Security experts from Melani published a detailed technical report about the strain of Turla used in the cyberespionage attack against the RUAG firm.
A few weeks ago I reported about the cyber espionage attack on the Swiss Defense Department that was revealed after a presentation on cyber espionage to the Federal Intelligence Service. The cyber attack was announced by the Swiss defense minister Guy Parmelin that explained that the Federal Department of Defence, Civil Protection and Sports was targeted by hackers.
It was not possible to attribute the attack, anyway, experts have found many similarities with another cyber attack that hit the government-owned Ruag firm.
The Ruag firm is a technology company, based in Bern, that supplies the country’s military with munitions. Threat actors exfiltrated data from the systems of the firm, which is wholly owned by the Swiss government, though the extent of the theft was unknown.
Below a portion of the interview released by Parmelin to the Swiss daily Tages-Anzeiger.
“According Tagesanzeiger.ch/Newsnet-Informationen hang the attacks against the VBS with a major cyber attack on the defense group RUAG together, behind Russia is suspected. Is become active in this matter, the Federal Council?
The Federal Council has been informed. He has proposed several measures that are now being implemented. The Attorney General has instituted a process.
What were these attacks?
The attacks were of industrial espionage. Because Ruag working for the army and the federal government and 100 percent of the federal government is one, it is very important for us to minimize risks.”
Parmelin pointed out industrial espionage has the root cause of the cyber attack and said his department was able to mitigate the attack and restore normal operations.
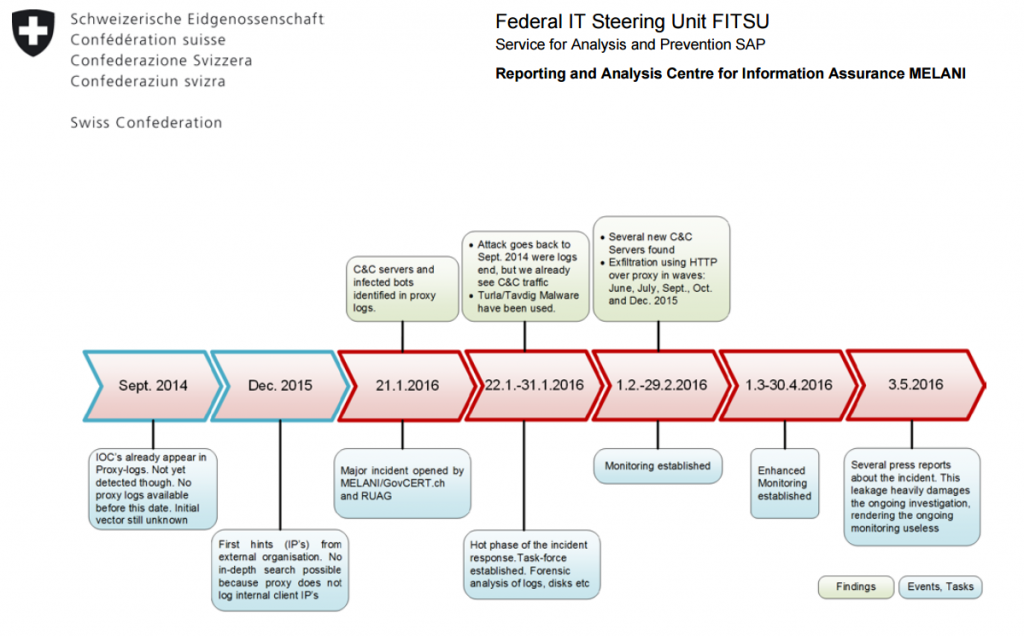
Now the Reporting and Analysis Center for Information Assurance (MELANI) has published a detailed Technical Report about the Malware used in the Cyberespionage against RUAG.
The Federal Council has decided to disclose the details of the cyber attack in order to give organizations the chance to check their networks for evidence of the attack.The threat actors have been using a malicious code linked to the Turla family, threat actors behind the threat, dubbed Turla APT, hit more than 500 victims in 45 different countries worldwide, government agencies, military and diplomatic entities are privileged targets of the group.

