Did you know an organization is hit with a ransomware attack every 11 seconds?
As the global attack surface grows every day, and with everyone’s security perimeter now everywhere and anywhere data travels, being resilient to ransomware attacks takes on far greater significance.
The only way to create a truly resilient strategy against the growing onslaught of ransomware attacks is to go on the offensive by arming your data to protect itself.
Ensuring Data Integrity
First and foremost, that strategy depends on data integrity.
Data is the one constant in today’s complex, continually evolving technology ecosystem. It’s the currency of every organization and, increasingly, for ransomware attackers.
For criminals, the vast rivers of data streaming in and out of organizations every day represent potentially lucrative profits from as-yet untapped gold mines. The more confidential the data, the higher the monetary value that criminals place on those assets.
Let’s assume a bad actor penetrates your organization’s network and then exfiltrates every piece of data on that system. Even if you pay a ransom to unlock your data, how can you be sure of its integrity – that any or all of your data wasn’t altered in some way or corrupted?
Since you’re dealing with criminals, after all, there are no sure-fire guarantees. In fact, the odds are against you. A study by Cybereason found that, although 46% of companies pay a ransom to regain access to their data, some or all of it is corrupted.
With ransomware attacks rising, and insurers facing unprecedented losses from their cyber policies, carriers who protect organizations from attacks are hiking policy premiums to record levels, limiting coverage with more restrictive underwriting or canceling policies altogether. These policies are generally designed to cover the costs of an organization’s data recovery efforts after a breach, legal expenses if lawsuits are filed and restitution for attack-related losses incurred by customers. According to one industry survey, premiums for U.S. cyber insurance rose 25.5% between Q1-Q2 2021, outstripping all other insurance categories.
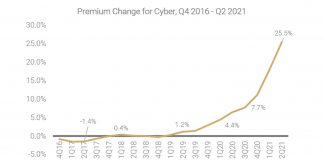
Source: Council of Insurance Agents & Brokers’ Commercial Property Casualty Market Report
But there are ways to ensure your data stays intact before, during or after a ransomware attempt – without having to rely on expensive cyber insurance for protection.
Elements of a Strong Resilience Strategy
Effective ransomware resilience strategies use a combination of data-centric security tools, policies, and people that can quickly detect and mitigate cyberattacks without interrupting the ebb and flow of business operations.
In mapping your strategy, consider these three important principles: confidentiality, integrity, and availability, also known as the CIA triad.
These three “legs” of the CIA stool are important management tools for several reasons. They can help decision-makers determine the value-add of new IT products and services. And they can help organizations evaluate whether they have the best policies, practices, and procedures in place to support their overall resiliency strategy.
Confidentiality refers to techniques and technologies that prevent access to information by unauthorized users (e.g., data encryption, classification, and access control).
Highly sensitive data may require extra security measures, such as storing on specified devices or segmented networks, securing isolated computers that are physically disconnected from a network, and maintaining hard copies.
Better yet, a recent technological breakthrough allows data to automatically think for itself and protect itself – no matter where it goes in the world, no matter who has it, where it’s stored or how many copies exist. Keyavi launched this innovation last year so that you – the data owner – always retain total control of your data, even if it ends up in criminal hands.
Up until now, the entire cyber market based its security approach and tools on one premise: that data can’t protect itself. It’s the one premise that ransomware criminals counted on – until now!
Our platform stops ransomware attackers cold by infusing data with intelligence, self-protection, and self-awareness.
A data owner can quickly revoke access to a Keyavi-enabled file or folder in near real-time, reassign access rights to someone else, or void access to every piece of intelligent data he or she owns. An owner can also allow or prevent data access by geolocation and pre-set access embargoes for authorized recipients on specific days and times. This smart data also reports back to its owner where it is, who has it, what device it’s on and when to protect itself anywhere it goes, no matter how it’s stored or for how long.
Integrity means maintaining the accuracy and trustworthiness of data throughout its lifecycle, either at rest or in transit. Only authorized users could access or alter that data.
Keyavi’s technology allows data owners to apply three different user rights to data files: read-only, collaborate, and full access.
Read-only access means just that: data can only be opened by an authorized recipient in a protected viewer but without the ability to edit, copy, paste, share or capture a screen.
With collaborate access, an authorized user can view and edit data in a protected viewer with limited options, such as copying, pasting, and saving modifications but not sharing or capturing a screen. Any changes to a file must also be saved in protected mode.
Full access allows an authorized recipient to view and edit data in the native application that was used to create it, such as Microsoft Word, Excel, or PowerPoint.
