Hackers that breached Oracle MICROS systems have infected systems of other five PoS vendors that supply hundreds of thousands of companies in the US.
Last week the systems of the Oracle MICROS payment terminals division have been infected by a malware, MICROS payment terminals are installed in the most important retail chains worldwide as well as stores and hotels worldwide (more than 330,000 locations in 180 countries).
The attackers infected the troubleshooting portal of the Oracle MICROS payment terminals to steal customers’ login credentials, then use the usernames and passwords to access their accounts and gain control over their MICROS point-of-sales (POS) terminals.
The Consumerist.com reported that the company sent a memo to its customers urging the password reset for current and former MICROS accounts. The passwords of the accounts used by MICROS staff to remotely control payment terminals worldwide have to be reset.
“Oracle Security has detected and addressed malicious code in certain legacy MICROS systems,” reads a letter sent by the company to customers of its MICROS point-of-sale system.
According to the IT Giant, other services are not impacted and that payment card data are stored in encrypted format by MICROS systems.
The cyber security expert Brian Krebs, who first reported the security breach, speculated the involvement of a Russian criminal organization specialized in PoS attacks.
“A Russian organized cybercrime group known for hacking into banks and retailers appears to have breached hundreds of computer systems at software giant Oracle Corp., KrebsOnSecurity has learned. More alarmingly, the attackers have compromised a customer support portal for companies using Oracle’s MICROS point-of-sale credit card payment systems.” wrote Krebs.
According to Krebs’ sources involved in the investigation, hackers used a server previously associated with the infamous Carbanak gang, the same hacker crew that has stolen as much as one billion dollars from more than 100 banks worldwide. A
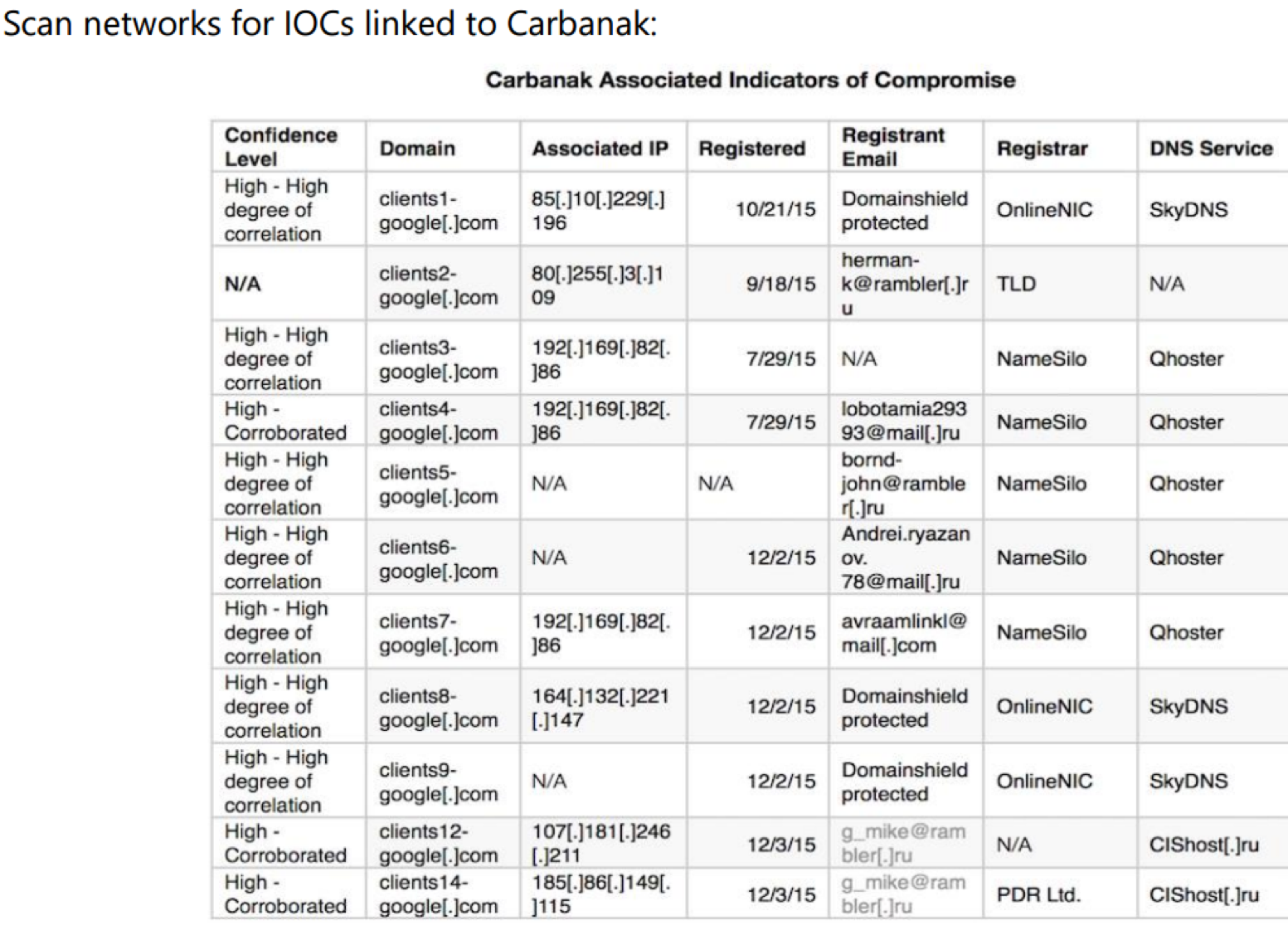
The news of the potential involvement of the Carbanak hacker crew was confirmed by the indicators of compromise (IoCs) shared by Visa is a security alert.
“Some of the addresses on this list from Visa are known to be associated with the Carbanak Gang, a group of Eastern European hackers that Russian security firm Kaspersky Lab estimates has stolen more than $1 billion from banks and retailers. Here’s the IOCs list from the alert Visa pushed out Friday:” wrote Brian Krebs in a blog post.

It seems that the hacker behind the security breach suffered by Oracle’s MICROS also targeted other PoS vendors. According to the experts from Hold Security, that the hackers also claimed to have compromised the payment systems of five other PoS vendors, including ECRS, Cin7, PAR Technology, Navy Zebra and Uniwell. One of the company, ECRS also already confirmed to Forbes that the same malware used against MICRO had been found on one of its servers, but the firm clarified that hackers might have stolen only data employee, vendor and customer contact information – payment card processing systems were allegedly not impacted.
“It now appears the same allegedly Russian cybercrime gang has hit five others in the last month: Cin7, ECRS, Navy Zebra, PAR Technology and Uniwell. Together, they supply as many as, if not more than, 1 million point-of-sale systems globally.” wrote Forbes.
“The hackers’ normal modus operandi was simple: first find weaknesses in point-of-sale (PoS) system vendors’ servers and hack them.”
ECRS confirmed to Forbes that malicious code had been found on one of its web portals, but claimed that the attackers might have stolen only contact data belonging to employee, vendor and customer. It seems that the payment card processing systems of the company were not reached by the malware.
Navy Zebra is investigating the alleged incident, its website is offline for a scheduled maintenance.
Cin7, PAR Technology and Uniwell have confirmed the attack, but denied any data breach.
Stay Tuned.