By John Riley III, Cyber Business Development, Alan B. Levan | NSU Broward Center of Innovation.
“Securing the software delivery pipeline is as important as securing the software that is delivered.”1 – Gartner
In today’s increasingly digital world, software is the backbone of business operations, from customer-facing applications to internal processes. However, the rapid growth of software development has also made organizations more vulnerable to security threats. To counteract this, companies must prioritize a Secure Software Development Lifecycle (SSDLC) to ensure their software remains resilient in the face of evolving threats.
A Secure Software Development Lifecycle strategy is essential for organizations that want to build and maintain secure software applications. It not only helps prevent security vulnerabilities, but also offers numerous benefits in terms of cost savings, regulatory compliance, customer trust, and competitive advantage. By making security an integral part of the development process, organizations can better protect their software and the data they process.
The Necessity of SSDLC
A Secure Software Development Lifecycle is a systematic and methodical approach to developing software with security at its core. It encompasses every phase of the software development process, from the initial design and coding to testing, deployment, and maintenance. Here’s why companies must make SSDLC an integral part of their software development process:
- Early Vulnerability Detection: SSDLC encourages identifying and addressing security vulnerabilities at an early stage. This proactive approach minimizes the risks of costly security breaches and data leaks down the line.
- Regulatory Compliance: Various industries and regions have stringent regulations concerning data privacy and cybersecurity. Implementing an SSDLC ensures compliance with these regulations, helping companies avoid hefty fines and legal consequences.
- Risk Reduction: A robust SSDLC strategy significantly reduces the risk of security incidents. By integrating security measures from the start, organizations can better protect their reputation and sensitive data.
- Cost-Efficiency: Addressing security issues post-deployment can be expensive and time-consuming. With SSDLC, the cost of fixing security vulnerabilities is drastically reduced, as issues are detected and rectified during the development process.
- Faster Development: Contrary to the belief that security measures slow down development, SSDLC can expedite the process by reducing the time spent on security-related issues and rework.
Security Concerns in Software Deployment
When deploying new software into their environments, companies must be aware of a range of security concerns:
- Data Security: Protecting sensitive data is paramount. Companies should implement encryption, access controls, and data retention policies to safeguard user information.
- Authentication and Authorization: Ensure that users can only access the parts of the software and data they are authorized to. Weak authentication and authorization processes can lead to unauthorized access.
- Code Vulnerabilities: Unsecured code can provide entry points for attackers. Regular code reviews, static and dynamic analysis tools, and best coding practices are essential.
- Third-Party Components: Many applications use third-party libraries and components. It’s crucial to keep these up to date and assess their security posture.
- Patch Management: Timely application of security patches is vital to address vulnerabilities in software components and operating systems.
- Secure Configuration: Ensure that servers, databases, and other system components are configured securely. Insecure configurations can expose the software to attacks.
- Network Security: Protect the software from network attacks by employing firewalls, intrusion detection systems, and monitoring network traffic.
- User Training: Educate users and employees about security best practices and potential threats to minimize the risk of social engineering attacks.
- Incident Response Plan: Develop a robust incident response plan to address security incidents swiftly and effectively. Plan to review quarterly and run exercises to test knowledge and implementation of the plan.
- Secure Development Environment: Keep the development and testing environments secure to prevent the introduction of vulnerabilities during development.
The implementation of a Secure Software Development Lifecycle (SSDLC) is critical for companies deploying new software into their environments. A well-executed SSDLC strategy not only enhances security but also ensures regulatory compliance, reduces risks, and ultimately saves costs. As businesses increasingly rely on software, prioritizing security from the start is a non-negotiable requirement in today’s digital landscape.
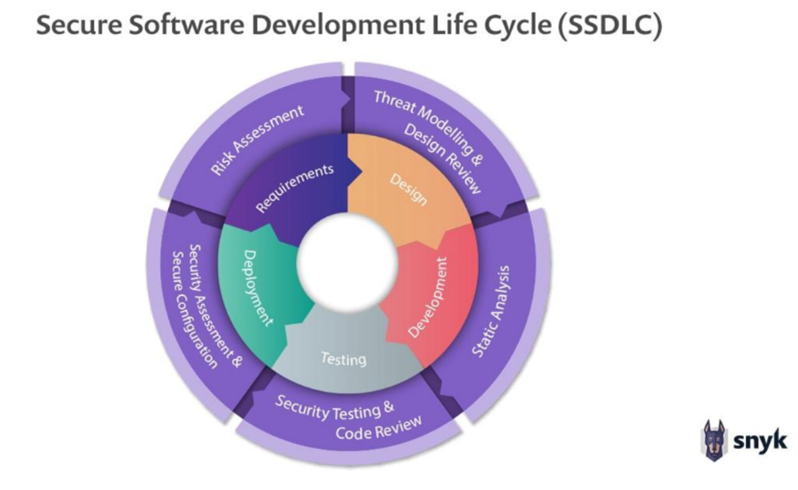
Phases of SLDC
- Requirements Gathering and Analysis: In this phase, the project team collaborates with stakeholders to understand their needs and requirements. The goal is to create a detailed and comprehensive set of software requirements that will guide the development process.