The strain of Turla used in the attack against the RUAG did not implement rootkit functionality, but relies on sophisticated obfuscation mechanisms to stay under the radar. It was a surgical attack that compromised only the systems the attackers were interested in in implementing various measures, such as a target IP list and extensive fingerprinting before and after the initial infection.
Once the attackers found an entry point in the target network, they moved laterally compromising other devices in the architecture, this was possible by targeting directly the active directory.
The malicious code contacted its C&C servers through HTTP requests, it received from them commands and also new malicious payloads to execute. The experts noticed that only some of the infected machines directly contacted the C&C servers, instead, they received instructions and communicated through named pipes.“The malware sent HTTP requests to transfer the data to the outside, where several layers of Commandand-Control (C&C) servers were located. These C&C servers provided new tasks to the infected devices. Such tasks may consist of new binaries, configuration files, or batch jobs. Inside the infiltrated network, the attackers used named pipes for the internal communication between infected devices, which is difficult to detect.” states the report published by Melani. “This way, they constructed a hierarchical peer-to-peer network: some of these devices took the role of a communication drone, while others acted as worker drones”
Victim evaluation: During this phase, the attacker tries to get as much information about the target as possible. It is a preparation for the actual attack and covers at least the IP ranges, platforms and some usage patterns of their users. It is important for him to place the right waterholes and to be able to filter out unwanted victims from the actual targets. This phase is divided into several sub phases, not all need to be necessarily be in place: • Passive information gathering • Active scanning • Preparing waterholes
Infecting: The infection phase consists of a fingerprint of the victim in order to find the best suited infection method (using an appropriate exploit or a social engineering technique). It has the following sub phases: • Activating waterholes / sending spearphishings • Fingerprinting: This is most often done using JavaScript • Exploiting: Depending on the target, a suitable exploit is chosen. If this is not feasible, a social engineering approach is applied.
Active Infection: The attacker is now in the network. There are several sub phases here: • Trojan supported Reconnaissance: We often see an initial reconnaissance tool being placed, performing additional reconnaissance actions from within the network of the victim. This tool has not many capabilities, but can be replaced by a more powerful malware at any time. • Gaining Persistence: If the recon tool has been placed successfully and has sent out enough information, it is replaced by the actual malware with more functionality and deeper persistence in the system and the network. • Lateral Movement: The attacker begins to move laterally in order to gain access to the information he is interested in. Lateral movement is often done by using “normal” tools that are also used for managing systems. The lateral movement also comprises the collection of credentials, as well as the elevation of privileges. • Data Exfiltration: As soon as the attacker begins to steal data, he must transport it outside of the network without being discovered. This is often done by first compressing the data and then sending it out, piece by piece.
The experts confirmed that it is quite difficult to estimate the damage caused by the hacking attack. The analysis of the proxy logs revealed periods of intense activities in alternate with very few activities. The report published by Melani also includes recommendations and countermeasures to defeat this Turla variant and promptly identify the presence of attackers, the authors also invite victims to share information about the attack.

Who is behind Turla?
It is very hard to discover the real identity of the attackers, the report itself did not make speculation on the alleged culprits.
Going back in March 2014 the researchers at BAE Systems Applied Intelligence spotted a Russian cyber espionage campaign codenamed as SNAKE that targeted Governments and Military Networks.
The attackers behind the operation SNAKE penetrated highly secured systems all around the world, but most interesting revelation is that the Uroburos rootkit recently discovered by German security firm G Data Software was just one component of the overall SNAKE campaign.
For the SNAKE campaign the attackers used various pieces of malware, Western intelligence officers have found another spyware, dubbed Turla, used to infect government network all over the world.
Researchers linked the malware Turla to popular cyber espionage campaign Red October discovered by Kaspersky in 2013 that hit government, military and diplomatic organizations all around the world.
Following this chain of events and the discoveries made by various security firms we can speculate that behind the Turla malware there are Russian nation-state hackers.
However, we cannot be sure that Russian hackers have now targeted the Ruag firm too.
I suggest you to give a look to the report, it is full of interesting data.
https://www.surveymonkey.com/r/secbloggerwards2016
Thank you
Pierluigi