Social networks could be a privileged attack vector to rapidly spread a malware to a huge audience, FacexWorm targets cryptocurrency users by spreading through Facebook Messenger.
Social networks could be a privileged attack vector to rapidly spread a malware to a huge audience.
In the last hours, a new threat is spreading through leveraging an apparently harmful link for a video sent by a friend on Facebook messenger.
Security researchers from Trend Micro have spotted a malicious Chrome extension, dubbed FacexWorm,which is spreading through Facebook Messenger and targeting users of cryptocurrency trading platforms to steal their accounts’ credentials and run cryptocurrency mining scripts.
“Our Cyber Safety Solutions team identified a malicious Chrome extension we named FacexWorm, which uses a miscellany of techniques to target cryptocurrency trading platforms accessed on an affected browser and propagates via Facebook Messenger.” reads the reportpublished by Trend Micro.
According to the experts, FacexWorm was first detected in late April and appears to be linked to two other Facebook Messenger spam campaigns, one that occurredin August 2017 and a second one that was launched in December 2017 to spread the Digmine cryptocurrency miner.
Experts recently observed a spike in FacexWorm activity, the malicious code was detected in several countries, including Germany, Tunisia, Japan, Taiwan, South Korea, and Spain.
FacexWorm implements several features, including stealing account credentials from websites, like Google and cryptocurrency sites, redirecting victims to rogue cryptocurrency sites, injecting cryptocurrency miners, and redirecting victims to the attacker’s referral link for cryptocurrency-related referral programs.
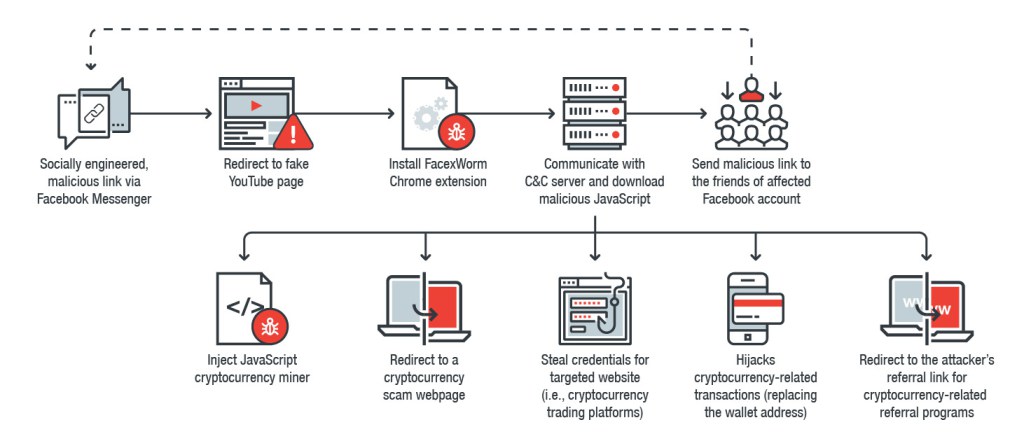
The following image shows the FacexWorm’s infection chain:
FacexWorm propagates by links over Facebook Messenger to the friends of an affected Facebook account to redirect users to fake versions of popular video streaming websites, including YouTube. The user is encouraged to download a malicious Chrome extension as a codec extension to continue playing the video and to grant all extended permissions to complete the installation, with this trick malware can have full control for any websites the user visits.
Currently the malicious extension only Chrome users, when the malware detects a different browser it redirects the user to an innocuous-looking advertisement.
“FacexWorm is delivered through socially engineered links sent to Facebook Messenger. The links redirect to a fake YouTube page that will ask unwitting users to agree and install a codec extension (FacexWorm) in order to play the video on the page. It will then request privilege to access and change data on the opened website.” continues the report.
Once FacexWorm Chrome extension is installed on the victim’s PC, it downloads more modules from its command and control server to perform other malicious activities.
“FacexWorm is a clone of a normal Chrome extension but injected with short code containing its main routine. It downloads additional JavaScript code from the C&C server when the browser is opened,” continues the report.
“Every time a victim opens a new webpage, FacexWorm will query its C&C server to find and retrieve another JavaScript code (hosted on a Github repository) and execute its behaviors on that webpage.”
Trend Micro detailed the malicious behaviors of the malware that include:
- Steal the user’s account credentials for Google, MyMonero, and Coinhive.
- Push a cryptocurrency scam.
- Conduct malicious web cryptocurrency mining.
- Hijack cryptocurrency-related transactions.
- Earn from cryptocurrency-related referral programs.