- Planning: Based on the requirements, the project team creates a detailed project plan. This plan includes timelines, resource allocation, budgeting, and a breakdown of tasks. It provides a roadmap for the entire project.
- System Design: This phase involves designing the system architecture. It includes defining the software’s structure, components, interfaces, and data. The result is a high-level design that serves as a blueprint for the development team.
- Implementation (Coding): During this phase, developers write the actual code for the software, following the design specifications. This is where the software is built according to the requirements and design.
- Testing: Testing is a crucial phase where the software is evaluated to identify and fix defects and ensure it meets the specified requirements. It includes various types of testing, such as unit testing, integration testing, system testing, and user acceptance testing.
- Deployment: Once the software has been thoroughly tested and is ready for release, it is deployed into the production environment. This phase may involve data migration, setting up the infrastructure, and making the software available to users.
- Maintenance and Support: After deployment, the software enters the maintenance phase. This involves addressing issues, releasing updates, and providing ongoing support to users. Maintenance may include bug fixes, performance enhancements, and the addition of new features.
In the dynamic landscape of modern business, the importance of a Secure Software Development Lifecycle (SSDLC) cannot be overstated. With the rapid expansion of software development comes an increased vulnerability to security threats. A well-executed SSDLC not only fortifies against potential breaches, but also yields substantial benefits in terms of cost efficiency, regulatory adherence, customer confidence, and competitive edge. By integrating security seamlessly into each phase of development, organizations fortify their software and shield the data they manage. As reliance on software continues to grow, initiating projects with security in focus is an indispensable practice. This article encourages every cybersecurity professional to champion the adoption of SSDLC within their organizations, ensuring a robust and resilient software ecosystem for years to come. The phases of SSDLC, from Requirements Gathering to Maintenance and Support, provide a comprehensive roadmap for safeguarding software integrity and security.
About the Author
 John Riley III, Cyber Business Development, Alan B. Levan | NSU Broward Center of Innovation
John Riley III, Cyber Business Development, Alan B. Levan | NSU Broward Center of Innovation
With a career spanning over two decades in the software application industry, John Riley III brings a wealth of experience to the table. His journey has been marked by a steadfast commitment to understanding and solving customers’ challenges and a strong belief that collaboration with like-minded professionals is the key to success.
John’s Specialties and Skills encompass a wide array of expertise, making him a versatile leader in various domains:
In the realm of technology adoption, he excels in End User Adoption, ensuring that technological innovations seamlessly integrate into user workflows. He navigates the intricate landscape of SaaS, guides organizations through the complex process of Digital Transformation, and harnesses the power of Digital Twins for enhanced insights.
John’s knack for Business Process Alignment and his experience in DOD | Military give him a unique perspective on optimizing operations. He’s a master of Pre-Sales, crafting strategies that drive success, and a seasoned hand in Business Development.
In the world of software, John shines in Enterprise Software implementation and the cutting-edge arena of Enterprise Blockchain Platforms. He’s well-versed in AI/ML and its applications and excels in Strategy development. His commitment to Innovation is unwavering, and he’s skilled in building Knowledge Graphs for informed decision-making. John also lends his expertise to organizations through Consulting, guiding them through complex challenges and ensuring robust Cybersecurity practices.
John’s career trajectory includes a significant tenure in the Oracle Applications space, with a focus on consulting services and education, assisting companies in software implementations, business process changes, and user adoption education.
Most recently, he held the position of VP of Business Development at Kilroy Blockchain and assumed the role of organizer for two Blockchain Meet-Up groups in West Palm Beach, FL. Presently, he is the Co-founder and CEO of C-N-C Blockchain Advisory.
Notably, John Riley III is a US Marine War Veteran, with a distinguished service record during Desert Shield/Desert Storm, underscoring his unwavering commitment to duty and leadership.
John Riley III can be reached online at ([email protected]) and at our company website https://www.levancentercyber.com/


