The threat group behind the Machete cyber espionage campaign first spotted in 2014 continues to target entities in Spanish-speaking countries.
According to the researchers at security firm Cylance Threat actors behind the cyber espionage campaign dubbed Machete continue to target entities in Spanish-speaking countries.
The Machete campaign was first uncovered by the researchers at Kaspersky in August 2014 and according to the experts, it had been active since 2010.
“While assisting the customer, we found a very interesting file in the system that is completely unrelated to China and contained no Chinese coding traces. At first look, it pretends to be a Java related application but after a quick analysis, it was obvious this was something more than just a simple Java file. It was a targeted attack we are calling “Machete”.” wrote Kaspersky in 2014.

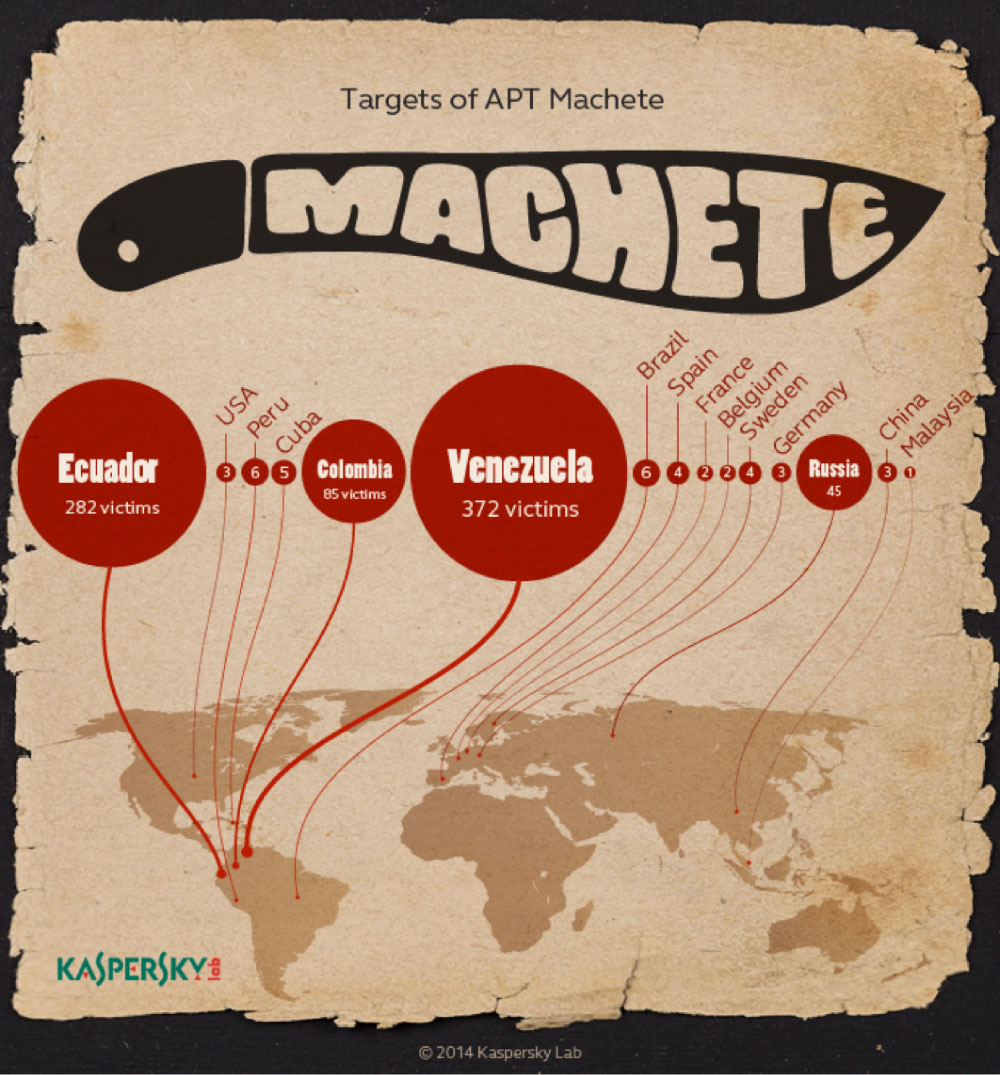
The cyber spies targeted intelligence services, embassies, government institutions and military organizations, the majority of the victims at the time were located in Ecuador, Colombia, Peru, Venezuela, Cuba, Spain, and Russia.
The hackers continue to leverage spear-phishing emails and fake blogs to deliver malware a spyware.
“Phishing emails continued to use links to external ZIP or RAR archives, which ultimately contained an executable with the extension SCR. All of the executables SPEAR identified contained either an executable generated by the open source Nullsoft Scriptable Install System (https://sourceforge.net/projects/nsis/) or a self-extracting RAR executable (SFX). NSIS provides a surprisingly easy way for attackers to obfuscate malicious code via multiple common compression routines like ZLib, BZip2, LZMA.” reads the analysis published by Cylance. “The attackers also made extensive use of Hostinger’s cheap web hosting services to deliver initial payloads. SPEAR identified the following URLs were used in phishing attempts:”
The malicious code is able to log keystrokes, capture audio from the microphone, collect geolocation data, take screenshots and images via the webcam, and of course exfiltrate documents to a remote command and control server or a special USB device.
The researchers at Cylance reported the attackers managed to steal more than 100 Gb of data from hundreds of victims.
The majority of the victims identified by Cylance were located in Ecuador, Venezuela, Peru, Argentina and Colombia, but some targets were also found in Korea, the U.S., the Dominican Republic, Bolivia, Cuba, Guatemala, Nicaragua, Mexico, the U.K., Canada, Germany, Russia and Ukraine.
The novelty is represented by the presence of telecommunications and power companies in the list of targeted organizations.
The researchers highlighted that many of the targeted states are known customers of surveillance firms such as FinFisher and Hacking Team, “which suggests they likely have yet to fully mature and develop their own internal cyber capabilities”
Cylance speculates the threat actors are Brazilians because they mostly targeted countries bordering Brazil.
The attackers continued their activity by moving to a new command and control (C&C) infrastructure and applying minor changes to their malicious code mostly to evade detection.
“El Machete has continued largely unimpeded in their espionage activities for the past several years, despite the abundance of publicly available indicators.” continues Cylance researchers.”Many of these indicators should have allowed defenders to reliably identify this threat, but the majority of antivirus (AV) solutions continue to have very low detection rates across current samples,”
The analysis published by Cylance includes several useful information, including IoCs, enjoy it.