A newly observed spam campaign is spreading a ransomware variant known as Sage 2.0 that is demanding a $2,000 ransom for the decryption key.
Sage 2.0 is a new ransomware recently spotted by security experts, it was first observed in December and not now it is distributed via malicious spam. Sage is considered a variant of CryLocker ransomware, it is being distributed by the Sundown and RIG exploit kits. The current campaign also leverages steganography to exfiltrate information about the victim’s PC inside a PNG image.

The malicious messages have a ZIP attachment that contains a Word document with malicious macros that once executed download and install the Sage ransomware. In some cases the experts also observed that the ZIP archive contains a .js file with the same functionality.
Duncan also explained that some of the malicious attachments are double-zipped and often the recipient’s name is part of the attachment’s file name.
“Emails from this particular campaign generally have no subject lines, and they always have no message text. The only content is a zip attachment containing a Word document with a malicious macro that downloads and installs ransomware. Sometimes, I’ll see a .js file instead of a Word document, but it does the same thing.” Duncan wrote in a report. “Often, the recipient’s name is part of the attachment’s file name. I replace those names with [recipient] before I share any info. A more interesting fact is the attachments are often double-zipped. They contain another zip archive before you get to the Word document or .js file.”
When the Sage 2.0 ransomware infects a Windows 7 machine it triggers the User Account Control (UAC) technology, this means that the user has to authorize its execution.
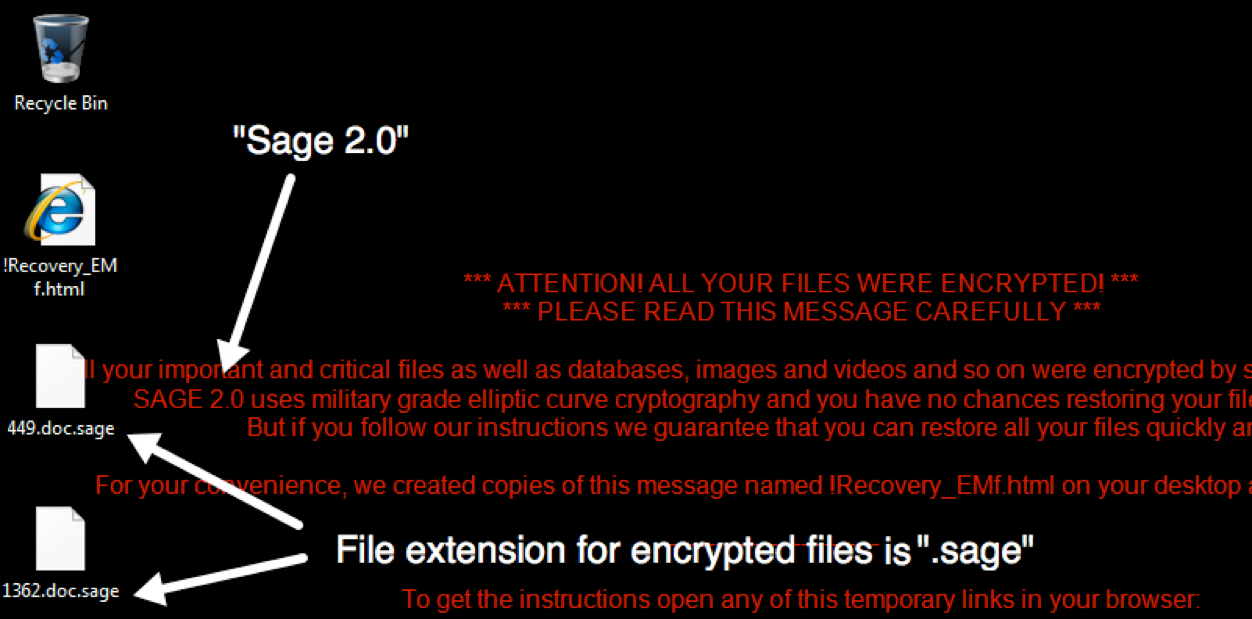
The ransom note includes instructions to pay an initial $2,000 ransom (or 2.22188 bitcoin). The ransomware uses a Tor-based domain with a decryptor screen.
In case of non-payment, the fee will increase over the time, but after a deadline reported on the Tor website the victim will be able possible to recover its files.
“The infected Windows host has an image of the decryption instructions as the desktop background. There’s also an HTML file with the same instructions dropped to the desktop. The same HTML file is also dropped to any directory with encrypted files. ‘.sage’ is the suffix for all encrypted files,” the security researcher explains.
The Sage ransomware maintains persistent on the infected machine by a scheduled task, and it’s stored as an executable in the user’s AppData\Roaming directory.
The Sage 2.0 ransomware generates post-infection traffic, like the CryLocker ransomware, in the form of HTTP POST requests. Sage traffic is different from CryLocker one because it is encrypted in some way.
“When the callback domains for Sage didn’t resolve in DNS, the infected host sent UDP packets sent to over 7,000 IP addresses. I think this could be UDP-based peer-to-peer (P2P) traffic, and it appears to be somehow encoded or encrypted,” added the security researcher.
“I’m not sure how widely-distributed Sage ransomware is. I’ve only seen it from this one malspam campaign, and I’ve only seen it one day so far. I’m also not sure how effective this particular campaign is. It seems these emails can easily be blocked, so few end users may have actually seen Sage 2.0. Still, Sage is another name in the wide variety of existing ransomware families. This illustrates how profitable ransomware remains for cyber criminals,” Duncan concludes.
[adrotate banner=”22″]