Researchers at Menlo Labs uncovered a malicious email campaign targeting employees of banks and financial services companies abusing Google Cloud Storage.
The campaign targeted organizations in the US and the UK, the attackers have been abusing Google Cloud Storage to deliver payload.
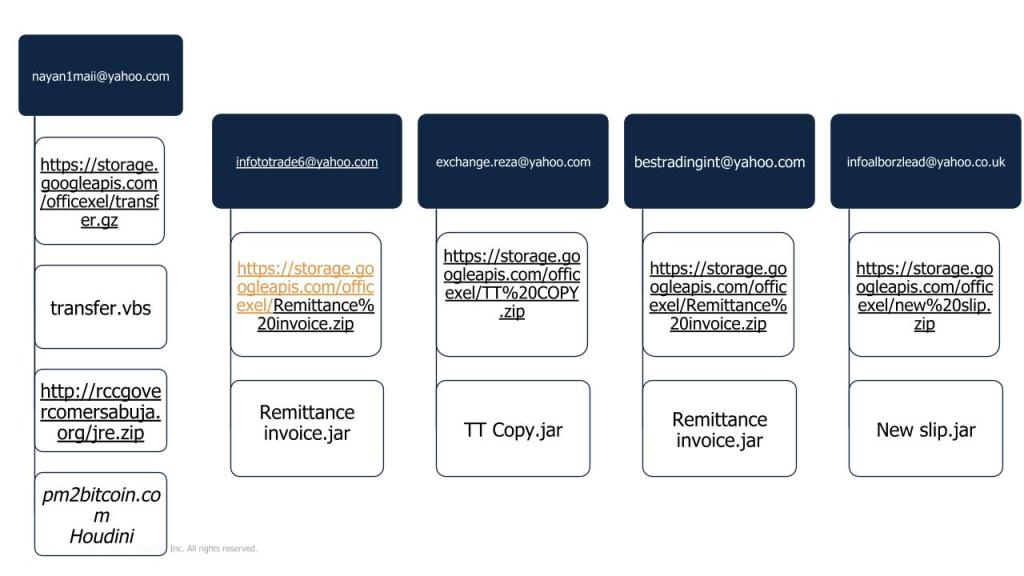
The spam campaign uses messages including links that point to archive
files such as .zip or .gz. Attackers attempt to trick victims into clicking on the malicious links. Threat actors hosted the malicious payloads on storage.googleapis.com, which is associated with Google Cloud Storage service. The payload belongs to the Houdini and QRat malware families.
With this attack scheme, threat actors are able to bypass security controls in place within targeted organizations.
“In all of these cases, the malicious payload was hosted on storage.googleapis.com, the domain of the Google Cloud Storage service that is used by countless companies. Bad actors may host their payloads using this widely trusted domain as a way to bypass security controls put in place by organizations or built into commercially security products.” reads the analysis published by security researchers at Menlo.
“It’s an example of the increased use of “reputation-jacking”—hiding behind well-known, popular hosting services to help avoid detection. “
These attackers likely used malicious links rather than malicious attachments because of the combined use of email and the web to infect victims with this threat. Many security solution are able to detect malicious attachments but identify malicious URLs only if they included in a blacklist.
The attackers leveraged two types of payloads to compromise the victims, VBS scripts and JAR files. Experts analyzed some malicious VBS scripts that were highly obfuscated and were likely created by one of the builder available in the cybercrime underground.
The experts analyzed three scripts which belong to the Houdini malware family. The codes were highly obfuscated with three nested levels of obfuscated VBScript and encoded using Base64 encoding. Researchers discovered that they used the same C2 domain (pm2bitcoin[.]com) and secondary C2 (fud[.]fudcrypt[.] com ).
Researchers noticed the same string “<[ recoder : houdini (c) skype : houdini-fx ]>” appears in the last level of obfuscated VBScript and all download a JAR file.
One of the files belongs to the Houdini/jRAT malware family, meanwhile other JAR files belong to the QRat malware family.
“The Financial Services vertical continues to be a very attractive target for attackers, and Remote Access Trojans (RATs) play an important role in gaining control over a compromised machine within an enterprise. Novel ways of gaining endpoint access are always being developed, and will continue to evolve.” Menlo Labs concludes.
“Financial Services companies can expect to be the target of even more sophisticated malware and credential phishing attacks,”