By Milica D. Djekic
The mechatronics systems are a common part of the industrial control systems (ICS) or – in other words – these two assets serve in many control engineering applications. The mechatronics systems exist many years back and they are only the phase in a development of control systems. In addition, they are a synergy of control, mechanical, electrical and computer systems. Through this modern time – these infrastructures are correlated with the web technologies and frequently use the internet to communicate with each other. Here, how over the control engineering and mechatronics we would come to an Internet of Things (IoT) concept. In this chapter, we would discuss how mechatronics paradigm has become the part of control engineering solutions and why it’s important to understand its IoT side in order to stay cyber safe.
What are the mechatronics systems?
“Mechatronics” is a quite recent concept that would mainly affect the control engineering solutions. It’s commonly correlated with the robotics, but nowadays it’s more than a robotics. Basically, it’s about smart systems which would use many sensors and measuring devices in order to make an intelligent decision. The mechatronics is about the mix of control, mechanical, electrical and computer systems. Those solutions would so commonly get exposed to the internet and for such a reason they would deal with the next phase of their development and deployment and that’s the IoT stage. It’s well known that a number of sensors and the similar gadgets could improve any control system – especially if its designer has developed the smart control algorithm. The real technological intelligence would usually get connected with the adaptive systems getting the ability to deal with the unknown environment so intelligently. Right here, we would illustrate how some mechatronics system appears and how it could get applied in an industry. This illustration is provided through a Figure 1 as follows.

Figure 1. The mechatronics asset being used in an industry
Next, we would want to deal with some of the bases of a mechatronics concept. For instance, it’s quite clear that these systems would use mechanical devices such as gears, frames, metal objects, robotics arms and so on. Also, they would get dependable on a power supply making these solutions dealing with the electrical systems. Finally, their control system would use the algorithm being saved within some computing unit and that’s how such a solution would apply the commands and follow the instructions. The block diagram of such a mechatronics system is given in a Figure 2 as follows.
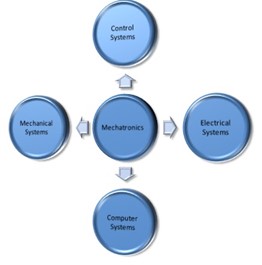
Figure 2. The mechatronics as a concept
Finally, we would realize that this concept is a consequence of the long-term evolutional process that would improve our technological advancements. The role of the mechatronics systems is to make a solid basis to an industry as well as some home applications. The mechatronics is a quite complicated branch of technology and people dealing with its design, research, development and maintainace must be highly skillful. In such a case, it’s vitally important to understand all the simple terms of that technology in order to deal with so at a more holistic level. Indeed, this sort of industry would require a multidisciplinary team of experts who would so deeply cope with their areas of expertise and make these systems work so accurately and intelligently.
The Shodan and the mechatronics solutions
Through this book’s chapter mainly dealing with the practice – we would try to discuss how mechatronics systems could get correlate with one of the scariest search engines of today. In addition, it’s quite clear that crawler is a Shodan and right here – we would attempt to explain how we could use such a tool to get familiar with the mechatronics systems. As we would suggest through the title of this chapter – the purpose of this segment is to indicate to all the weaknesses of mechatronics systems being exposed to the web as well as suggest some of the hacking strategies. So, let’s start with the Shodan being our top crawler for the world of advanced technology. The first step of this research would get given in a Figure 3 as follows.

Figure 3. The Shodan’s environment to industrial systems
As it’s illustrated in a Figure 3 – the Shodan would offer us several featured options that could lead us to sections being ICS, Databases and Video Games. Right here, we would be deeply interested into the ICS as something which would rely on the mechatronics principles. As it’s well known – for a required keyword, the Shodan would return us a certain IP address offering us an opportunity to try to exploit such an asset. For such a purpose, it’s necessary to get the adequate hacker’s tools. We have talked a bit more about such an operation through the previous chapter. Using that chapter – we have deeply explained how software such as the Advanced IP Scanner and Radmin could get used in looking for the vulnerabilities of those IoT solutions. Finally, even that chapter has served to us in a better understanding of all Shodan’s capacities being used either – for good or bad. Right here, we would illustrate through a Figure 4 what the next step in such a campaign could be.
