An Indispensable Element of Cyber Risk Management Strategy
By Kaustubh Medhe, Head of Research and Intelligence, Cyble
As the COVID pandemic rages on and threatens to delay the restoration of normalcy, organizations have had to rapidly transition to a digital model of working to ensure operational continuity and maintain their competitive advantage. Experts claim that the pandemic has accelerated the adoption of digital ecosystems by nearly a decade, with companies rushing to embrace the cloud, implementing a mobile-first strategy, and employees working remotely. Unfortunately, this progressive trend has been marred by a disproportionate increase in the frequency and sophistication of cyberattacks, especially ransomware attacks on organizations, large and small alike. The consequences of this include cybercriminal groups stealing/destroying sensitive data, disrupting business operations, and further exposing the victims to unwanted media and regulatory scrutiny.
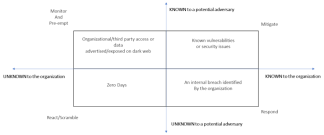
Surprisingly, Threat Actors routinely compromise even high-profile organizations with skilled cybersecurity staff, state-of-the-art cybersecurity technology, adequate security budgets, and demonstrably good cybersecurity processes. In fact, in many instances, the affected organizations were found blissfully unaware that they were breached and only came to know about it via a third party. This fact indicates that while organizations are very good at managing “known” risks and responding to attacks that they can “see,” they are often oblivious to the “unknown” attacks that fly undetected under their security radar. To quote Walter Johnson, one of the greatest baseball pitchers in sports history – “You can’t hit what you can’t see.”
These risks are referred to as ‘unknown knowns’ (blind spots or information that the organization is unaware of – but a potential adversary can exploit to their advantage). Organizations do have a way to overcome this blind spot, however.
Cybercriminals have been known to frequent the “darkweb” (the hidden part of the internet accessible via specialized browsers and networks to help preserve anonymity) to advertise and monetize the illegally obtained information through successful cyber-attacks. This information includes stolen access credentials (usernames and passwords) to the victim’s corporate network and business applications, banking accounts, or sensitive personal /business information stolen during a successful malware attack or a data breach. This information is procured by other cybercriminals who can leverage the compromised account access to either steal funds, exfiltrate sensitive data or launch another advanced cyber-attack (like a ransomware attack) on the victim organization.
Cybercriminals have also been observed discussing potential vulnerabilities that they have found in their target companies on various darkweb forums.
With specialized darkweb monitoring services, organizations can become aware of such vulnerabilities in their infrastructure and potentially compromised users or systems before their access credentials are abused or misused in follow-up attacks. Based on this intelligence, organizations can immediately take remedial measures such as resetting credentials, conducting a security assessment, or a forensic investigation to identify and remediate malware or vulnerabilities to minimize or eliminate the risk of an impending attack.
Leading organizations with mature cyber risk management practices have already been employing darkweb monitoring as a critical asset in their security monitoring arsenal for quite some time. Of late, they have also expanded the scope of darkweb monitoring to help manage their third-party/supply chain cyber risks. Some of the key applications of darkweb monitoring for third party risk management include –
- Identifying compromised credentials of their critical third parties or customers
- Identifying and assessing their data exposure in the event of a third-party data breach
- Assessing cyber risk exposure of a potential M&A target as part of due diligence
- Identifying their customer data in a third-party data breach and initiating Data Breach Notification processes as stipulated by various Data Protection Regulations such as GDPR
- Continuous risk assessment and cyber risk monitoring of critical vendors or business partners based on their data/access exposure on the darkweb
As the cyber threat landscape evolves, it is no longer sufficient to rely solely on enterprise security tools such as endpoint and perimeter security controls to safeguard organizational data. Organizations need to look beyond the perimeter to gain continuous visibility and insight into what their adversaries know about them and then remediate those issues before they can be exploited.
In this endeavor, darkweb monitoring has quickly emerged as a valuable tool in cyber defenders’ arsenals – something every security-conscious organization should consider including as part of their cyber risk management strategy.
About the Author
 Kaustubh Medhe, Head of Research and Intelligence, at Cyble is a seasoned cybersecurity and risk management professional with 20+ years of diverse experience in consulting, practice management, and cybersecurity operations. Before joining Cyble, Kaustubh gained extensive experience in successfully managing security service programs and engagements for several clients in the Insurance and Banking sector in India, the Middle East, and APAC.
Kaustubh Medhe, Head of Research and Intelligence, at Cyble is a seasoned cybersecurity and risk management professional with 20+ years of diverse experience in consulting, practice management, and cybersecurity operations. Before joining Cyble, Kaustubh gained extensive experience in successfully managing security service programs and engagements for several clients in the Insurance and Banking sector in India, the Middle East, and APAC.
Kaustubh can be reached online at https://in.linkedin.com/in/kaustubh-medhe-8963204?trk=public_post_share-update_actor-image and at our company website https://cyble.com/


