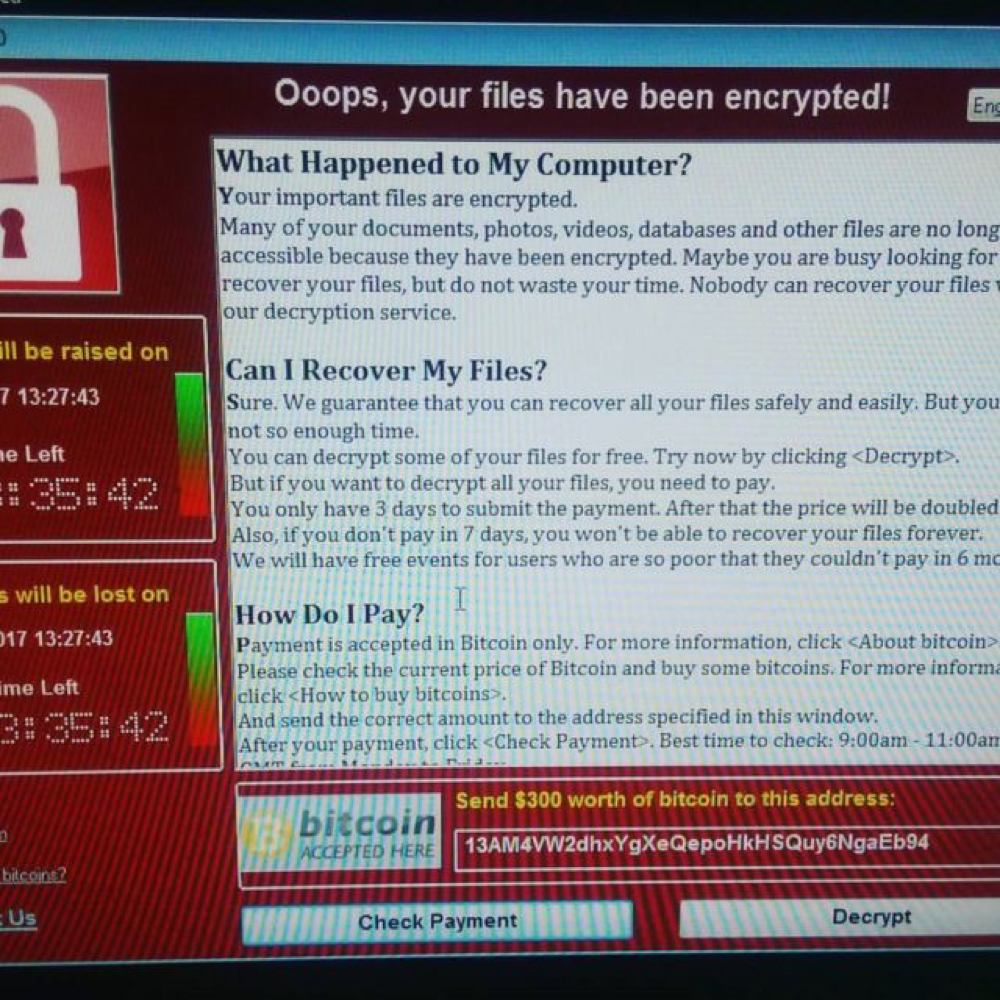
WannaCrypt ransomware attack is infecting systems in dozen countries leveraging NSA exploit codes leaked by the hacker group Shadow Brokers.
A Massive ransomware attack targets UK hospitals and Spanish banks, the news was confirmed by Telefónica that was one of the numerous victims of the malicious campaign.
The newspaper El Pais reported the massive attack, experts at Telefónica confirmed the systems in its intranet have been infected, but also added that the situation is currently under control. The fixed and mobile telephony services provided by Telefónica have not been affected by the ransomware-based attack.
The ransomware, dubbed WannaCrypt (aka Wcry, WanaCrypt, WannaCrypt), also spread among other businesses in Spain, among the victims the energy suppliers Iberdrola and the telco firm Vodafone. Spanish financial institutions confirmed the attacks by downplayed the threat.

Source Arstechnica
At the time I was writing there is no news about the damage caused by the infections.
The Spanish CERT issued an alert warning the organizations and confirming that the malware is rapidly spreading.
The strain of ransomware at the centre of the outbreak is a variant of Wanna Decryptor aka Wcry aka WanaCrypt aka WannaCrypt. Spain’s CERT put out an alert saying that the outbreak had affected several organizations.
The Wanna Decryptor is exploiting the NSA EternalBlue / DoublePulsar exploit to infect other connected Windows systems on the same network.
“The special criticality of this campaign is caused by exploiting the vulnerability described in bulletin MS17-010 using EternalBlue / DoublePulsar, which can infect other connected Windows systems on the same network that are not properly updated. Infection of a single computer can end up compromising the entire corporate network.” states the security alert issued by the CERT.
“The ransomware, a variant of WannaCry, infects the machine by encrypting all its files and, using the vulnerability mentioned in the previous paragraph that allows the execution of remote commands through Samba (SMB) and is distributed to other Windows machines in That same network.”
The DOUBLEPULSAR backdoor allows attackers to inject and execute malicious code on a target system, it is installed by leveraging the ETERNALBLUE, an SMBv1 (Server Message Block 1.0) exploit that could trigger an RCE in older versions of Windows (Windows XP to Server 2008 R2).
The Wanna Decryptor is infecting systems in dozen states, among the victims there is also the UK public health service.
The network warm capabilities of the malware are allowing the rapid diffusion of the threat
The ransomware demands $300 to restore documents, without any other details of the code we can only speculate that the attack was powered by a criminal gang.
The following aspects of the attack must be carefully analyzed:
- This attack demonstrates the risks related to the militarization of the cyberspace. Malware, exploits code and hacking tools developed by intelligence agencies and governments could be very dangerous when go out of control.
- The success of the malware is due to the wrong security posture of the victims that have no awareness of the threat and that did not apply security patches released by Microsoft.
- Modern critical infrastructure are not resilient to cyber attacks.