By Brendon McHugh, FAE & Technical Writer, Per Vices
Wireless technology has become ubiquitous in people’s lives and will continue to expand with Industry 4.0, smart cities, smart grids, and a whole plethora of internet of things (IoT) devices. As wireless standards continually evolve to accommodate changing user and device requirements, many issues are also becoming apparent, including the need to mitigate spectral challenges and issues related to cyber security, as well as appropriate responses to these incidents. In order for this, a flexible, reconfigurable, and programmable framework is required. A software-defined radio (SDR) is a radio communication system that is up to such a challenge.
In this article, we discuss the various threat incidents to machine-to-machine (M2M) and human-to-machine communications (HMC)/human-machine interfaces (HMI) in industrial and critical infrastructure– so-called industrial internet of things (IIoT). This includes cyberattacks such as sniffing, spoofing, replay attacks, and various others, which can threaten the various wireless devices in these settings. Other incidents occur in the electromagnetic (EMS) itself, including jamming, co-channel interference, and various other spectral issues. SDRs are capable of monitoring, detecting, and protecting wireless communication as well as being able to locate the origin of interference and alert of any communications failures.
Basic overview of M2M/HMC/IIoT Communications
In recent years, research on wireless systems that link with other devices has grown rapidly in an effort to replace traditionally wired systems while expanding the use of wireless technology. One such example is the Industrial Internet of Things (IIoT), used in areas like manufacturing, energy, transportation, agriculture, and more; essentially a wireless system of automation, learning, and sensor technology working together in order to provide smooth collaboration between critical systems. M2M IIoT technologies are being used by industrial and manufacturing organizations as they become more flexible in capabilities while increasing productivity. Implementing M2M solutions can yield benefits in terms of time and cost savings, operational efficiency gains, and optimized performance from key remote plants or other assets, whether it’s maintaining machines and plants installed across the globe from a central point, scanning data from distant outstations and mobile applications, or controlling plant-wide processes.
Unlike in the past, when factories required personnel to actively check the operation of each system, today’s manufacturing organizations are all focused on M2M and HMC/HMI combined with the Industrial Internet of Things (IIoT). Advanced sensors and actuators are used in M2M technologies to monitor a machine’s overall status and performance. The technology automatically conveys vibrations, temperature, pressure fluctuations, and other signals of mechanical failure to other linked devices, helping personnel to discover and handle issues sooner. Companies can deliver all preventative maintenance chores to protect the equipment’s longevity and ensure effective functioning since M2M-linked devices can notice warning signals and report problems practically instantaneously. Furthermore, these technologies aid in improving machine performance and productivity.
Often, microcontrollers are used to control input and output (from sensors, actuators, etc) as they communicate through cellular, Wi-Fi, and various other IEEE 802.1 standards. 5G and Time-sensitive networking (TSN) are also becoming more popular as mobility becomes more important for IIoT devices. Moreover, satellite communications for GPS/GNSS receivers embedded in transportation systems used in IIoT are becoming a requirement.
While various security features do exist in these standards, there is still high susceptibility to cyber and EMS threats, both intentional and unintentional, and so, examining, monitoring, and safeguarding IIoT devices is becoming increasingly critical.
Cyber and RF Attack Vectors
As discussed, a number of methods, technologies, and protocols for sending data or voice wirelessly between people, M2M, and/or HMC/HMI exist. However, these systems are susceptible to various cyber and RF threats. Commonly referred to as attack vectors, vulnerabilities of complex wireless systems such as those used in IIoT, are conducted through attacking hardware (radio frontend (RFE), time boards, sub-system microcontrollers/PLCs, etc.) and software/firmware used in devices (APIs, Ethernet cards/NICs, FPGA, ASICs, CPUs, Servers, etc.) as shown in Figure 1.
