By Douglas McKee, Executive Director, Threat Research, SonicWall
As Ferris Bueller once said, “Life moves pretty fast.” Most people, especially cybersecurity professionals, know the feeling. Minutes – sometimes seconds – matter in dealing with cybersecurity incidents. But how do you slow down time? What makes it so difficult to stay current or to prioritize what is on today’s agenda for a security operations center? It’s all in the minor details.
Parents can often recognize this instinctively. If your son or daughter wakes up one morning and you ask them, “How did you get home last night?” And they respond with, “I hitched a ride with a complete stranger,” a protective parent may gasp with surprise and concern. However, if the response has more details such as, “I took an Uber at 3 a.m. from my friend’s house, because I wanted to get home safely,” the same protective parent could react differently and prioritize the conversation accordingly.
On October 3, Daniel Stenberg Posted on X about a new “High” vulnerability in the curl ecosystem that would be publicly disclosed on October 11. Due to the popularity of both curl and Daniel’s social media influence, the cybersecurity world exploded with anticipation of a highly impactful and severe security issue; however, the post provided very few details about the actual issue.
The Windup
Daniel’s initial post on X sparked many questions, some of which people were not afraid to ask on X.
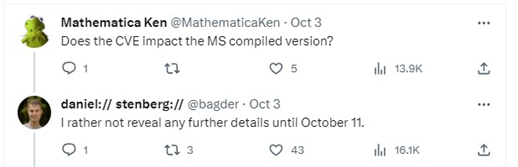
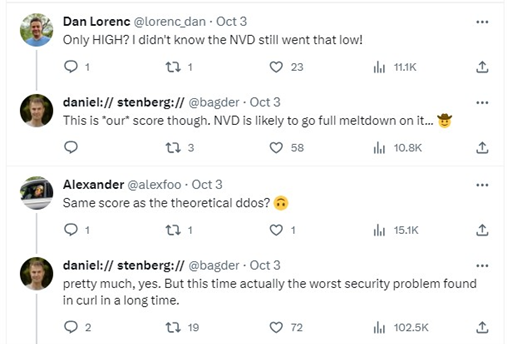
Phrases such as “likely to go full meltdown” and “worst security problem found in curl in a long time” coupled with resistance to provide any additional detail, sent media outlets and security experts writing articles about how this vulnerability would be the next big security concern for the computing world. It’s also important to note the context around the term “High” in regard to the National Vulnerability Database (NVD). From a standard scoring perspective, a “High” vulnerability has a CVSS score of 7.0-8.9.
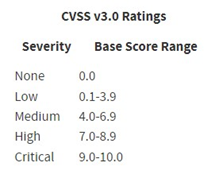
This is important since there is a precedent that “meltdown” level vulnerabilities are typically 9.0 or above, hence the “Critical” rating. This means there is a potential conflict in the minor details, but in our culture, often the mismatch will be ignored for a more severe outcome.
The Details
On October 11 as promised, the details of the vulnerability were made public, and the world was set on fire, but in a different manner than one may have expected.

It’s important to take a moment to acknowledge the main lesson learned from the release is the absolute professionalism and care Daniel Stenberg took in addressing this issue. If every vendor and open-source project followed his example, we would have a more secure computer world without question. A vulnerability was discovered and reported by a security researcher on a highly impactful platform, and it was patched in a timely manner with full transparency on the issues and how it was addressed, before, to the best of the community’s knowledge, any active exploitation had occurred. More simply put – the process worked flawlessly.
What did the release say?
