Use “Imaginary Enemy” methodology to mitigate APT Attack
By Jamal Uddin Shaikh, Cybersecurity Architect and Technology Lead , Appxone
- Introduction
Early in the morning, I was pulled up by the leader to analyze the FireEye incident. The entire security circle in the Moments of Friends was also boiling, but as the analysis deepened, it was found that it was a little “big-skilled”. There were no sophisticated tools and technical solutions that I wanted. They were all Red team simulation tools with known attack techniques used by Threat Actor. But from the perspective of a member of the Red team, a lot has been gained.
- Does the Red team service really use “Imaginary Enemy” methodology”?
Use the “Imaginary Enemy” method to assess corporate security, and the method here is often defined as an APT method.
- Is the current domestic Red team service using APT?
- What is APT means?
- How is the Red team simulated?
In the defense strategy given by FireEye, it is obvious that there are many samples, tools, and backdoors at the beginning of APT. The security personnel of FireEye have made various technical methods in APT activities into Red team tools to evaluate the company’s defense capabilities against various APT technologies, at least from the tool level. FireEye has achieved the requirements of “Imaginary enemies”. What about the domestic Red team? , Everyone knows for yourself, not much to say.
What is the APT method? Most domestic companies put APT tracking in the threat intelligence department, and some analysis reports have been issued. From the technical means, the so-called APT report may only be called a sample analysis report. Everyone knows whether the discovered technology has been instrumented and provided to the Red team for Red team evaluation.
- If the FireEye team only has “this level”, it’s just that
Known as the world’s most APT-knowledge, if only the level of strategy reflects, it is a bit of a misnomer.
From the analysis of the strategy, there are about 60% of open source projects, about %35 are the secondary development of open source projects, about %5 are the realization of known technologies, and all technologies are known and public. There is no forward-looking technical solution, no large-scale tool platform, I want to say “I don’t believe it.”
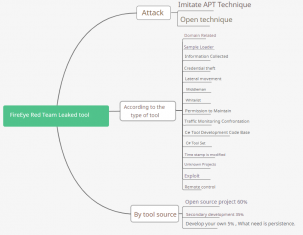
- Looking at the engineering level of external Red teams from the perspective of strategy
To put it bluntly, it is a lot ahead of China, Russia and North Korea. Most of them are C# development, in line with the technical trend of external Red team circles. Most of Github’s open-source Red team tools are also C# development. I have read the codes of some tools, and the standards are also average. This may be the reason why FireEye has carried out a lot of secondary development! Looking back at the topic, the idea of weaponization has only started, and it is a bit of a face when talking about engineering. There is no open source atmosphere, no engineering ability, the coding ability that wants to open source is weak, and those who have strong coding ability cherish themselves. The legal risk of tools are also a major constraint.
“Neither understand APT nor write code, you tell me that you are a Red team”
- As a Cybersecurity professional, we still need to look at some technology
Most Cybersecurity professional may be like me, to see if they can get some tools back. The Leaked FireEye tools are at least more stable than open source tools. But I used md5 to catch VirusTotal, and the conclusion is: No! No! No! But it also gave some minor exposures:
GoRAT FireEye is actually working, I may need to try it.
Among them is a D language backdoor, do more niche languages to alleviate the pain of anti-virus clash.
DLL hijacking is a good way to maintain permissions. The strategy contains a lot of dll hijacking schemes, but they are all public.
The production of various Loaders is still at the forefront of confrontation.
Still need to build more wheels, the existing wheels are not necessarily good wheels.
The weaponization of known vulnerabilities is still necessary. I believe that most people are as greedy as me for the CVE weaponization tool, and subconsciously believe that the use of FireEye tools must be a good option.
- Our road is still long
The Red team still has a long way to go. Recognize the gap and see the direction.
Finally, I hope FireEye will disclose the technical details of the attack and hope to see the top of the hacker world. As far as the current public is concerned, I want to say “My pants are all taken off, will you show me this?”
About the Author
 Jamal Uddin Shaikh is the Cybersecurity Architect and Technology Lead of the Appxone. He has done B.S. in Computer Engineering as well as have CISM, CPTE, CEH, ECSA, IBM QRadar, MCSA, MCITP professional certifications. He have 16 years of cyber security hands-on experience.
Jamal Uddin Shaikh is the Cybersecurity Architect and Technology Lead of the Appxone. He has done B.S. in Computer Engineering as well as have CISM, CPTE, CEH, ECSA, IBM QRadar, MCSA, MCITP professional certifications. He have 16 years of cyber security hands-on experience.
He found SQL injection vulnerability at NASA website, XSS vulnerability at Microsoft phone site, XSS Dom based vulnerability in Microsoft.com. He can create fully undetectable malicious link for reconnaissance or phishing.
He is Cyber Security instructor at Udemy.com, and launched online Courses “Combating Advanced Persistent Threat – APT Attack”, “Learn Hacked Credit and Debit Card Recovery from Scratch” and “Manual Bug Bounty Hunting for earning handsome money”.
He also developed a web based Dark Web Monitoring tool name as “Threat Ninja” which help us to centralize Hacked Credit and Debit Card Recovery service. He also developed Red Team and Malware development tool. He involved in the core development of Threat Intelligence Platform application.
Jamal Uddin can be reached online at [email protected] and at linkedin https://www.linkedin.com/in/engrjamal/