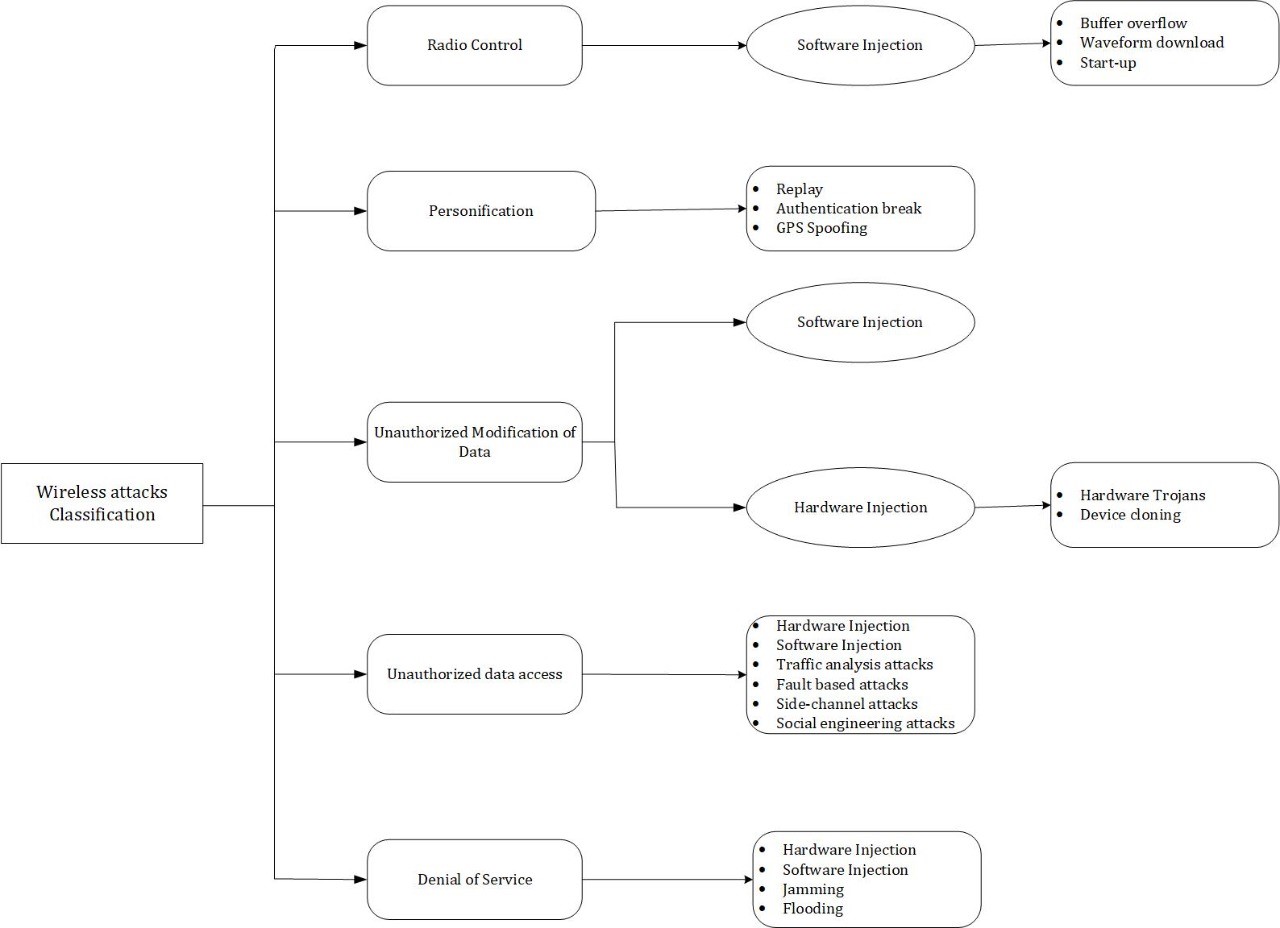
Figure 1: Cyber threats and RF attacks classification
While numerous methods exist for ensuring networks are secured from cyber threats, via device identification and access control, authentication encryption, distributed denial of service (DDoS) protection, and firewalls, it’s becoming increasingly important to fend off RF-related attacks and spectral issues as the RF spectrum becomes increasingly congested.
RF EMS threats, issues, and incidents are numerous in IIoT settings. For example, numerous technologies in IIoT operate in the 2.4 GHz band, causing co-channel overlapped operation and hence facing severe cross-technology co-channel CCI. Another example is intentional jamming, such as a denial-of-service (DoS) attack where transmission capabilities are blocked from either the receiving or the emitting end. Such attacks affect the availability of information/data flow from IIoT devices. Of course, numerous other RF attacks are possible, including spoofing, replay attacks, and eavesdropping, to name a few.
SDRs for M2M/HMC
SDRs are also becoming more common for use in IIoT settings as they can be used as a gateway for connecting numerous wireless devices using various wireless protocols, and their associated tuning frequencies, modulation schemes, and so on. Such interoperability is made possible by an SDR’s reconfigurable and flexible nature.
A typical SDR system has an analog front-end and a digital back-end. The analog front-end handles the transmit (Tx) and receive (Rx) functions of a radio communication system. Signals are translated from one domain to another using analog-to-digital converters (ADCs) and digital-to-analog converters (DACs). Once in the digital domain, signals enter an FPGA with onboard DSP capabilities for modulation, demodulation, upconverting, downconverting, and data packetization over Ethernet optical links. It’s also possible to implement various security features on the FPGA as part of the network stack, configure it for various modulation/demodulation schemes of radio protocols, etc.