Availability refers to the readiness and accessibility of requisite IT systems, hardware, and software for authorized personnel.
At Keyavi, the availability leg applies to rules-based data access controls built into our technology, regardless of the hardware it resides on and the system with which it interacts. This technology allows data to open only for authorized users after it checks the recipient’s unique device characteristics for authenticity. Plus, we’ve made security controls and their integration into daily workflows easy to use.
Embedded policies in Keyavi’s technology also validate a person’s true geolocation along with other requirements to prevent data access in unauthorized locations by unapproved users. Our technology defaults to “safe and closed” to keep files protected even when offline, yet it also encrypts data even in transit. Organizations that prefer to tailor their policies to allow for varying levels of flexibility and risk mitigation for online and offline access have that option as well.
Administrators of Keyavi’s technology can set their own organizational policies with geolocation controls to allow data access at a company’s headquarters, satellite offices, remote employee home offices or specific locations for business travelers. In addition, the policy also provides the ability to blacklist geographies where data is never allowed to be opened.
Along with security capabilities, a technology’s ease of use is a major adoption factor for any organization evaluating a new IT product or service. Many security controls, when first being implemented, are often difficult for people to integrate and use. Employees who are uncomfortable adapting a new technology end up resisting it or bypassing it entirely.
Our development team headed that potential issue off at the pass by developing a lightweight Keyavi service that plugs in seamlessly with Microsoft Office and other applications so that workers can focus on the business at hand rather than struggle with unfamiliar and complicated new technology.
Expect the Unexpected
It’s been more than a year since the COVID-19 pandemic engulfed everyone everywhere. Yet IT departments still struggle to manage complex security and connectivity issues for workers in far-flung locations.
Every CISO I talk to never expected to support a remote workforce exposing organizational data on such a wide scale, which, in the process, created a massive attack surface. Cybercriminals continue to expand that attack surface by rapidly expanding malware capabilities, well-disguised phishing scams, ransomware assaults, and Distributed-Denial-of-Service attacks onto insecure digital devices, targeting remote workers unaware of the most basic security measures with unrelenting ferocity
As the shift to a hybrid remote- and in-office workforce becomes our new normal, Keyavi’s customers have learned that securing data doesn’t have to be either difficult or expensive.
Let’s assume, for example, that another crisis unfolds again on the world stage in the future. How would an organization maintain uninterrupted business operations within its resiliency framework?
Conceivably, core employees could evacuate to a “warm” site – a temporary headquarters equipped with office-ready accouterments for conducting business. Workers would be able to log into internet-enabled workstations using the applications they normally use and resume their daily routines. One downside to this approach is the often expensive cost of leasing office space and equipment to accommodate these employees.
Alternatively, Keyavi’s technology could enable every worker’s home or physical location to serve instead as a secure “warm” site, simply by having that employee log in as an authorized Keyavi user and register their new location. Not only is this a more cost-effective approach to battening down an organization’s security hatches quickly, it also secures an organization’s most sensitive data while ensuring the continuity of a remote worker’s productivity.
The upshot for any ransomware resiliency and data integrity strategy is that files no longer have to exist behind a firewall to be protected from cybercriminals or accidental loss. Now data itself IS the elegant, simple fortress. And Keyavi can help fortify any organization’s data security challenges as its resiliency strategy takes shape.
About the Author
 T.J. Minichillo is Keyavi’s chief information security officer (CISO) and VP of cyber threat & intelligence. He is nationally renowned cybersecurity and intelligence expert, helping to detect and thwart many of the world’s significant cyber threats. He has held strategic intelligence roles in financial services, the military, and energy, including global head of threat intelligence at both National Grid and Morgan Stanley, deputy director at Citigroup’s Cyber Intelligence Center, a chief cyber intelligence officer at Merrill Lynch, and senior intelligence special agent at the Department of Defense. Follow him on Twitter and LinkedIn.
T.J. Minichillo is Keyavi’s chief information security officer (CISO) and VP of cyber threat & intelligence. He is nationally renowned cybersecurity and intelligence expert, helping to detect and thwart many of the world’s significant cyber threats. He has held strategic intelligence roles in financial services, the military, and energy, including global head of threat intelligence at both National Grid and Morgan Stanley, deputy director at Citigroup’s Cyber Intelligence Center, a chief cyber intelligence officer at Merrill Lynch, and senior intelligence special agent at the Department of Defense. Follow him on Twitter and LinkedIn.


