Experts killed tens of thousands of subdomains used by crooks to host the RIG Exploit Kit that were set up with a domain shadowing campaign.
GoDaddy and RSA Security, with the support of other security companies and researchers, have shut down tens of thousands of illegally established subdomains used by crooks to host the RIG Exploit Kit.
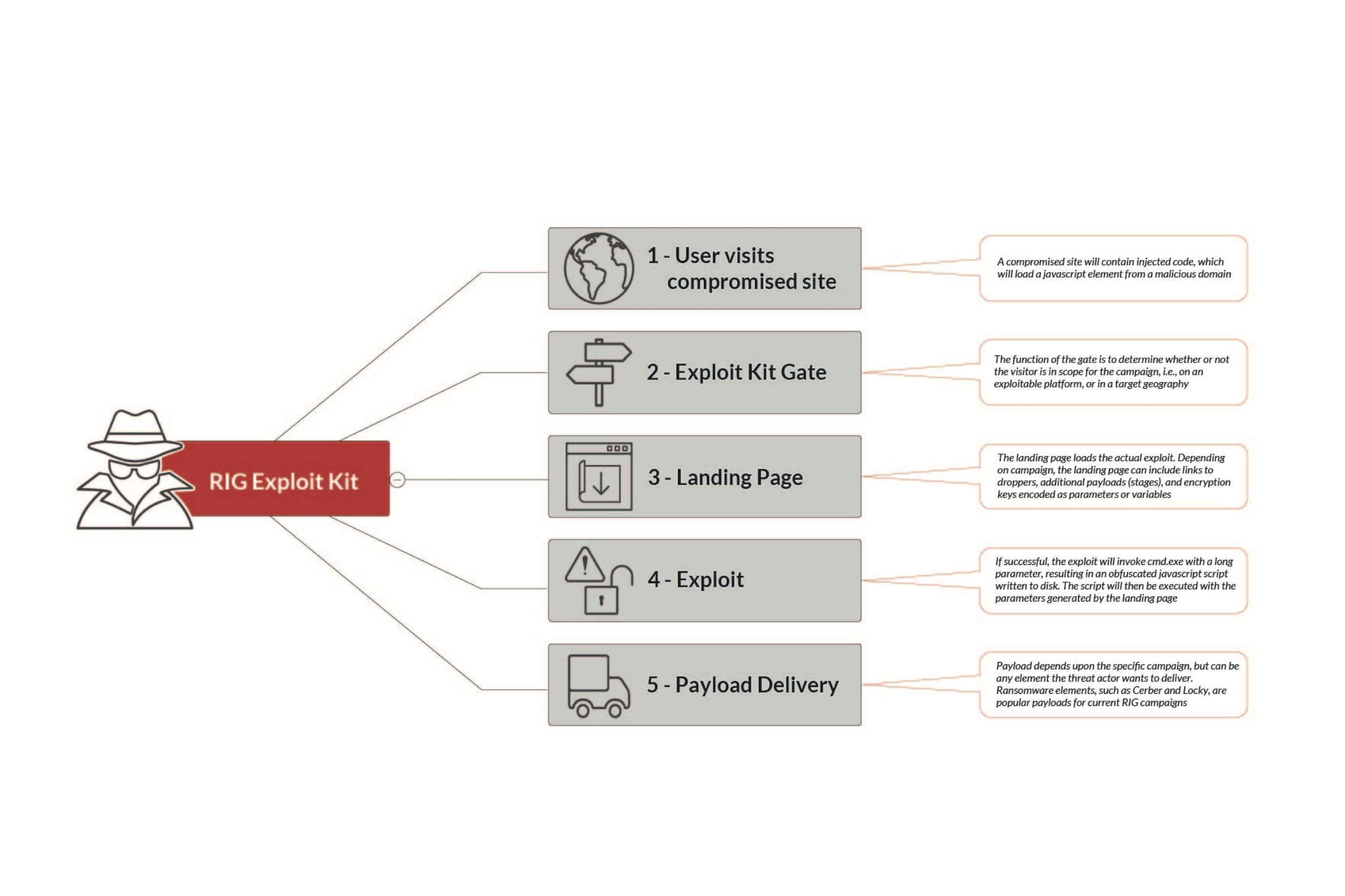
The RIG exploit kit is very popular in the criminal ecosystem, early this year security experts at Heimdal Security warned of a spike in cyber attacks leveraging the popular Neutrino and RIG EKs.

The cyber criminals set up the subdomains, most of them used GoDaddy as the primary domain registrar, by obtaining domain account credentials with phishing attacks (so-called domain shadowing).
“Domain shadowing is “a technique in which attackers steal domain account credentials from their owners for the purpose of creating subdomains directed at malicious servers”.” states RSA. “As a direct result of these efforts, tens of thousands of active shadow domain resources were removed from RIG, malvertising, and malspam operations.”
In March experts shut down the subdomains along with hundreds of IP addresses used by crooks to spread malware.
RSA Security published a detailed report titled Shadowfall on the RIG operation.
According to RSA hackers used a data-stealing malware as part of a phishing campaign to steal GoDaddy domain account credentials. Crooks used the account credentials to create new subdomains to use as gates in attacks to redirect visitors to IP addresses hosting the exploit kit.
The RSA researchers mapped domains to registrars and discovered that a most of them were registered with GoDaddy.
The RIG operation allowed the identification of 40,000 network subdomains and 2,000 IP addresses. According to RSA, the Shadow domains were kept alive 24 hours on average and DNS records were cleaned up before new shadow domains were created.
The researchers investigated four campaigns between February and March, two of them were spreading malware, including the Cerber ransomware and Dreambot banking malware.
RSA also helped GoDaddy in building some automation to monitor and detect shadowing attacks.
“The focus moving forward is to continue developing processes for at-scale detection and removal of malicious DNS records, as well as to integrate preventative measures into the domain modification data flow. As these efforts mature in their ability to prevent and disrupt shadowing, the direction will shift away from reliance of submitted indicators for ad-hoc remediation. Instead, they will depend on the analysis of internal datasets to identify and remove malicious records in an automated fashion.” concludes RSA.
“Success in these areas will minimize Time to Detection and Time to Remediation while significantly reducing the shadow domains’ lifespan. Architectural mitigations are also being evaluated for integration into accounts at high risk for domain shadowing. This path of action will keep GoDaddy accounts more secure and reduce the effectiveness of domain shadowing as a technique for malware distribution.”