Four malicious Chrome extensions may have impacted more than half million users likely to conduct click fraud or black search engine optimization.
More than half million users may have been infected by four malicious Chrome extensions that were likely used to conduct click fraud or black search engine optimization.
According to ICEBRG, the malicious extensions also impacted employees of major organizations, potentially allowing attackers to gain access to corporate networks.
“Recently, ICEBRG detected a suspicious spike in outbound network traffic from a customer workstation which prompted an investigation that led to the discovery of four malicious extensions impacting a total of over half a million users, including workstations within major organizations globally.” states the analysis published by ICEBRG. “Although likely used to conduct click fraud and/or search engine optimization (SEO) manipulation, these extensions provided a foothold that the threat actors could leverage to gain access to corporate networks and user information.”
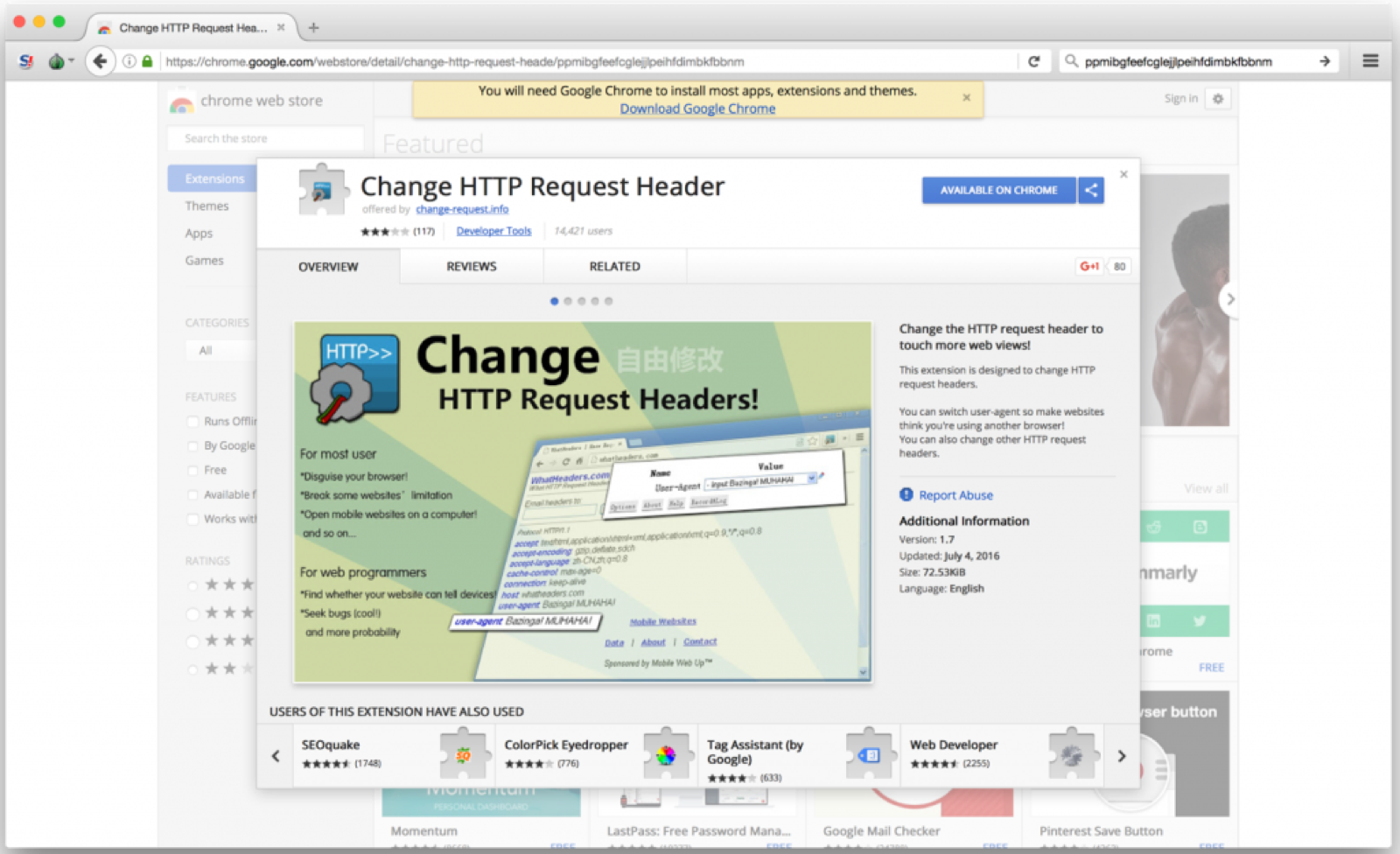
The researchers noticed an unusual spike in outbound traffic volume from a customer workstation to a European VPS provider. The analysis of the HTTP traffic revealed it was to the domain ‘change-request[.]info’ and was generated from a Chrome extension with ID ‘ppmibgfeefcglejjlpeihfdimbkfbbnm’ named Change HTTP Request Header that was available via Google’s Chrome Web Store.
The extension does not contain any malicious code, but the combination of “two items of concern that” could allow attackers to inject and execute an arbitrary JavaScript code via the extension.
The experts highlighted that Chrome extensions are not allowed to retrieve JSON from an external source and execute JavaScript code they contain, but need to explicitly request its use via the Content Security Policy (CSP).
Once enable the ‘unsafe-eval’ (Figure 3) permission to retrieve the JSON from an external source the attacker can force the browser to execute malicious code.
“When an extension does enable the ‘unsafe-eval’ (Figure 3) permission to perform such actions, it may retrieve and process JSON from an externally-controlled server.” “This creates a scenario in which the extension author could inject and execute arbitrary JavaScript code anytime the update server receives a request.” continues the analysis.
The Change HTTP Request Header extension is able to download obfuscated JSON files from an external source (‘change-request[.]info’), by invoking the ‘update_presets()’ function.
The Chrome extension implemented an anti-analysis technique to avoid detection.
The extension checks the JavaScript for the presence of native Chrome debugging tools (chrome://inspect/ and chrome://net-internals/), and if detected, halts the injection of malicious code segment. The Chrome extension implemented an anti-analysis technique to avoid detection.
Once injected the code, the JavaScript creates a WebSocket tunnel with ‘change-request[.]info’ and uses it to proxy browsing traffic via the victim’s browser.
During the analysis, the experts observed that this feature was observed by threat actors for visiting advertising related domains likely to conduct click fraud scams.
“The same capability could also be used by the threat actor to browse internal sites of victim networks, effectively bypassing perimeter controls that are meant to protect internal assets from external parties.” continues the analysis.
The security experts discovered other Chrome extensions with a similar behavior and using the same C&C server.
- Nyoogle – Custom Logo for Google
- Lite Bookmarks
- Stickies Chrome’s Post-it Notes