An SDR can support a vast range of wireless technologies used in IIoT M2M, HMI, etc., and provides a compact, programmable, open-source, and full-duplex, solution for acting as a gateway to devices. Moreover, hardware designers can use the onboard FPGA to encode and decode the data for the various wireless standards, especially as open-source software/IP cores are becoming available. The FPGA also can also be used to encrypt or scramble the data to avoid transmitting in a way that is susceptible to RF attacks.
Examples of SDRs for M2M/HMC
With the deployment of 5G technologies and their use in IIoT, SDR technology is becoming critical, as these devices employ critical functions such as Network Function Virtualization (NFV). This not only enables a virtualized re-configurable environment of the SDR but also provides an opportunity to extend the overall network coverage, for instance, to mobile IIoT devices used in transportation networks, etc. For more global operations, such as international shipping and logistics, satellite communication with IIoT devices and gateways is also becoming critical. SDRs are also proving to be useful in this domain.
SDR technology has also become increasingly popular in the energy sector as it can aid with grid monitoring by allowing utilities and energy businesses to better monitor and regulate energy infrastructure or the electric grid for possible issues, as well as quickly adjust to changing conditions improving grid management efficiency and safety. It is widely utilized in the oil and gas industry for pipeline monitoring, asset tracking, and remote tank monitoring. SDR is also being utilized in renewable energy applications like wind farm monitoring and control, solar panel monitoring, and energy storage management.
How SDRs can Defend and Respond to Cyber/RF Threats and Incidents
Generally, today’s network security threats are becoming very sophisticated, so advanced solutions are needed to keep networks safe. Software-based solutions that have been used to protect network infrastructure are no longer good enough. One way to close this performance gap is to use reconfigurable software controlling hardware; in other words, the SDR paradigm. An SDR-based IIoT system combines the parallelism of hardware and the flexibility of software to make a network security solution that can be used in many different ways.
M2M communication security is required to safeguard the system from all forms of threats and infiltration. This includes means to prevent denial-of-service (DoS) attacks, transmission eavesdropping, routing attacks, floods, and data center security and access control. Physical attacks include inserting legitimate authentication tokens into a manipulated device, modifying or changing software, and environmental/side-channel attacks. A DoS attack is one that attempts to bring a system or network to a halt, rendering it unreachable to its intended users. SDRs are capable of protecting against these since they are networked devices and can be used as a barrier by monitoring data being received/transmitted at the SDR gateway (via FPGA end-point security, etc.) before being passed over to other network components (cloud servers in data centers, other IIoT devices, etc.), as well as alert of any suspicious activities.
One important aspect to consider is the use of SDR in the IIoT communication stack such as to self-heal, autoconfigure, and adapt the radio based on various EMS environments. For instance, there is always a chance that data communications could be harmed by radio frequency (RF) interference, which is unwanted energy in the form of emissions, radiations, or inductions. RF interference can affect a wide range of wireless technologies, including Bluetooth, Wi-Fi, and GPS. On the other hand, jamming occurs between a transmitter and a receiver. The purpose of radiofrequency or communication jamming is to prevent receiving or decoding, by disabling the opponent’s radio connection. To respond to these incidents, SDRs can reconfigure by various means, such as changing antenna directionality, changing center frequency, or using a redundant SDR gateway elsewhere in an IIoT network, thus mitigating RF spectral issues.
Other schemes for a secure SDR architecture incorporate an automatic calibration and certification unit (ACU), an radio security module (RSM), and a GNSS receiver for the position. The ACU is an SDR security threat mitigation method that monitors the output spectrum to enforce local rules. Such systems may set the necessary spectrum rules depending on the SDR’s location and spectrum configuration files. The SDR monitors spectrum laws globally (for example, spectrum configuration files). Even a malicious waveform in the SDR node can be stopped by the ACU. These modules are downloaded and executed by the RSM. User and device authentication, event and access logging, encryption, port disabling, and smart password and network key management are also important to consider.
