concept, Applications and Security”and “The Insider’s Threats: Operational, Tactical and Strategic Perspective”being published in 2017 and 2021 respectively with the Lambert Academic Publishing. Milica is also a speaker with the BrightTALK expert’s channel. She is the member of an ASIS International since 2017 and contributor to the Australian Cyber Security Magazine since 2018. Milica’s research efforts are recognized with Computer Emergency Response Team for the European Union (CERT-EU), Censys Press, BU-CERT UK and EASA European Centre for Cybersecurity in Aviation (ECCSA). Her fields of interests are cyber defense, technology, and business. Milica is a person with disability.
Milica D. Djekic is an Independent Researcher from Subotica, the Republic of Serbia. She received her engineering background from the Faculty of Mechanical Engineering, University of Belgrade. She writes for some domestic and overseas presses and she is also the author of the books“The Internet of Things: Concept, Applications and Security”and “The Insider’s Threats: Operational, Tactical and Strategic Perspective”being published in 2017 and 2021 respectively with the Lambert Academic Publishing. Milica is also a speaker with the BrightTALK expert’s channel. She is the member of an ASIS International since 2017 and contributor to the Australian Cyber Security Magazine since 2018. Milica’s research efforts are recognized with Computer Emergency Response Team for the European Union (CERT-EU), Censys Press, BU-CERT UK and EASA European Centre for Cybersecurity in Aviation (ECCSA). Her fields of interests are cyber defense, technology, and business. Milica is a person with disability.


