By Jhilam Biswas, Customer Engineering Manager, Google Cloud
The growth of cloud computing is undeniable. According to Garter’s report, the global spending on public cloud services was around $490.3 billion in 2022, and this number is projected to grow by 20.7% in 2023 to reach $591.8 billion. What propels this phenomenal growth are a number of reasons, a few notable ones being accelerating digital transformation and faster time to market, increasing demand for hybrid and multi-cloud deployments, leveraging the pay-as-you-go model of the cloud.
As cloud computing grows, so does the need for cloud security. Cloud environments are complex and often have a large attack surface, making them attractive targets for cyber attackers. In fact, a recent study by Verizon found that more than 80% of enterprise breaches involved threats initiated by external sources and 50% of all social engineering attacks are pretexting incidents—nearly double of last year’s total.
Given the importance of cloud security in the age of cyberattacks, in this article, we’ll cover some critical methodologies used in Google Cloud to prevent the most commonly seen security incidents in the cloud. Although the solutions mentioned here are unique to Google Cloud, you can find similar services in other public cloud providers that provide similar functionality.
- Prevent public exposure of your API credentials, encryption keys and secrets: Developers often unknowingly share API credentials, encryption keys and secrets in their codebase that resides in a code hosting platform such as GitHub or Google Cloud’s Artifact Registry. This might sound like a common practice usually done for the sake of “quick accessibility”. In the long run though, when the code gets pushed into production with the credentials/keys in the code itself, it might pose a huge risk. If a hacker gets access to those credentials that’s publicly available in your code-base, they potentially hold the power to gain unprivileged access to your organization’s proprietary data and can cause irreversible damage. Some mechanisms to prevent this is by using extremely granular IAM policies not only for identities but also on the resource itself. For example, in Google Cloud, you can use Organization Policy Constraints to limit who can create service account keys.
- Prevent user accounts compromise: Password spray and brute force attacks are the most common ways to steal identities and use that access for malicious purposes. As enterprises, you can adopt a couple of solutions to prevent such threats. For example, you can use 2FA / U2F solutions and make its requirement a mandate in your organization. You can also use a tool like “Password Alert” that prevents re-use of passwords that are being used by users in your organization to be used elsewhere on the internet. Consider also using tools such as Google’s Password Manager that helps you manage passwords all at one place and identify your passwords that were exposed in a third-party data breach.
- Monitor virtual machines for cryptojacking: Cryptojacking is a type of malware attack that uses a victim’s virtual machine resources to mine cryptocurrency. This can have a significant impact such as data breaches, an unwarranted massive cloud bill or other security incidents that can negatively affect your organization. Cloud-based cryptojacking is on the rise and occurs when an attacker gains access to a victim’s cloud computing account and uses it to mine cryptocurrency. This type of attack is more scalable and anonymous, making it more difficult to detect and prevent. Google Cloud’s native built-in solutions in the Security Command Center such as the “Virtual Machine Threat Detection” and “Event Threat Detection” can help identify such threats in the cloud. These are critical threats due to the aforementioned reasons and so having that instant visibility can help organizations immediately fix such issues whenever they get identified.
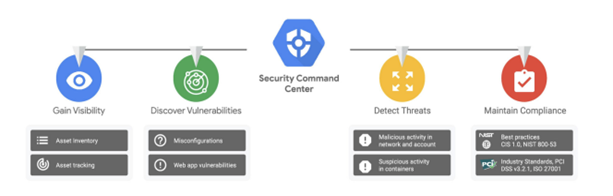
Source: https://cloud.google.com/security-command-center
- Prevent misconfigurations of cloud storage buckets: If you are starting a new project and need a durable object-storage solution to store, manage and retrieve files, cloud storage is probably one of the widely used native cloud services that organizations use. However, cloud storage buckets are often misconfigured in a way that your buckets get exposed to the internet unknowingly. In order to prevent such misconfigurations, you can use services such as Organizational Constraints for Cloud Storage in Google Cloud to enforce constraints such as public access prevention and object retention policies. You can also use Security Command Center’s Storage Vulnerability Findings to proactively detect misconfigurations in storage buckets.
- Audit your users’ Cloud IAM Entitlement Lifecycle to improve security posture: Just about every org has an outlook.com / yahoo.com / gmail.com account somewhere in their IAM structure. These user accounts could potentially be malicious with privileged permissions and pose a threat to misuse your cloud resources. A manual audit of personal accounts/users can be difficult to track in your cloud IAM hierarchy. To help organizations with the detection of such accounts, you can use Google Cloud’s Organizational Policies to limit domains with IAM grants. In Google Cloud, you can also use Security Command Center’s Event Threat Detection to search IAM for external grants.
Cloud is a complex environment to manage and security in the cloud is even a tougher problem to solve for. However by taking advantage of the approaches called out above, you can shield your organization from the most common threats seen in cloud environments.
About the Author
 Jhilam Biswas is an experienced cybersecurity professional with over 9 years of experience in cloud computing and security. She’s currently a Customer Engineering Manager at Google Cloud helping strategic digital native clients to deploy and scale securely in the cloud. Before Google, she has worn many security hats in different F500 companies such as Security Solutions Architect at Akamai and Security Engineer at Cisco. She earned her MS Degree from the University of Maryland at College Park with a focus on cloud computing and network security. Jhilam can be reached online at https://www.linkedin.com/in/jhilambiswas/ and at our company website https://cloud.google.com/
Jhilam Biswas is an experienced cybersecurity professional with over 9 years of experience in cloud computing and security. She’s currently a Customer Engineering Manager at Google Cloud helping strategic digital native clients to deploy and scale securely in the cloud. Before Google, she has worn many security hats in different F500 companies such as Security Solutions Architect at Akamai and Security Engineer at Cisco. She earned her MS Degree from the University of Maryland at College Park with a focus on cloud computing and network security. Jhilam can be reached online at https://www.linkedin.com/in/jhilambiswas/ and at our company website https://cloud.google.com/


