By Pedro Tavares, Editor-in-Chief seguranca-informatica.pt
We are living in an age where ransomware continues to grow and the number of attacks has increased especially during the COVID-19 pandemic. Data encryption malware is an emergent threat evolving and changing its Tactics, Techniques, and Procedures (TTP) along the time.
In general, data encryption malware so-called ransomware is a type of malware that prevents victims from accessing their systems and demands ransom payments in order to regain access to the data. The affected systems include network assets, servers, backups, personal data, and so on.
In early ransomware versions – the 1980s, the ransom paid was paid via snail mail. Today the schema evolves an order sent via cryptocurrency (bitcoin) and credit card.
These kinds of attacks generally start via email, with social engineering campaigns in place, namely malspam, malvertising, and phishing schemas sent to a huge group of users every day.
Ransomware can be grouped into some categories, namely:
- Scareware: includes rogue security software and tech support scams.
- Screen lockers: freeze the system and a window is presented after login with payment details.
- Encrypting ransomware: the files are encrypted and a ransom must be paid to recover the data.
- Destructive ransomware: less common, it only aims to destroy systems.
Mediatic Ransomware
There is a collection of mediatic ransomware that has been made headlines due to their damage.
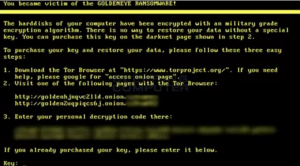
GoldenEye: One of the most well-known ransomware in the world is GoldenEye, which was responsible for a complete shutdown, crashing Ukrainian systems. The impact of this attack hit the banking networks, the system of the largest airport in the country, and the main electricity company. Three crucial points for society, which proved to be extremely vulnerable.
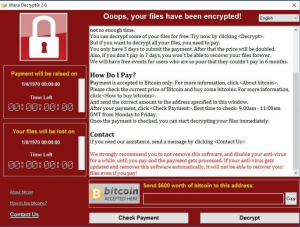
Wannacry: A cryptographic malware that hijacks and blocks files and folders promising to return them only by paying a ransom in bitcoins (virtual currency). This ransomware was based on a security breach and was largely responsible for an internet blackout. Criminals asked for $600 to unlock the content on each computer.
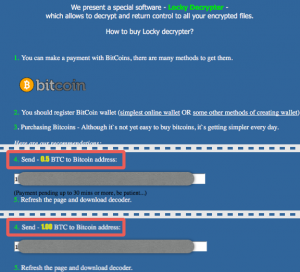
Locky: it encrypts files and holds them hostage for ransom. Locky was first discovered at the beginning of 2016 and immediately became one of the most significant malware threats in the wild. This ransomware was developed by the same hackers in charge of Dridex botnet, considered one of the largest botnet networks in the world.
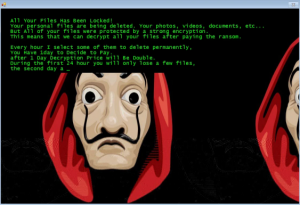
Jigsaw: it was inspired by the protagonist of the “Mortal Games” movie franchise. This attack begins with a salute, followed by a request for ransom. The malware encrypts computer files and gradually deletes them unless a ransom is paid to decrypt the files.
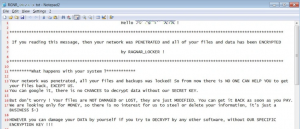
Ryuk: it’s specifically used to target enterprise environments. Ryuk is a modified version of Hermes ransomware. Ryuk ransomware is more lucrative than its predecessor. It targets large organizations and government agencies that end up paying up large amounts based on the exfiltrated information.
Ragnar Locker: This is one of the most recent pieces of ransomware. Ragnar Locker is a ransomware-type, designed not only to encrypt data but also to terminate installed programs (like ConnectWise and Kaseya) that are commonly used by managed service providers and various Windows services.
How to Prevent a Ransomware Attack
There is no perfect solution to prevent attacks of this nature, however, there is a set of good practices that can be applied in order to minimize the impact of data encryption malware. I can enumerate some of them below.
- Use live, active anti-virus which are regularly updated.
- Patch updates regularly. Update all software including operating systems, network devices, applications, mobile phones, and other software.
- Maintain a proper backup mechanism and made it mandatory.
- Regularly test the recovery function of backup and restore procedure and also test the data integrity of backups.
- Conduct simulated ransomware preparedness test.
- Install Microsoft Office viewers and always keep macros disabled.
- Limit end-user access to mapped drives and don’t enable file sharing.
- Don’t enable remote services. The organizations with RDP, VPN, proxies, and servers are to be provided with better IT Security standards.
Take home message: Implement effective security awareness training to improve cyber education and don’t download anything from unknown sources.
About the Author
 Pedro Tavares is a cybersecurity professional and a founding member of CSIRT.UBI and Editor-in-Chief of seguranca-informatica.pt. In recent years he has invested in the field of information security, exploring and analyzing a wide range of topics, malware, ethical hacking (OSCP-certified), cybersecurity, IoT, and security in computer networks. He is also a Freelance Writer.
Pedro Tavares is a cybersecurity professional and a founding member of CSIRT.UBI and Editor-in-Chief of seguranca-informatica.pt. In recent years he has invested in the field of information security, exploring and analyzing a wide range of topics, malware, ethical hacking (OSCP-certified), cybersecurity, IoT, and security in computer networks. He is also a Freelance Writer.
Segurança Informática blog: www.seguranca-informatica.pt
LinkedIn: https://www.linkedin.com/in/sirpedrotavares
Twitter: https://twitter.com/sirpedrotavares
Contact me: [email protected]