Japanese commercial and critical infrastructure organizations have been targeted a long-running campaign dubbed Operation Dust Storm.
Security firm Cylance have uncovered a long-running hacking campaign dubbed ‘Operation Dust Storm’ targeting commercial and critical infrastructure organizations in Japan.
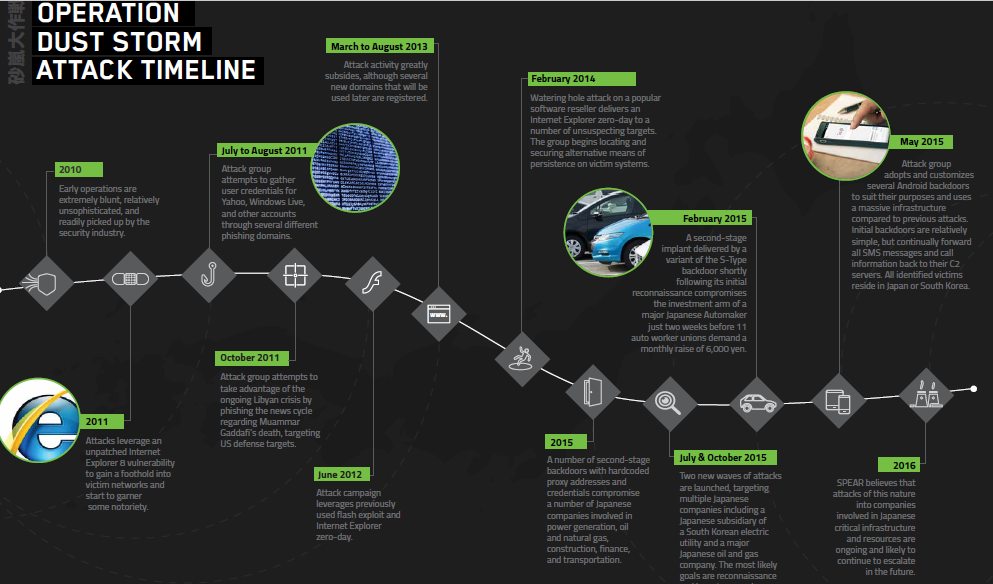
Threat actors behind the Operation Dust Storm have been active since at least 2010, the hackers targeted several organizations in Japan, South Korea, the US, Europe, and other Asian countries.
Experts believe that the group is well-organized and well-funded, a circumstance that lead the researchers to speculate the involvement of a nation-state actor.
The researchers at Cylance revealed that the threat actors started focusing on Japanese organizations since 2015, they hackers breached networks of Japanese organizations in the electricity generation, oil and natural gas, transportation, finance, and construction industries.
The list of victims includes an automaker, the Japanese subsidiary of a South Korean electric utility firm, and an oil and gas company.
The hackers demonstrated the availability of unique backdoors and zero-day exploits in their arsenal, used to launch watering holes and spear phishing attacks. In a number of attacks conducted in May 2015, the group also used several Android backdoors against targets in South Korea and Japan.

Fortunately, the attacks launched by the group behind Operation Dust Storm were not sophisticated. The researchers spotted the group in 2011, when the hackers relied on Adobe Flash Player (CVE-2011-0611) and Internet Explorer (CVE-2011-1255) zero-day vulnerabilities to deliver a strain of malware dubbed Misdat.
“Very little public information was available throughout 2010 on this threat, despite the group’s primary backdoor gaining some level of prominence in targeted Asian attacks” states the report published by Cylance “It wasn’t until June 2011 that Operation Dust Storm started to garner some notoriety from a series of attacks which leveraged an unpatched Internet Explorer 8 vulnerability, CVE-2011-1255, to gain a foothold into victim networks. “
In October 2011, the hackers targeted gathering intelligence about the Libyan crisis following the death of Muammar Gaddafi. In 2012, the group leveraged the Internet Explorer zero-day (CVE-2012-1889) for their cyber espionage campaigns.
Experts at Cylance noticed a significant reduction of the Operation Dust Storm in March 2013, after the publication of the Mandiant’s analysis of the Chinese APT group dubbed APT1.
In February 2014 the group behind Operation Dust Storm appeared again, it launched a series of attacks leveraging a new Internet Explorer zero-day exploit (CVE-2014-0322) used in watering hole attacks.
The researchers at Cylance have no doubts, the attacks against Japanese critical infrastructure will rapidly increase in the future.
“However, our team believes that attacks of this nature on companies involved in Japanese critical infrastructure and resources are ongoing and are likely to continue to escalate in the future.” Cylance concluded.