Current research is also being done on SDRs used to prevent issues related to co-channel interference. As mentioned, one common IIoT protocol is Zigbee, however, it suffers from co-channel interference with WiFi sharing the same band. At 2.4 GHz, ZigBee uses offset quadrature phase-shift keying (O-QPSK) and direct-sequence spread spectrum (DSSS). But, each WiFi orthogonal channel has four ZigBee channels (2 MHz each), and thus, buried or blind terminals, and variations in channel sensing/response time still cause co-channel interference. To prevent this, matching local noise variance (LNV) is estimated after the interferers appear, and the Log-likelihood ratios (LLRs) are scaled using Local noise variance LLR scaling (LNV-SC). Figure 2 depicts the full interference detection and LLR scaling process. Adding LLRs to SDR software simplifies implementation. In an article published in IEEE Transactions on Vehicular Technology, researchers from Oulu University in Finland and Kaiserslautern University in Germany demonstrated how SDR can successfully mitigate the effects of multiple co-channel ZigBee interferers. The researchers found that SDR-based interference reduction may considerably improve ZigBee network performance in both lab and field settings.
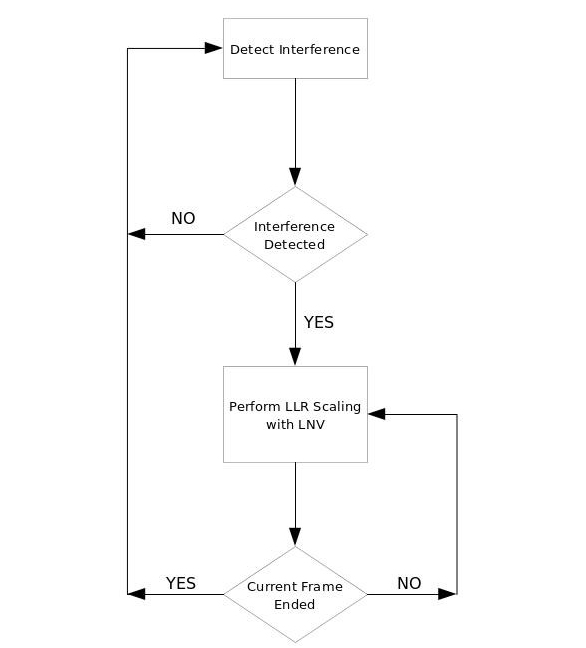
Figure 2: Flow chart of interference detection and LLR scaling (source: https://jwcn-eurasipjournals.springeropen.com/articles/10.1186/s13638-019-1512-3)
Moreover, an SDR can act as a spectrum monitoring device in IIoT networks only on factory floors using the common 2.4 GHz band (Wi-Fi, ZigBee, Bluetooth, etc) is critical for minimizing various co-channel interferers. Spectrum monitoring is a spectrum management technique that entails tracking a section of the radio frequency spectrum and storing the data for further study. The SDR can locate and isolate interfering devices by monitoring the spectrum, allowing the network to continue to function normally. In addition to spectrum monitoring and its function in interference mitigation, SDRs can identify possible sources of interference, locate them, and take actions to minimize them by continuously scanning the spectrum. Therefore, it can assist keep the IIoT network free of interference and running at maximum efficiency.
Conclusion
As discussed, wireless networks are prone to a large number of cybersecurity and spectral threats that if not handled and responded to in a timely manner, may lead to compromise in confidential/proprietary data and disruption in the networks. SDR-based systems are able to create a flexible and high-performance network security solution and respond to wireless RF communications vulnerabilities. This security layer solution overcomes traditional security solutions’ fundamental constraints and allows for real-time deployment of complicated protection functions. Because they are reconfigurable and enable high parallelism, FPGAs onboard SDRs are perfect for implementing this network security solution. With the ever-growing emergence of new wireless technologies, it is therefore imperative to adopt SDRs technology to ensure flexibility as well as security in IIoT M2M, HMC/HMI networks.
Per Vices has extensive experience developing and integrating highly secure SDRs for mission-critical applications, including that in industrial M2M communications, satellite communications, and other IoT applications. For more information, contact [email protected].
About the Author
 Brendon McHugh is a Field Application Engineer and Technical Writer at Per Vices Corporation. Per Vices has extensive experience in developing, building, and integrating software defined radios for CEMA operations. Brendon is responsible for assisting current and prospective clients in configuring the right SDR solutions for their unique needs, and possesses a degree in Theoretical and Mathematical Physics from the University of Toronto.
Brendon McHugh is a Field Application Engineer and Technical Writer at Per Vices Corporation. Per Vices has extensive experience in developing, building, and integrating software defined radios for CEMA operations. Brendon is responsible for assisting current and prospective clients in configuring the right SDR solutions for their unique needs, and possesses a degree in Theoretical and Mathematical Physics from the University of Toronto.
Brendon can be reached online at [email protected] and at our company website https://www.pervices.com/.


