The North Korea-linked Lazarus APT group as Lazarus is believed to be behind attacks targeting United States defense contractors.
According to Palo Alto Networks, the North Korea-linked Lazarus APT group as Lazarus is believed to be behind attacks targeting United States defense contractors.
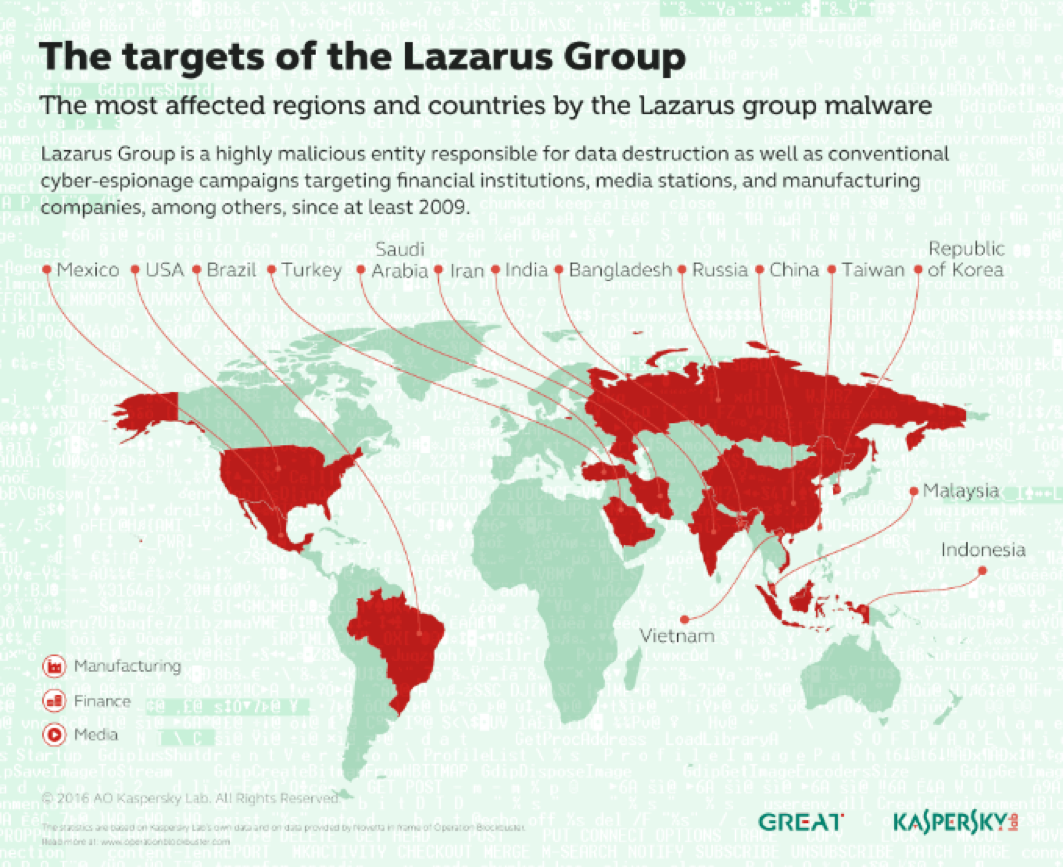
The activity of the Lazarus APT Group surged in 2014 and 2015, its members used mostly custom-tailored malware in their attacks and experts that investigated on the crew consider it highly sophisticated.
This threat actor has been active since at least 2009, possibly as early as 2007, and it was involved in both cyber espionage campaigns and sabotage activities aimed to destroy data and disrupt systems. Security researchers discovered that North Korean Lazarus APT group was behind recent attacks on banks, including the Bangladesh cyber heist.
According to security experts, the group was behind, other large-scale cyber espionage campaigns against targets worldwide, including the Troy Operation, the DarkSeoul Operation, and the Sony Picture hack.
The Lazarus group, tracked by the U.S. government as Hidden Cobra, seems to be behind recent attacks against U.S. defense contractors, likely in cooperation with other hacker groups.
The last campaign conducted by the Lazarus APT leverages spear phishing emails containing weaponized Microsoft Office documents. The documents are written in English and embed malicious macros to deliver a malware.
The hackers used decoy documents describing job openings at some U.S. defense contractors, the hackers used the text of job descriptions available on the legitimate company’s website.
“Unit 42 researchers at Palo Alto Networks have discovered new attack activity targeting individuals involved with United States defense contractors. Through analysis of malicious code, files, and infrastructure it is clear the group behind this campaign is either directly responsible for or has cooperated with the group which conducted Operation Blockbuster Sequeland, ultimately, Operation Blockbuster (originally outlined by researchers from Novetta).” reads the analysis published by PaloAlto networks.
The macros used in this last campaign presents many similarities with other cyber espionage attacks attributed to the Lazarus APT, experts also found many links between the nature of the decoy document used, the payloads and the command and control (C&C) servers.
“Recently, we’ve identified weaponized Microsoft Office Document files which use the same malicious macros as attacks from earlier this year. Based on the contents of these latest decoy documents which are displayed to a victim after opening the weaponized document the attackers have switched targets from Korean language speakers to English language speakers. Most notably, decoy document themes now include job role descriptions and internal policies from US defense contractors.” continues the analysis.
“This reuse of macro source code, XOR keys used within the macro to decode implant payloads, and the functional overlap in the payloads the macros write to disk demonstrates the continued use of this tool set by this threat group. The use of an automated tool to build the weaponized documents would explain the common but not consistent reuse of metadata, payloads, and XOR keys within the documents,”
The experts highlighted that the tools and tactics used by the group have changed only little compared to previous cyber espionage campaigns, they have no doubt about the fact that threat actors will continue their operations.
I suggest reading the analysis that also includes Indicators of Compromise.