Digital identity is an extra layer of security needed to protect your organization’s document and workflows. Here’s how it works and why it matters.
By Filip Verreth, VP Product Management of eSign Solutions at Nitro, Inc.
The digital-first economy is rapidly evolving and, with more sensitive data being shared online, cybersecurity risks are escalating. It has never been more important for your organization to ask the question, “Do we really know who we’re doing business with?”
Digital identification has become an important component of cybersecurity initiatives and an enabler in the modern business transformation journey. It helps protect data, build trust and drive business efficiency. However, getting it right requires a strategic approach.
In this article, we’ll help you understand what digital identity means, why it is a business priority and what you need to know. It’s time to take full control of your electronic documents and eSigning workflows so you keep your organization safe and secure.
What is a Digital Identity?
A digital identity, or digital ID, is information that exists about an individual, organization and device online. There are many different sources from which a unique digital identity is formed, from emails and passwords to online search history. With organizations investing more in digital tools and technology and cyber threats on the rise, creating a framework for managing digital identity has never been so important.
Is Digital Identification and Authentication the Same Thing?
No. Digital identification is what an individual, organization or device claims to be. Authentication, on the other hand, is the process of verifying these claims.
In the eSigning process, for example, the user must be fully authenticated before a signature can be obtained. The authentication process can vary widely. Examples include:
- Login and password combinations (including Single Sign-On)
- One-time passwords (via SMS and email)
- Mobile identities
- Bank authentication
- Biometric authentication
5 Reasons Why Digital Identity Should be a Top Business Priority
Having a strategic approach to digital identity can unlock considerable business value. Let’s look at some of the top benefits for your organization:
Effortless Compliance: Meet AML (Anti-Money Laundering) and KYC (Know Your Customer) requirements that place a legal emphasis on identity verification.
Minimize Risk: Reduce opportunities for manual error and breaches of conduct through robust security measures.
Improve Customer Journeys: Smart digital identity management will build trust and customer satisfaction by prioritizing privacy and data protection.
Fraud Prevention: Detect and eliminate fraudulent activity across key touchpoints.
Increase Efficiency: Save time by replacing manual activities and the need for face-to-face interaction with digitally automated processes.
Digital Identity for Your Organization: What You Need to Know
When it comes to managing your documents and eSigning workflows, there are important points you need to consider:
Each eSignature Method Offers Different Levels of Digital Identity Assurance
An important fact to point out is that electronic signatures and digital signatures are not the same thing. Though often used interchangeably, digital signatures rely on cryptography-based technology that provides an extra level of security and integrity for the document. They use the standards and procedures of Public Key Infrastructure (PKI) to sign electronic data.
Digital signatures comply with the most stringent regulatory requirements and offer more protection for your documents and eSigning. This type of signature works well for sensitive information including financial records, healthcare documents or real estate contracts.
On the other hand, an electronic signature, or eSignature, can be the image of your signature pasted in a Word document or even your mail signature.
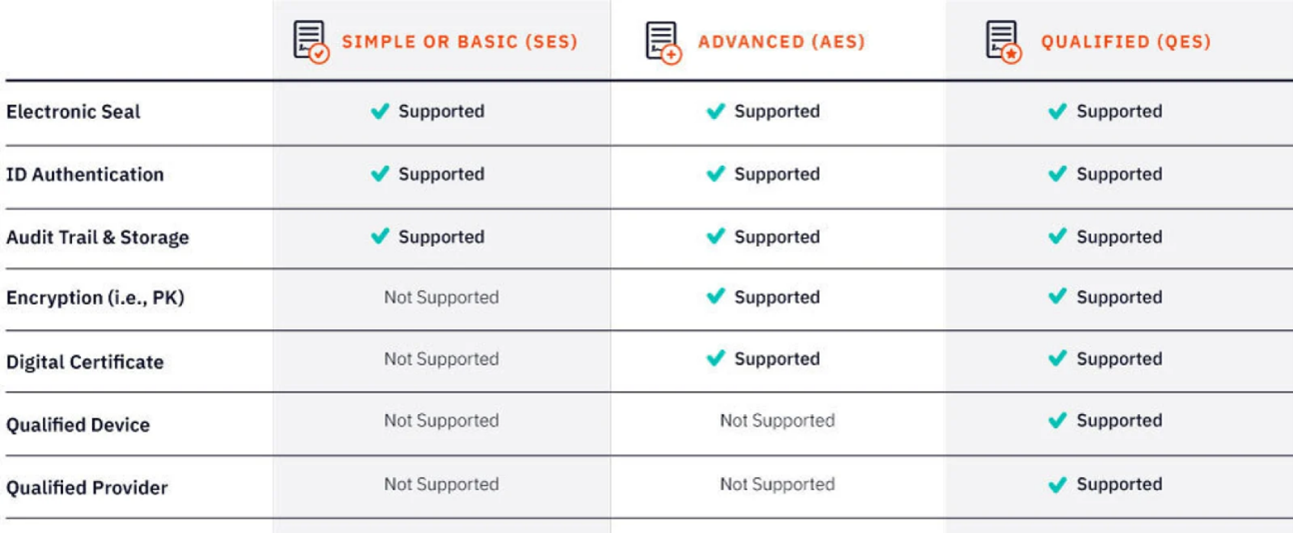
The 3 Types of eSignatures Also Have Different Levels of Security
There are 3 different methods of eSignatures as identified by The European Union’s Electronic Identification, Authentication and Trust Services (eIDAS).
- Simple Electronic Signatures (SES)
- Advanced Electronic Signatures (AES)
- Qualified Electronic Signatures (QES)
In most cases, only Advanced and Qualified Electronic Signatures are digital signatures as they provide greater signer identification and authentication. So, if you’re in a highly regulated industry that handles sensitive data, or you just want greater assurance across your documents and eSigning, you’ll need to choose a method that offers the highest level of security and digital identity protection.
What To Consider When Choosing a Digital Identity Vendor
When selecting any vendor for your organization, meeting business requirements across key focus areas is critical for success. This checklist can help you identify important digital identity capabilities, so your organization can stay one step ahead:
- Can the solution give you the flexibility to enable any secure identification method?
- Does it comply with the regulations relevant to your organization and the countries you are operating in?
- Will it offer enough coverage for your business needs?
- Does it cover your Know Your Customer (KYC) and Anti-Money Laundering (AML) needs?
- Will it easily integrate into your business applications?
The Key to Getting Digital Identity Right
Digital identity should be a core element of your business and security strategy. Not only can it be a powerful solution in your cyber resilience toolkit, without it, you can never be 100% confident who you’re doing business with.
To protect your business, carefully align digital identity initiatives and partners with your organization’s overarching objectives. Define your expectations and the impact you want it to have on your digital transformation.
Remember, digital identity shouldn’t be siloed. Educate your stakeholders and create a collaborative approach so teams understand the important role they play in this journey.
About the Author
 Filip Verreth, VP Product Management of eSign Solutions at Nitro, Inc. Filip Verreth joined Nitro from Connective, where he was the CIO. He is currently the VP of Product Management, leading the team working to improve eSignature and identity products. His passion for technology and compliance standards drives Nitro’s products’ progress and innovation.
Filip Verreth, VP Product Management of eSign Solutions at Nitro, Inc. Filip Verreth joined Nitro from Connective, where he was the CIO. He is currently the VP of Product Management, leading the team working to improve eSignature and identity products. His passion for technology and compliance standards drives Nitro’s products’ progress and innovation.
Nitro, Inc. company website: https://www.gonitro.com/


