The Operation BlockBuster Coalition has disclosed the results of its investigation on the activities of the Lazarus Group that is believed to be behind the Sony Pictures hack.
State-sponsored hackers allegedly behind the Sony Pictures hack have been linked to other security breach suffered by a number of companies in South Korea.
The FBI blamed the North Korea, the Bureau released the findings of its investigation that indicated the involvement of the Government of Pyongyang in the Sony Hack.
“As a result of our investigation, and in close collaboration with other US Government departments and agencies, the FBI now has enough information to conclude that the North Korean government is responsible for these actions,” the FBI said Friday in a statement.
The US law enforcement suspect the involvement of the North Korea’s Unit 121, which is the group of hackers working under the direction of the General Bureau of Reconnaissance.
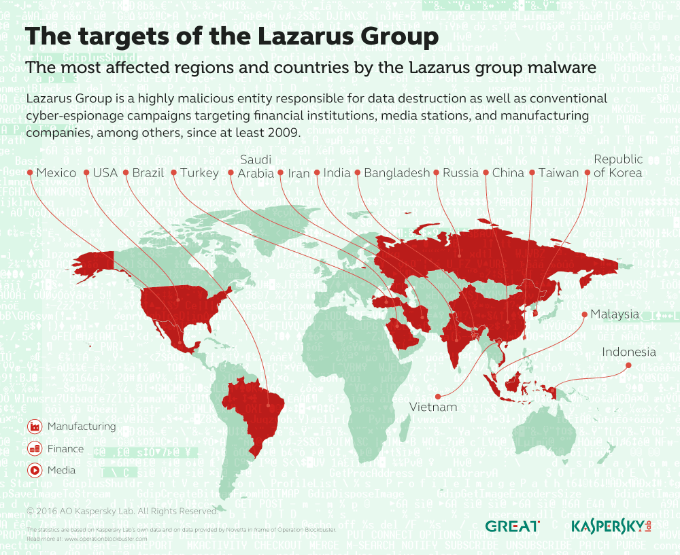
Experts at Kaspersky have linked the group to the hacking operations Dark Seoul and Operation Troy. According to Kaspersky the hacking crew has been active since at least 2009 and is still operating undercover.
Kaspersky Lab, alongside with a number of security firms including Novetta, AlienVault, Invincea, ThreatConnect, Volexity, Symantec, and PunchCyber have published reports related to the activities of the Lazarus Group.
The group of security firms formed an alliance called Operation Blockbuster that issued the detection signatures to neutralize the hacking tools used by the APT.
The Lazarus Group ’s arsenal includes the Destover wiper malware, the same used against the systems of the Sony Pictures Entertainment.
“The group deployed multiple malware families throughout the years, including malware associated with Operation Troy and DarkSeoul, the Hangman malware (2014-2015) and Wild Positron / Duuzer (2015). The group is known for spearphishing attacks, which include CVE-2015-6585, which was a zero-day vulnerability at the time of discovery.” states a report published on SecureList.

Researchers at Kaspersky Lab revealed that the Lazarus Group’s malware is mostly custom-tailored and appears highly sophisticated.
The activity of the Lazarus Group surged in 2014 and 2015, the experts of the firm composing the Operation Blockbuster team noticed a number of similarities across a number of attacks worldwide.

The researchers discovered that malware used in the attacks linked to the Lazarus Group reused several components, including at least six user-agents.
“Studying multiple coding quirks within any given malware variant actually revealed these to be coding conventions implemented across both different malware families as well as entirely new samples. A simple example of code reuse is the networking functionality that includes a half-dozen hard-coded user-agents with the misspelling ‘Mozillar’ instead of Mozilla.” states the post.
The experts also noticed other similarities in the modus operandi of the threat actors, such as the use of BAT files to delete malware pieces after infections and the password reuse in the malware droppers.
“These BAT files are generated on the fly and, while they serve their purpose of eliminating initial infection traces, they ironically double as a great way to identify the malware itself by honing in on the path-placeholder strings that generate the randomly-named BAT files on the infected systems,” Kaspersky Lab said in its report. “A high-confidence indicator of correlation is the reuse of a shared password across malware droppers used to drop different malware variants. The droppers all kept their payloads within a password-protected ZIP under the resource name ‘MYRES’. The dropper contains the hardcoded password ‘!1234567890 dghtdhtrhgfjnui$%^^&fdt‘ making it trivially easy for an analyst to reach the payload. “
The researchers confirmed that the group is still active and is currently working to new weapons to add to its arsenal.
Give a look to the reports published by Kaspersky and its partners, Symantec, Novetta and AlienVault.