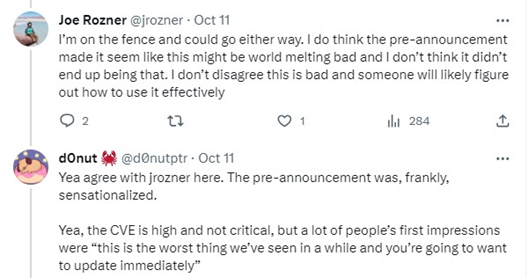
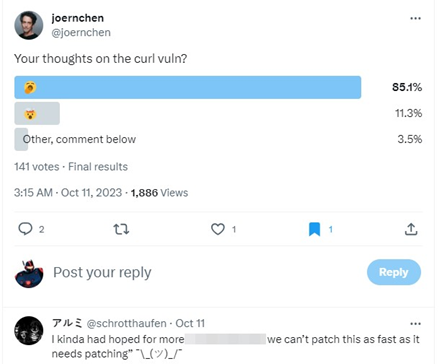
In nutshell, the published details revealed a memory corruption vulnerability in a large number of installed versions of both curl and libcurl. That exploitation required a special set of conditions to be true. Instead of the main conversation being about the technical details of the vulnerability, a conversation about the hype which surrounded the vulnerability took center stage. Why? While it was clearly stated in the initial messaging the issue was a “High” severity bug, the extreme language provided a false sense of a critical issue.
Officially, at the time of writing NVD hasn’t published a CVSS score indicating an official “High” vs. “Critical” rating. Some researchers have taken the details and predicted a score which has varied from a 7.5 to an 8.8 rating, both of which are high ratings. Therefore, the details surrounding the exploitation requirement of the vulnerability indeed confirmed a “High” level vulnerability and not a critical vulnerability, however these details were originally left to the imagination of the reader.
The Impact of Change
If the vulnerability is patched and the disclosure information is accurate, does it matter? The problem with overhype is it often causes a reaction or change in prioritization. Cybersecurity is already overwhelmed with events and starving for resources to address them. This dictates that prioritization of actions is the most important task for any organization. What risks are the highest risk right now and how do I address them? While sometimes the cost of change is minimal, at other times it’s a cost that can’t be afforded.
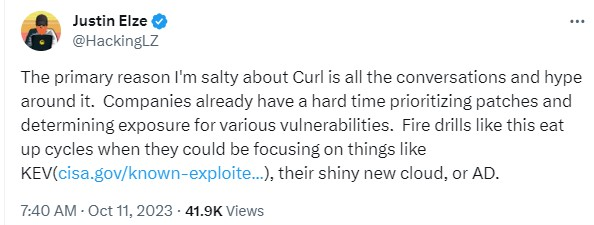
It is imperative that security researchers continue to responsibly disclose vulnerabilities to closed and open-source projects. Transparency of these vulnerabilities along with patches (as well done by the curl project) is the only way for defenders to have the necessary information required to defend our ever growing technology stack. It is also our responsibility to keep a factual, data driven, non-emotional response to these events, focus on the details and work together to responsibly use the resources we have at our disposal.
So, the next time “life comes at you pretty fast,” it pays dividends to “stop and look around once in a while.” It helps in making sure your team focuses your resources and efforts on the most critical and urgent issues that pose the greatest threat to your organization by paying attention to the minor details.
About the Author
 Douglas McKee is the Executive Director of Threat Research at SonicWall where he and his team focus on identifying, analyzing, and mitigating critical vulnerabilities through daily product content. He is also the lead author and instructor for SANS SEC568: Combating Supply Chain Attacks with Product Security Testing. Doug is a regular speaker at industry conferences such as DEF CON, Blackhat, Hardware.IO and RSA, and in his career has provided software exploitation training to many audiences, including law enforcement. His research is regularly featured in publications with broad readership including Politico, Bleeping Computer, Security Boulevard, Venture Beat, CSO, Politico Morning eHealth, Tech Republic, and Axios. Douglas can be reached at [email protected]
Douglas McKee is the Executive Director of Threat Research at SonicWall where he and his team focus on identifying, analyzing, and mitigating critical vulnerabilities through daily product content. He is also the lead author and instructor for SANS SEC568: Combating Supply Chain Attacks with Product Security Testing. Doug is a regular speaker at industry conferences such as DEF CON, Blackhat, Hardware.IO and RSA, and in his career has provided software exploitation training to many audiences, including law enforcement. His research is regularly featured in publications with broad readership including Politico, Bleeping Computer, Security Boulevard, Venture Beat, CSO, Politico Morning eHealth, Tech Republic, and Axios. Douglas can be reached at [email protected]


