Experts from Bitdefender have uncovered the Netrepser Cyber espionage campaign that compromised more than 500 Government organizations worldwide.
Security experts at Bitdefender uncovered a cyber espionage campaign that leverages a strain of malware dubbed Netrepser to target government organizations.
Netrepser Trojan samples were first discovered by the Bitdefender in May 2016, according to experts the analysis of the command and control (C&C) servers confirms that the malware had infected more than 500 computers, mainly government agencies.
The malware researchers haven’t found any evidence linking this cyber campaign to threat actors previously analyzed.
The Netrepser Trojan allows attackers to collect system information on the target system, record keystrokes, and to steal email and instant messaging passwords, session cookies and passwords from web browsers.
“Paired with advanced spear phishing techniques and the malware’s primary focus to collect intelligence and exfiltrate it systematically, we presume that this attack is part of a high-level cyber-espionage campaign,” states the report published by Bitdefender. “The piece of malware we look at in this report comes with quite an array of methods to steal information, ranging from keylogging to password and cookie theft. “

The malware used in the campaign was built around a legitimate recovery toolkit provided by Nirsoft, the malicious code leverages the Nirsoft email and instant messaging password recovery tools to steal email and IM passwords. The Netrepser Trojan also uses another Nirsoft utility to steal passwords stored in browsers.
The malware used other legitimate tools such as the Sysinternal SDelete utility to delete files to prevent the recovery of forensic evidence and WinRAR to compress stolen data before sending it to the C&C.
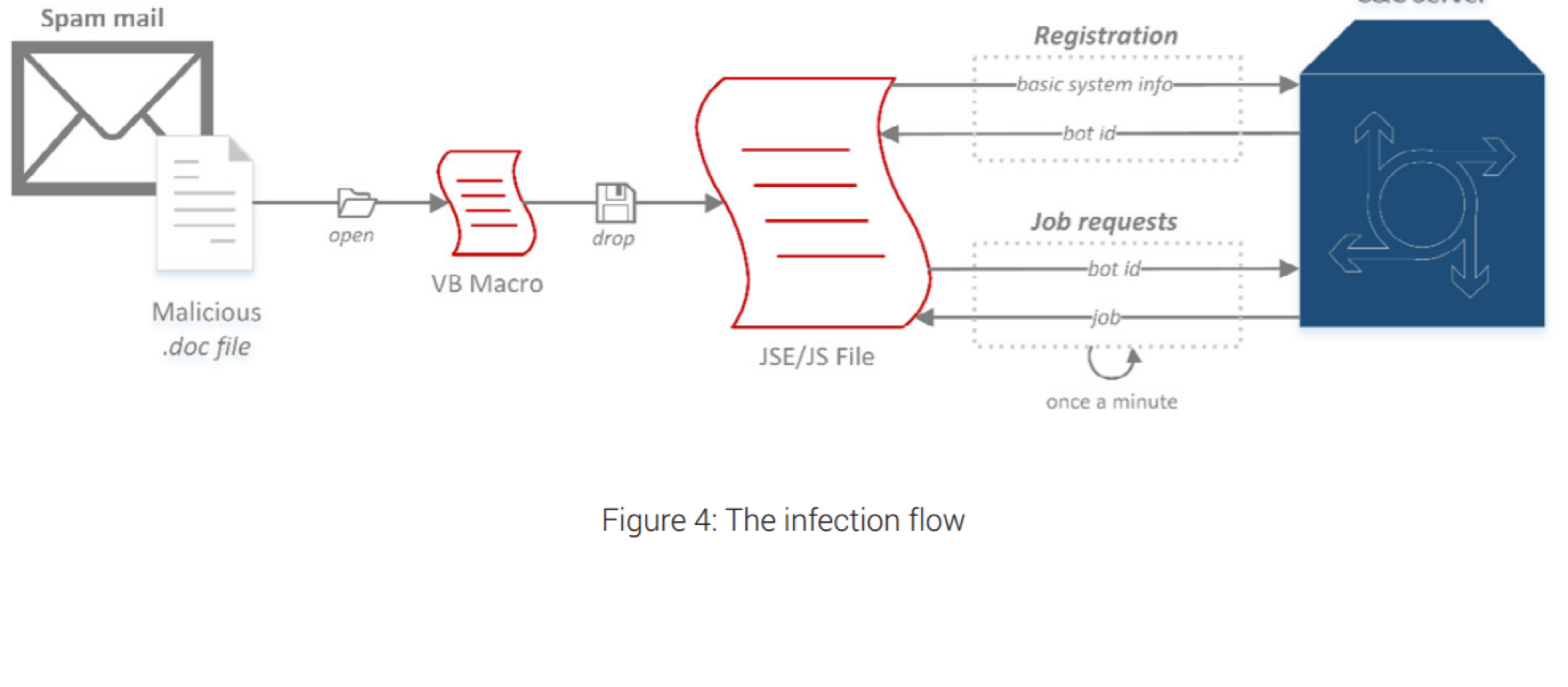
The threat actors delivered the malware via spear-phishing emails that use weaponized documents. The documents embed macros to deliver the final payload in the form of JavaScript or JavaScript Encoded files.
One of the decoy documents was titled “Russia Partners Drafting guidelines (for directors’ discussion),” researchers also observed messages using files with Russian names that translated to “installation” and “Ural.”
“The message purportedly comes from a Donald Spencer, who, according to this LinkedIn profile, is currently the Managing Director of Siguler Guff, Siguler Guff is a multi-strategy private equity investment firm which, by their own account, has over $11 billion of assets under management. Their real-estate portfolio spans from Mumbai to Moscow, where Drew Guff actually gave a speech at St. Petersburg International Economic Forum in June ‘16.” reads the analysis. “The headers reveal that the email originates from an inbox called [email protected]. Attached to the message is a DOC file containing a Visual Basic macro. If opened, the document would ask the user to enable macros in order to execute the dynamic content which would subsequently drop a JavaScript or JavaScript Encoded file to act as final payload. “
Bitdefender hasn’t made any hypothesis about the threat actor behind the campaign, the experts only highlighted that some file paths used by the Trojan are also written in Cyrillic script.
“Because of the nature of these attacks, attribution is impossible unless we dig into the realm of speculation. Our technical analysis, however, has revealed that some documents and file paths this campaign is using are written in Cyrillic” concluded Bitdefender.