A study conducted by Recorded Future on PoC exploits shared online over the last year shows that social media is the main distribution channel.
Security experts at the threat intelligence firm Recorded Future have conducted an interesting study on the proof-of-concept exploits shared online (e.g. On Twitter, on forum linking to personal blogs, GitHub, or Pastebin) last year.
The PoC exploits are developed by threat actors and security experts to demonstrate the existence of s security flaw into a target system and how to exploit it.
In some cases, hackers publicly disclose PoC exploits to force a company to develop a patch to fix critical flaws in their products.
The research allowed the discovery of roughly 12,000 references to PoC exploits shared online since March 22, 2015, an amazing data is we consider that it represents a near 200 percent increase compared to the previous year.
According to the report, the majority of PoC exploits were spread via social media networks (97 percent of cases), mainly via Twitter, followed by Code Repositories (1.8 percent of cases). The choice is not casual, social media allow users to reach a wider audience instantly.
“Our research shows that POCs are disseminated primarily via Twitter, with users flagging POCs to view externally in a range of sources — code repositories (GitHub), paste sites (Pastebin), social media (Facebook and Reddit surprisingly), and deep web forums (Chinese and Spanish forums).” states the study.
| Source | Count | Rate |
| Social Media | 11,549 | 97% |
| Code Repository | 215 | 1.8% |
| Mainstream | 42 | 0.35% |
| None | 33 | 0.28% |
| Niche | 26 | 0.22% |
| Blog | 22 | 0.18% |
| Forum | 11 | 0.09% |
| Exchange | 4 | 0.03% |
| Malware/Vulnerability Technical Reporting | 2 | 0.02% |
| Paste Site | 2 | 0.02% |
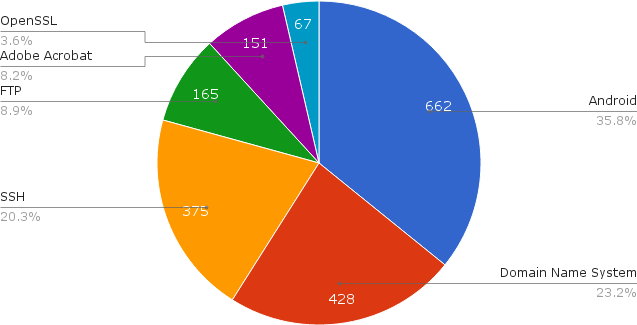
Which are the targets of the POC exploits?
Most targeted technologies are Android (35,8), DNS (23,2), SSH (20,3). The products being targeted are Android phones, Microsoft Windows 7 and 8, Microsoft Internet Explorer, Linux, GNU C Library (glibc), and Firefox.

Giving a look to the list of the most widely distributed PoC we can observe that the CVE-2015-7547 buffer overflow flaw is the one with the greatest number of PoC exploits. The flaw affects the GNU C Library and could be exploited by hackers to trigger a buffer overflow through malicious DNS response.
Other PoC exploits shared online are related to the CVE-2015-1635 and the CVE-2016-0051 in Microsoft Windows Server, and the CVE-2015-3456, aka the VENOM flaw, in the
The analysis of the top 10 vulnerabilities discussed around POCs suggests a huge focus on Linux boxes and Microsoft Windows Servers, clearly due to their diffusion.
“According to open source intelligence (OSINT) collections by Recorded Future, here are some of the most linked to POCs over the last year:”
- CVE-2015-3456 (Venom): https://marc.info/?l=oss-security&m=143155206320935&w=2
- CVE-2015-2370 / MS15-076: https://www.exploit-db.com/exploits/37768/
- CVE-2016-0051: https://github.com/koczkatamas/CVE-2016-0051
- CVE-2015-1635 / MS15-034: http://pastebin.com/raw/ypURDPc4
“Researchers and malicious actors focus their time on developing POCs for Web servers/services and consumer products in the Microsoft Office suite, Microsoft IE, etc. These are used across the commercial, consumer, and government sector widely,” explained Nick Espinoza from Recorded Future.
Enjoy the report, it is full of precious data.