The French police force, National Gendarmerie, announced to have neutralized the Retadup malware on over 850,000 computers taking over its C2 server.
The French police force, National Gendarmerie, announced the successful takedown of a huge RETADUP botnet after it has taken the control of its command and control (C2) server. The operation allowed the France law enforcement agency to remotely disinfect more than 850,000 computers worldwide with the help of Avast malware researchers.
#BellesAffaires #Cybercriminalité
La #gendarmerie démantèle l'un des plus gros réseaux d'ordinateurs piratés au monde ! En lien avec le #FBI, les #cybergendarmes parviennent à "désinfecter" à distance plus de 850 000 ordinateurs. Une #PremièreMondiale ! 🇫🇷— Gendarmerie nationale (@Gendarmerie) August 28, 2019
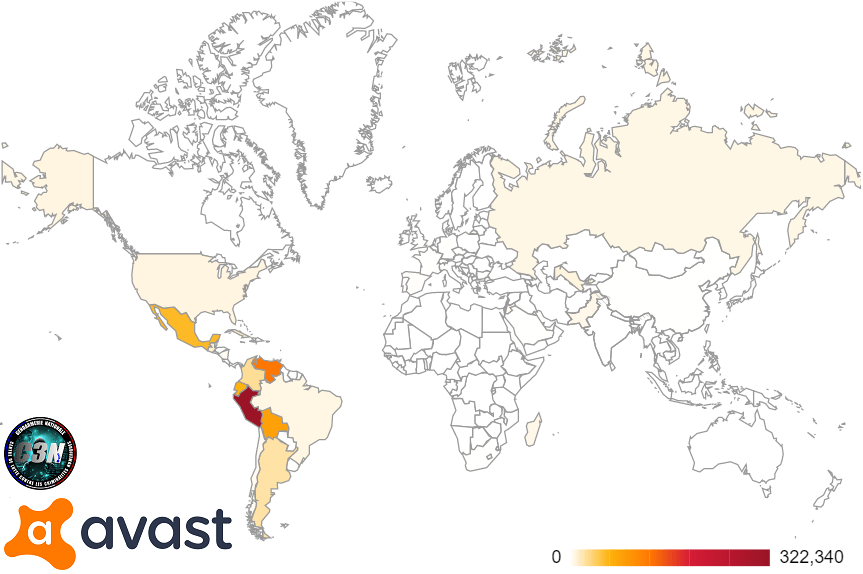
Most of the infected systems were located in Latin America, more than 85% of victims did not have any security software installed. The highest number of infection was in Peru, followed by Venezuela, Bolivia, Mexico and Ecuador.
The Retadup bot has been around since at least 2015, it was involved in several malicious campaigns aimed at delivering malware such as information stealers, ransomware and miners.
In recent campaigns, the Retadup worm was observed delivering Monero cryptocurrency miners in Latin America.
Earlier this year, malware researchers from Avast antivirus firm discovered a design flaw in the C&C protocol of the botnet that could have been exploited to remove the malware from infected computers.
The exploitation of the flaw required the control of the command and control server that was hosted with a hosting provider located in France.
Then Avast contacted the Cybercrime Fighting Center (C3N) of the French National Gendarmerie in March this year and requested its support to dismantle the botnet.
The French authorities took control over the RETADUP C2 server in July and replaced it with a C2 server designed to disinfect the machines by abusing the design flaw in its protocol. The server instructed the bot to remove itself from infected machines.
“In accordance with our recommendations, C3N dismantled a malicious command and control (C&C) server and replaced it with a disinfection server.” reads a blog postpublished by Avast. “The disinfection server responded to incoming bot requests with a specific response that caused connected pieces of the malware to self-destruct. At the time of publishing this article, the collaboration has neutralized over 850,000 unique infections of Retadup.”
The National Criminal Intelligence Service at Gendarmerie Nationale will keep the disinfection server online for a few more months to remove the malware from the largest number of computers. Experts noticed that some infected computers still haven’t contacted the disinfection server, some have been offline since July.
“We managed to clean more than 850,000 machines that were infected by the Retadup virus.This fleet of computers made it possible to make global attacks of very, very great magnitude.You can imagine our satisfaction to have succeeded to remove the viruses from the computers of the victims, who at first did not even know that their machines were infected.” explained Jean-Dominique Nollet, head of the National Criminal Intelligence Service at Gendarmerie Nationale.
“Basically, we managed to detect where was the command server, the control tower of the network of infected computers, the ‘botnet’. It was copied, replicated with a server of ours, and made to do things that allow the virus to be idle on the victims’ computers.”
The French authorities also shared with the FBI its findings on the botnet, the experts, in fact, discovered that part of the C2 infrastructure was in the United States. The FBI quickly took down this C2 server on July 8.
“Some parts of the C&C infrastructure were also located in the US. The Gendarmerie alerted the FBI who took them down, and on July 8 the malware authors no longer had any control over the malware bots. Since it was the C&C server’s responsibility to give mining jobs to the bots, none of the bots received any new mining jobs to execute after this takedown.” continues Avast. “This meant that they could no longer drain the computing power of their victims and that the malware authors no longer received any monetary gain from mining.”
Experts explained that Retadup has been under active development for years now, for this reason, there are many different variants in the wild. These variants are quite similar and only differ in how the implementation of the functionality, while the core is written in either AutoIt or AutoHotkey.
The analysis of the C&C server allowed the experts to discover that it also contained a .NET controller for an AutoIt RAT called HoudRat. Researchers believe it is just a more and less prevalent variant of Retadup.
Technical details on the Retadup bot are included in the analysis published by Avast.