Researchers from Cisco Talos team spotted a new strain of malware that leverages PowerShell scripts to fetch commands from DNS TXT records.
Malware researchers at Cisco Talos have published a detailed analysis on a targeted attack leveraging a weaponized Microsoft Word document that is spread in spam emails as an attachment.
The malicious code used in the attack is based on Windows PowerShell scripts, the RAT communicates with the C&C infrastructure through Domain Name Service.
The attacker used DNS as communication channel because DNS requests are never blocked on corporate networks.
The malicious code was first spotted by the security researcher (@simpo13) who reported his discovery to the Talos team because he noticed the code references Cisco’s SourceFire security appliances with the encoded text, “SourceFireSux.”
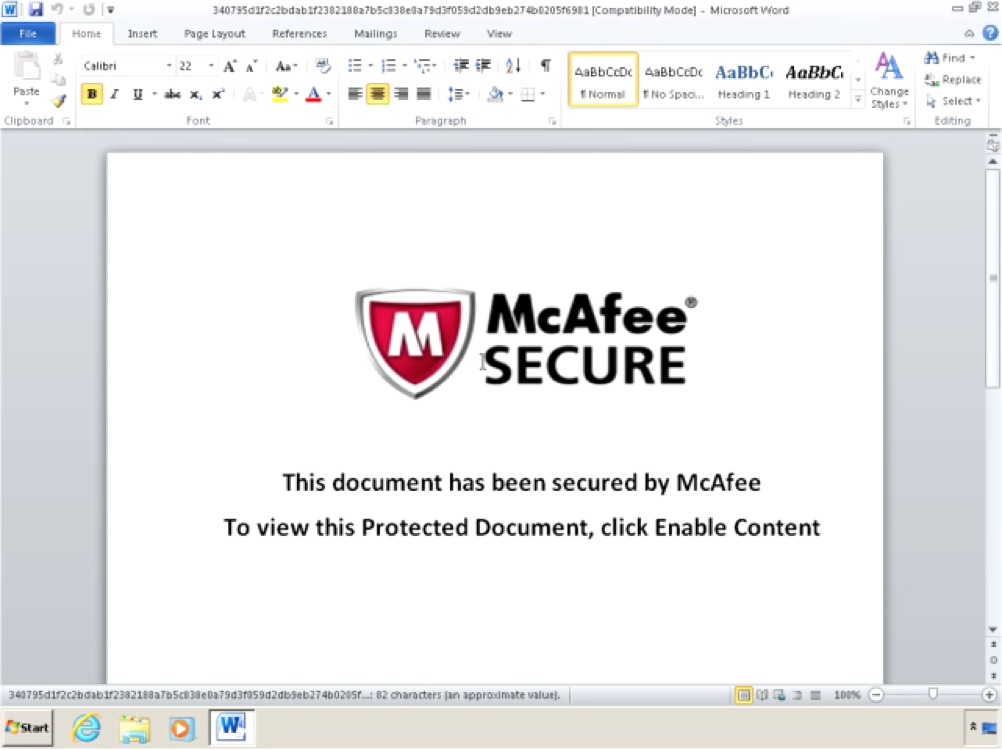
Attackers used a social engineering trick in order to trick victims into opening the malicious Word document.
“Interestingly, the Word document was made to appear as if it were associated with a secure email service that is secured by McAfee.” reads the blog post published by Talos. “This is likely an effective way to increase the odds of the victim opening the file and enabling macros as McAfee is a well known security vendor and likely immediately trusted by the victim. The document informs the user that it is secured and instructs the user to enable content.”

When the victim opens the document the multiple-stage infection starts with the execution of Visual Basic for Applications macro to launch PowerShell commands to install the backdoor onto the machine.
“The hash listed in the Pastebin led us to a malicious Word document that had also been uploaded to a public sandbox,” continues the Talos team. “The Word document initiated the same multiple-stage infection process as the file from the Hybrid Analysis report we previously discovered, and allowed us to reconstruct a more complete infection process.”
The VBA script unpacks a compressed and obfuscated second stage of PowerShell, which determines the PowerShell version installed on the system, then it adds entries to the Windows Registry and starts a third stage with a PowerShell script that acts as a backdoor.
In case the user does have administrative access, the installer PowerShell adds the backdoor to the Windows Management Instrumentation (WMI) database to gain persistence on the infected system after the reboot.
Once established the backdoor, in the stage 4 of the attack, the malicious code periodically makes DNS requests to one of the domains hard-coded into the script.
The requests retrieve TXT records from the domain that contain PowerShell commands that are directly executed by the infected system. It is important to notice that the code retrieved through the DNS requests but never written to the local system. This “fourth stage” script is the actual remote control tool used by the attacker. “Stage 4 is responsible for querying the C2 servers via DNS TXT message requests to ask what commands to execute,” Edmund Brumaghin told Ars via e-mail. “If a command is received, it is then executed and the output or results of the command are communicated back to the C2 server. This basically gives the attacker the ability to execute any Windows or application commands available on the infected host.”
“Once this is completed, the STDOUT and STDERR output that was captured from the Windows Command Line processor earlier in Stage 4 is transmitted using a “MSG” message. This allows the attacker to send commands to be executed directly by the Command Processor and receive the output of those commands all using DNS TXT requests and responses.” reads the analysis. “This communication is described in greater detail in the following section. Below is the DNS analysis and contents of the query request send from an infected system to the C2 server.”
The experts were not able to analyze the C2 infrastructure, the attack highlight the importance to inspect any network protocol to avoid problems.
“This malware sample is a great example of the length attackers are willing to go to stay undetected while operating within the environments that they are targeting.” concludes the Talos team. “It also illustrates the importance that in addition to inspecting and filtering network protocols such as HTTP/HTTPS, SMTP/POP3, etc. DNS traffic within corporate networks should also be considered a channel that an attacker can use to implement a fully functional, bidirectional C2 infrastructure.”