Security experts at Trend Micro spotted a new variant of the XLoader Trojan that is targeting Android devices by posing as a security application.
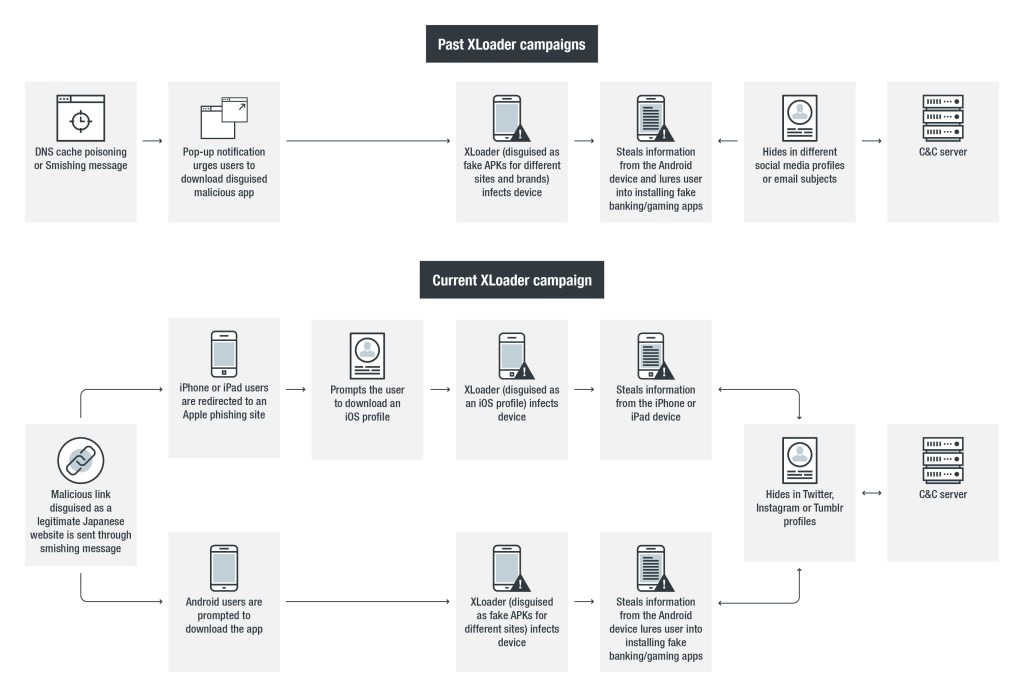
Trend Micro discovered a new variant of the XLoader Trojan that is targeting Android devices by posing as a security application, the malware also attempts to infect Apple devices (iPhones and iPads) through a malicious iOS profile. XLoader has been observed since 2018, but experts traced it back to January 2015, Trend Micro linked the threat to the FakeSpy malware.
The new XLoader Trojan variant features an updated deployment technique and includes code changes that make it different from previous variants.
The malicious code was observed in previous attacks posing as Facebook, Chrome, and other legitimate applications.
“Trend Micro researchers found a new variant that uses a different way to lure users. This new XLoader variant poses as a security app for Android devices, and uses a malicious iOS profile to affect iPhone and iPad devices.” reads the analysis published by Trend Micro. “Aside from a change in its deployment techniques, a few changes in its code set it apart from its previous versions.”
Attackers hosted the malicious code on fake websites mimicking legitimate websites such as the one belonging to a Japanese mobile phone operator. Hackers attempt to trick users into downloading the fake security Android application package (APK), they sent to the victims SMS messages containing links to the bogus websites.
When Android users access these websites or press any of the buttons they will be prompted the download of the malicious APK.
“However, successfully installing this malicious APK requires that the user has allowed the installation of such apps as controlled in the Unknown Sources settings. If users allow such apps to be installed, then it can be actively installed on the victim’s device.” continues the analysis.
The attack chain on iOS devices is more complex, users are served a phishing page that asks users to install a malicious configuration profile that is proposed as a solution to an issue preventing the site to load.
“Accessing the same malicious site would redirect its user to another malicious website (hxxp://apple-icloud[.]qwq-japan[.]com or hxxp://apple-icloud[.]zqo-japan[.]com) that prompts the user to install a malicious iOS configuration profile to solve a network issue preventing the site to load.” continues the analysis. “If the user installs the profile, the malicious website will open, revealing it to be an Apple phishing site,”
Like previous versions of the XLoader 6.0, the latest one abuses social media user profiles to hide C&C addresses.
XLoader 6.0 leverages the social media platform Twitter, the C2 address is encoded in the Twitter names.
The malware leverages Twitter profiles to encode its real command and control (C&C) addresses in the Twitter names. It implements a command called “getPhoneState”, which collects unique identifiers of mobile devices such as IMSI, ICCID, Android ID, and device serial number.
On Apple devices, the malicious iOS profile gathers the unique device identifier (UDID), International Mobile Equipment Identity (IMEI), Integrated Circuit Card ID (ICCID), mobile equipment identifier (MEID), version number, and product number.
“After the profile is installed, the user will then be redirected to another Apple phishing site.” reads the analysis. “The phishing site uses the gathered information as its GET parameter, allowing the attacker to access the stolen information,” the security researchers say.
While analyzing this attack, experts spotted another variant of XLoader that poses as a pornography app developed to target South Korean Android users The malicious APK connects to a fake website that runs XLoader in the background and uses a different fixed Twitter account.
Experts also found a variant that leverages Instagram and Tumblr to hide its C&C infrastructure.
Further technical details, including Indicators of Compromise, are reported in the analysis published by Trend Micro.