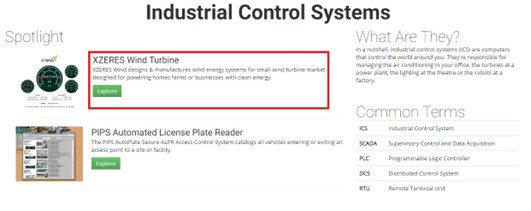
Figure 4. The Shodan’s ICS environment
As it’s illustrated via the Figure 4 – we would select the ICS being the wind turbines as a quite good case of mechatronics systems. It’s also important to mention that the embedded systems could also be the part of mechatronics systems depending which sort of computing unit is used for a system’s control. Further, the next stage in this explanation would be a click on the selected type of the wind turbines and through a Figure 5 – we would see how such an asset appears. The illustration is represented as follows.
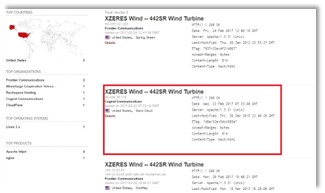
Figure 5. The wind turbines as a part of Shodan’s search
As you would see through the previous Figure – there would be many alternatives coping with the required criterion. The chapter before would illustrate us how we could hack an asset with the well-known IP address and authentication. In this case, we would deal with some IP address and no authentication, so our task would get a bit complicated. The majority of hackers would firstly try to do some guessing in order to break into a system. Also, there are some tools on the black market that would offer a chance to obtain someone’s login details. Finally, we would realize that some of the IoT systems would not use any protection, so the hackers would so easily get an access to that asset.
How to remain cyber safe?
In this modern time, it’s quite challenging to remain cyber safe. Through this learning material – we would discuss how it’s simple to organize some hacking attack, so the question here would be if there is any chance to avoid a cyber breach. The fact is these sorts of attacks are happening anywhere and anytime and the point is that you would accept that your IT asset got breached or not. As we said – it’s something that is occurring constantly, so we would strongly recommend taking care about your cybersecurity and try to follow the best procedures and policies in order to maintain the risk at an acceptable level. Also, it’s significant to say that the good defense is about the proper risk management and the point is not how to avoid the attack, but rather how to respond to so. Finally, it’s about the never-ending competition between the force of defense and the force of attack.
The conclusions
At the end, we would show through this book’s chapter how it’s possible to exploit even mechatronics systems being the part of ICS and so commonly the entire critical infrastructure. The mechatronics is only one of the stages in a development and deployment of our technological improvements and today – it’s combined with the IoT technology. The purpose of this chapter is to indicate that even mechatronics systems got some weaknesses and the task of an expert’s community should be to try to overcome those vulnerabilities and make much stronger and more reliable solutions.
About The Author
 Milica D. Djekic is an Independent Researcher from Subotica, the Republic of Serbia. She received her engineering background from the Faculty of Mechanical Engineering, University of Belgrade. She writes for some domestic and overseas presses and she is also the author of the books “The Internet of Things: Concept, Applications and Security” and “The Insider’s Threats: Operational, Tactical and Strategic Perspective” being published in 2017 and 2021 respectively with the Lambert Academic Publishing. Milica is also a speaker with the BrightTALK expert’s channel. She is the member of an ASIS International since 2017 and contributor to the Australian Cyber Security Magazine since 2018. Milica’s research efforts are recognized with Computer Emergency Response Team for the European Union (CERT-EU), Censys Press, BU-CERT UK and EASA European Centre for Cybersecurity in Aviation (ECCSA). Her fields of interests are cyber defense, technology and business. Milica is a person with disability.
Milica D. Djekic is an Independent Researcher from Subotica, the Republic of Serbia. She received her engineering background from the Faculty of Mechanical Engineering, University of Belgrade. She writes for some domestic and overseas presses and she is also the author of the books “The Internet of Things: Concept, Applications and Security” and “The Insider’s Threats: Operational, Tactical and Strategic Perspective” being published in 2017 and 2021 respectively with the Lambert Academic Publishing. Milica is also a speaker with the BrightTALK expert’s channel. She is the member of an ASIS International since 2017 and contributor to the Australian Cyber Security Magazine since 2018. Milica’s research efforts are recognized with Computer Emergency Response Team for the European Union (CERT-EU), Censys Press, BU-CERT UK and EASA European Centre for Cybersecurity in Aviation (ECCSA). Her fields of interests are cyber defense, technology and business. Milica is a person with disability.


