The PLATINUM hacker group has developed a system leveraging Intel Active Management Technology (AMT) to bypass the Windows firewall.
Microsoft is warning users of a new attack that leverage Intel’s Active Management Technology to to evade firewalls and other endpoint-based network monitoring.
The technique has been already used by a threat actor in Southeast Asia dubbed PLATINUM, it could be exploited only if the attackers gain administrative credentials.
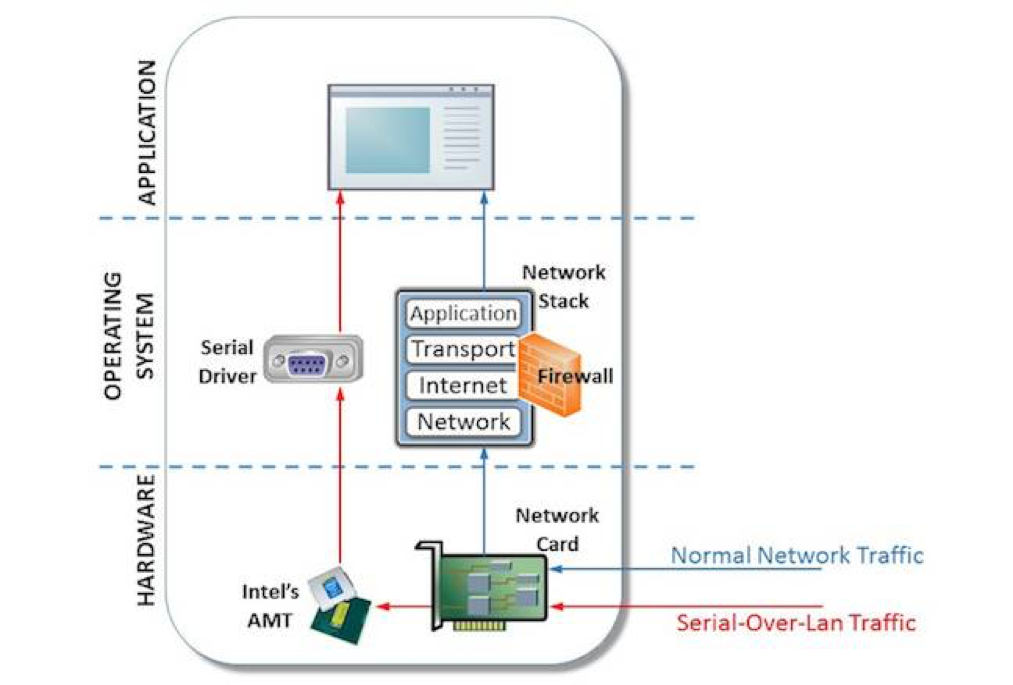
“Since the 2016 publication, Microsoft has come across an evolution of PLATINUM’s file-transfer tool, one that uses the Intel® Active Management Technology (AMT) Serial-over-LAN (SOL) channel for communication.” reads a security advisory published by Microsoft. “This channel works independently of the operating system (OS), rendering any communication over it invisible to firewall and network monitoring applications running on the host device. Until this incident, no malware had been discovered misusing the AMT SOL feature for communication.”
Attackers developed a system that uses a variant of 2016’s Platinum file transfer tool for sending malicious payloads to run inside the target network bypassing defense measures.
The PLATINUM attack leverages Intel’s Active Management Technology (AMT) to bypass the built-in Windows firewall. The AMT firmware allows attackers to run their code at a low-level below the operating system bypassing any check and accessing the host resources, including the processor and the network interface.
“Upon discovery of this unique file-transfer tool, Microsoft shared information with Intel, and the two companies collaborated to analyze and better understand the purpose and implementation of the tool. We confirmed that the tool did not expose vulnerabilities in the management technology itself, but rather misused AMT SOL within target networks that have already been compromised to keep communication stealthy and evade security applications.” continues Micorsoft.
“The updated tool has only been seen in a handful of victim computers within organizational networks in Southeast Asia—PLATINUM is known to customize tools based on the network architecture of targeted organizations. The diagram below represents the file-transfer tool’s updated channel and network flow.”
Attackers misuse the AMT’s Serial-over-LAN (SOL) feature, it’s independent of the host operating system and allow communication over the LAN if a physical connection exists, regardless of whether networking is enabled on the target.
Another feature of interest for attackers is that the embedded processor is designed to provide remote out-of-band capabilities including an IP-based KVM (keyboard/video/mouse) solution, The KVM solution enables a remote user to send mouse and keyboard input to a machine and see what’s on its display.
“The AMT SOL feature is not enabled by default and requires administrator privileges to provision for usage on workstations. It is currently unknown if PLATINUM was able to provision workstations to use the feature or piggyback on a previously enabled workstation management feature. In either case, PLATINUM would need to have gained administrative privileges on targeted systems prior to the feature’s misuse.” continues Microsoft.

Summarizing the Platinum group has devised a method then exploited SOL to transfer malware over the LAN and the process is totally transparent to the operating system.
Microsoft worked with Intel to analyze the Platinum variant and confirmed that Windows Defender ATP can detect the attack.
“The PLATINUM tool is, to our knowledge, the first malware sample observed to misuse chipset features in this way. While the technique used here by PLATINUM is OS independent, Windows Defender ATP can detect and notify network administrators of attempts to leverage the AMT SOL communication channel for unauthorized activity, specifically when used against a computer running Windows.” concludes Microsoft.
[adrotate group=”7″]