What is secure access service edge (sase) and why it matters
By Paul Martini, CEO, iboss
The world of technology that exists today is substantially different from that of only a few years ago. The cloud has changed everything. Mobile phones and devices have allowed users to work from virtually anywhere. Applications that were once hosted within data centers have moved to the cloud. The combination of mobility combined with business applications available in the cloud, from any location, has allowed companies to become more agile and productive. Bandwidth is through the roof and secures encrypted network connections are mandatory. While the revolution driven by SaaS applications provides new possibilities, the challenges they bring to the world of network security are substantial.
Network security is an area responsible for inspecting content as it moves between devices and the cloud. Fundamentally, network security technology stacks require access to the data in motion to prevent malware, detect breaches and prevent data loss. Traditionally, access to this data was very straight forward. Users were constrained to physical network perimeters, such as an office building. As devices interacted with public cloud services, the data could be forced through on-prem firewall and proxy network security appliances. The data was forced to flow through chokepoints before heading to and from the internet. With mobility, users are no longer constrained to any physical location. The data leaving their devices run on public networks and organizations do not have the luxury of forcing that traffic through company-owned firewalls and proxies.
The data could be hair-pinned back through centralized datacenters before heading out to the internet but increasing bandwidth and the need for speed quickly makes this approach unsustainable and cost-prohibitive.
Mobility changes the perspective of what the perimeter is defined by and completely inverts the traditional network topology model. Instead of using a physical building to define a network perimeter, the device itself becomes the perimeter. A user working on the road is a network of one. A group of three users working from a conference is a network of three, essentially forming a remote branch office. The same could be said for branch offices or headquarters. The device and the user is where the network is defined and where trust should begin and end. Firewall and proxy appliances inherently do not fit this model because they are physical infrastructure designed to protect physical locations by inspecting all of the data leaving that location. In the new model, where should the firewall or proxy be installed? If a user is working from home, should a company owned firewall appliance be installed at the user’s home office? How will this help when the user decides to take their laptop and work from the road, immediately leaving the home network perimeter?
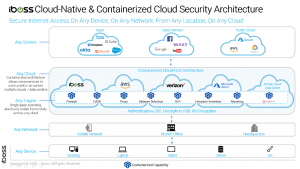
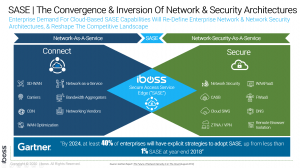
Network security functions are still required for both security and compliance. Intrusion prevention and inspection of network content for malware and data loss are fundamental techniques that are still required and essential. However, sending network data to appliances hosted at any specific location does not make sense when the connectivity is not originating from any specific location. This is where the shift of network security from on-prem network security appliances to network security delivered in the cloud is essential. Instead of sending device and user data to the network security appliance hosted at the data center, network security delivered in the cloud allows cybersecurity functions to move to where the user is located automatically. Since users are connected to cloud applications and cloud-based network security lives in the cloud as well, network security running in the cloud can move to the location from which those connections are originating. The network security functions, in essence, live where the applications live, in the cloud, allowing all data to be secured from anywhere.
To make things worse for an appliance-based approach to network security, the shear increases of bandwidth and encrypted data has been explosive. Network security appliances have theoretical throughput limits, governing the amount of data they can process and secure before becoming completely saturated and slowing down connections. Slow connections are just as bad as down connections because they drastically affect user productivity due to the inability to access business cloud applications efficiently. Network security delivered in the cloud is free from these restrictions as the compute and processing power available is not limited by any physical constraint and can scale on-demand as needed. Cloud-based network security can decrypt any volume of content and inspect it for malicious or harmful transfers with ease. Containerized approaches to cloud network security also allow for low latency and fast connections with the ability to take advantage of horizontal scaling to process any volume of traffic.
Moving network security to the cloud is a requirement with the new reality of an inverted network perimeter that exists today. When evaluating cloud-based network security platforms, it’s critical that the platform is able to deliver the same functionality found in network firewalls and proxies leaving only the appliances behind. Containerized architectures, like that found in platforms like iboss, allow both stream-based security functions found in firewalls and file-based security functions found in proxies to be delivered via a SaaS solution in the cloud. Containerization allows for raw packet processing capabilities that are required for firewall functionality, such as Intrusion Prevention protection. Ensuring that the cloud-based platform also has the policy engine capable of transitioning the network security functions mired in appliances to the cloud-based solution should also be considered.
In the Gartner paper titled “The Future of Network Security is in the Cloud” which introduced the SASE (“sassy”) model which describes this new phenomenon which must be addressed for a sustainable path to the future. Cloud SaaS network security platforms, such as iboss, allow organizations to easily migrate from traditional on-prem appliances to a sustainable cloud-based solution.
About the Author
 Paul Martini is the CEO, co-founder and chief architect of iboss, where he pioneered the award-winning iboss platform. Prior to founding iboss, Paul developed a wide variety of complex security and technology solutions for clients such as Phogenix, the U.S. Navy, and Hewlett Packard. He was also a key contributor at Copper Mountain Networks working on designing and implementing FPGAs and broadband network infrastructure used by Telcos to build the cloud. His work at Science Applications International Corporation (SAIC) involved building distributed real-time systems for companies such as Rolls Royce. Copper Mountain and SAIC both launched successful IPOs. Paul has been recognized for his leadership and innovation, receiving the Ernst & Young Entrepreneur of The Year award and being named one of Goldman Sachs’ 100 Most Intriguing Entrepreneurs. Paul holds over 100 issued patents in cybersecurity, networking and technology and has had his work published in many scientific journals, including the Journal of Foundations in Computer Science and the Journal of Analytical Biochemistry. He holds a Computer Science Degree from the University of California.
Paul Martini is the CEO, co-founder and chief architect of iboss, where he pioneered the award-winning iboss platform. Prior to founding iboss, Paul developed a wide variety of complex security and technology solutions for clients such as Phogenix, the U.S. Navy, and Hewlett Packard. He was also a key contributor at Copper Mountain Networks working on designing and implementing FPGAs and broadband network infrastructure used by Telcos to build the cloud. His work at Science Applications International Corporation (SAIC) involved building distributed real-time systems for companies such as Rolls Royce. Copper Mountain and SAIC both launched successful IPOs. Paul has been recognized for his leadership and innovation, receiving the Ernst & Young Entrepreneur of The Year award and being named one of Goldman Sachs’ 100 Most Intriguing Entrepreneurs. Paul holds over 100 issued patents in cybersecurity, networking and technology and has had his work published in many scientific journals, including the Journal of Foundations in Computer Science and the Journal of Analytical Biochemistry. He holds a Computer Science Degree from the University of California.
Paul can be reached online via LinkedIn at https://www.linkedin.com/in/martinipaul. For more information, visit the iboss company website at https://www.iboss.com.