North Korea-linked Lazarus APT group leveraged for the first time on a MacOS variant of the Fallchill malware in a cryptocurrency exchange attack.
According to Kaspersky, the North Korea-linked Lazarus group used a macOS malware to target a cryptocurrency exchange in a recent attack.
The activity of the Lazarus Group surged in 2014 and 2015, its members used mostly custom-tailored malware in their attacks and experts that investigated on the crew consider it highly sophisticated.
This threat actor has been active since at least 2009, possibly as early as 2007, and it was involved in both cyber espionage campaigns and sabotage activities aimed to destroy data and disrupt systems. Security researchers discovered that North Korean Lazarus APT group was behind recent attacks on banks, including the Bangladesh cyber heist.
According to security experts, the group was behind, other large-scale cyber espionage campaigns against targets worldwide, including the Troy Operation, the DarkSeoul Operation, and the Sony Picture hack.
Recently the APT targeted cryptocurrency exchanges and cryptocurrency companies, experts from Kaspersky Lab tracked a new campaign dubbed Operation AppleJeus aimed at spreading a tainted cryptocurrency trading application.
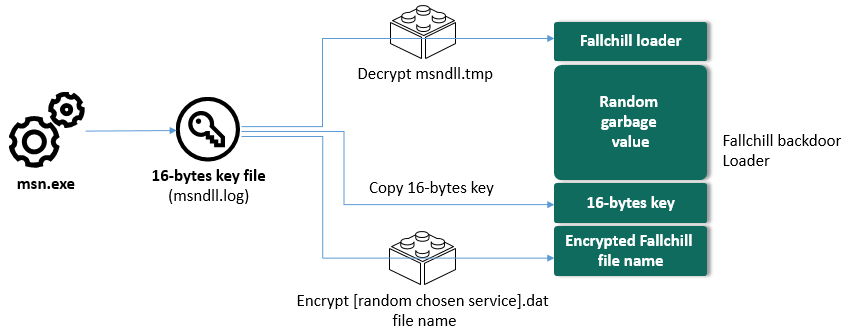
“While investigating a cryptocurrency exchange attacked by Lazarus, we made an unexpected discovery. The victim had been infected with the help of a trojanizedcryptocurrency trading application, which had been recommended to the company overemail.” states the report published by Kaspersky.
“It turned out that an unsuspecting employee of the company had willingly downloaded a third-party application from a legitimate looking website and their computer had been infected with malware known as Fallchill, an old tool that Lazarus has recently switched back to.”
The novelty of this attack is that the attacker for the first time used a version of the Fallchill malware specifically developed to target macOS systems, in addition to Windows.
The new development is very important for the strategy of the group that is expanding the list of potential targets.
“The fact that the Lazarus group has expanded its list of targeted operating systems should be a wake-up call for users of non-Windows platforms,” continues Kaspersky.
The malware was inserted into the installation package, instead, it was delivered to the target machine in the form of an update.
The experts discovered that the APT used the legitimate-looking application called Celas Trade Pro and comes from Celas Limited.
At the end of the installation process, the software runs the Updater.exe module that gathers system information and sends it back to the server in the form of a GIF image.
The malware continuously connects the command and control (C&C) server to fetch and execute an additional executable file.
Based on the server’s response (response HTTP code 200), the updater could extract a malicious code encoded with base64 and decrypts it using RC4 with another hardcoded key to retrieve an executable file.
For macOS users, Celas LLC also provided a native version of its trading app, experts noticed that a hidden ‘autoupdater’ module is installed in the background to start immediately after installation and also after every system reboot.
At the time of the report, it was not clear whether Lazarus compromised Celas server in a classic supply chain attack or managed to create “a legitimate looking business and inject a malicious payload into a ‘legitimate looking’ software update mechanism.”
Once the Cellas Trade Pro app is installed on macOS, it launches the Updater application on the system load via a file named “.com.celastradepro.plist.”
The fact that it starts with a dot symbol makes the Updates unlisted in the Finder app or default Terminal directory listing.
The “Updater” file is passed the “CheckUpdate” parameter on start, it quits if no argument is passed.
The updater is implemented using the cross-platform Qt framework, once executed it creates a unique identifier for the infected host, collects system information, and send them to the attacker’s server in encrypted format.
“First of all, Lazarusgroup has entered a new platform: macOS. There is steadily growing interest in macOS from ordinary users, especially in IT companies. Many developers and engineers are switching to using macOS. Apparently, in the chase after advanced users, software developers from supply chains and some high profile targets, threat actors are forced to have macOS malware tools.” concludes Kaspersky.
“We believe that in the future Lazarus is going to support all platforms that software developers are using as a base platform,because compromising developers opens many doors at once.”