Experts at Recorded Future have discovered a cheap RaaS, the Karmen Ransomware that deletes decryptor if detects a sandbox.
Security experts from threat intelligence firm Recorded Future have spotted a new ransomware as a service (RaaS) called Karmen. The service allows customers to easy create their ransomware campaign in a few steps and without specific skills.
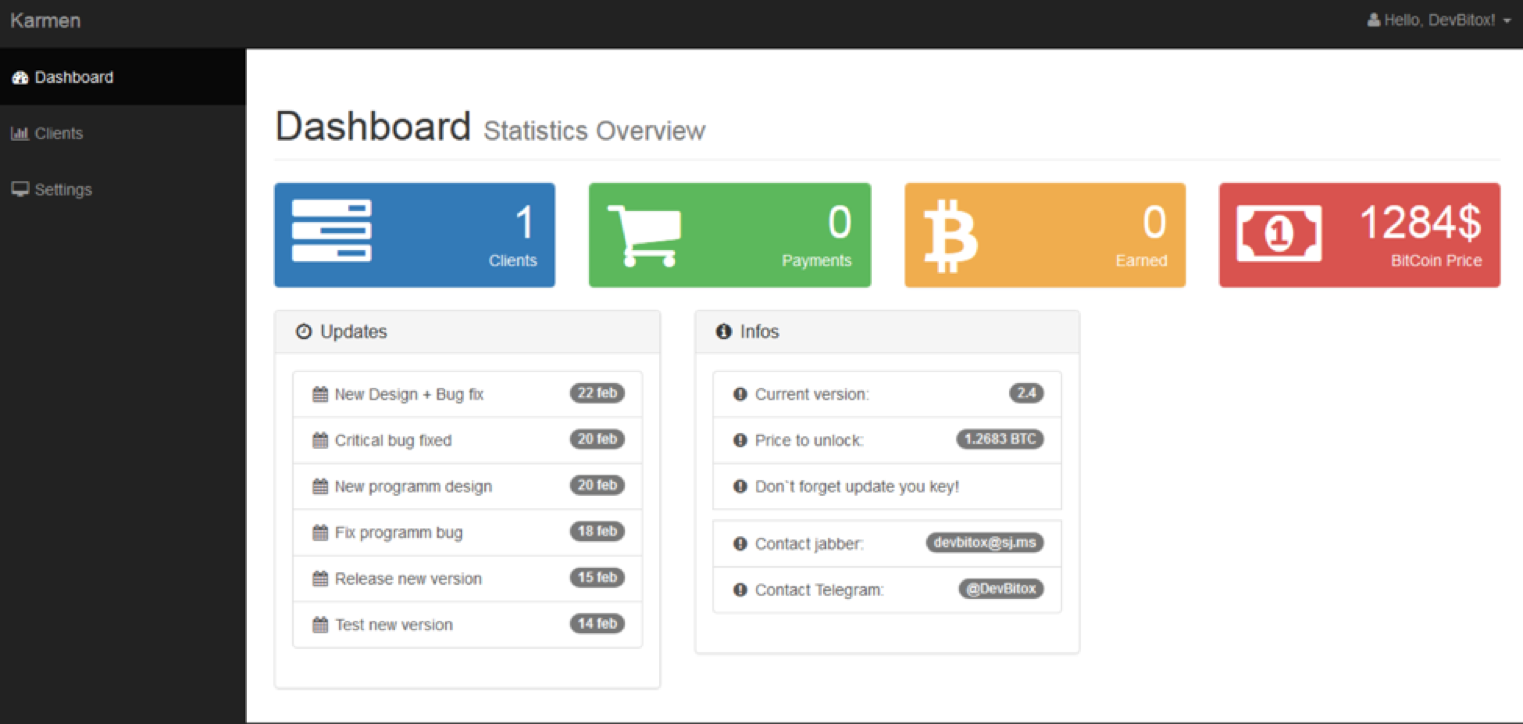
Wannabe-crooks also track infected systems via a “Clients” tab, the Dashboard implements an efficient and easy to use cockpit that include various information such as the number of infected machines, earned revenue, and available updates for the malware.
The Karmen RaaS is very cheap, it costs just $175, buyers can decide the ransom prices and the duration of the period in which the victims can pay the ransom.
The Karmen ransomware is based on the open-source ransomware Hidden Tear, which was released in August 2015 by the Turkish security researchers Utku Sen for educational purposes.
The first Karmen infections were reported in December 2016, the malware infected machines in Germany and the United States.
The Karmen ransomware is a multi-threaded and multi-language ransomware that supports .NET 4.0 and uses the AES-256 encryption standard.
The malware is .NET dependent and requires PHP 5.6 and MySQL.
“On March 4, 2017, a member of a top-tier cyber criminal community with the username “Dereck1” mentioned a new ransomware variant called “Karmen.” reported a blog post published by Recorded Future.
“Further investigation revealed that “DevBitox,” a Russian-speaking cyber criminal, was the seller behind the Karmen malware on underground forums in March 2017.”
“However, the first cases of infections with Karmen were reported as early as December 2016 by victims in Germany and the United States.”

Once infected a machine, the ransomware displays a ransom note with payment instructions, unlike similar malware, the Karmen ransomware automatically deletes the decryptor when detecting a sandbox environment or any other analysis software.
“A notable feature of Karmen is that it automatically deletes its own decryptor if a sandbox environment or analysis software is detected on the victim’s computer.” continues the blog post.
Below the list of ransomware features provided by DevBitox:
- Multi-threaded
- Multi-language
- Supports .NET 4.0 and newer versions
- Encryption algorithm: AES-256
- Adaptive admin panel
- Encrypts all discs and files
- Separate BTC wallet for each victim
- Small size
- Automatic deletion of loader
- Automatic deletion of malware (after payment was received)
- Minimal connection with control server
- Robust control panel
- Almost FUD (1/35)
- Automatic file decryption after received payment
- T2W compatible
- File extensions remain the same
- Detection of anti-debugger/analyzers/VM/sandbox
- Automatic deletion of decryptor if sandbox environment is detected on victim’s computer*
- Light version: obfuscation and autoloader only
- Full version: detection of analyzing software
The ransomware is available for sale in both light and full versions, the light version doesn’t include anti-analysis features.