Demystifying the requirements and identifying the right solution with necessary ingredients
By:Lalit Shinde, Head of Partnerships and Business Dev., Seceon Inc.
In today’s digital era, almost all organizations whether large, medium or small are looking for comprehensive cyber security solution that would stop any cyber security attack and protect them from any damage. Most small and medium organizations are relying on trusted managed service providers (MSPs) to recommend and provide these solutions, while most large organization may have in house security experts or trusted managed security service providers (MSSPs) to implement these. These MSPs and MSSPsare looking for the cyber security frameworks including the most popular NIST framework created by US govt. to improve their security posture and deploy the solution(s) that help fulfill this framework.
On a cyber security vendor side, there is also a sudden rush within the last few years to create a one-stop solution that caters to comprehensive cyber security so that they can be preferred vendor of choice with managed security service providers and with large enterprises. Most next-gen firewall and anti-virus companies are buying other innovative products to fillthe gaps and create this one stop solution, also called ‘Defense in Depth’ product lines. However, ‘Defense in Depth’ approach is flawed and usually leads to much higher cost without solving the fundamental requirements of comprehensive cyber security.
So,what is the primary goal of “Comprehensive Cyber Security for Digital Era”? It’s a) to protect the organization from all known and unknown cyber-attacks and b) if an attack happens, to proactively detect it at an early stage and contain or eliminate the attack to minimize the damage. In short “Stop the Data Breach from causing any damage to the organization” – whether that damage is legal, financial, competitive, and/or nation-state based.
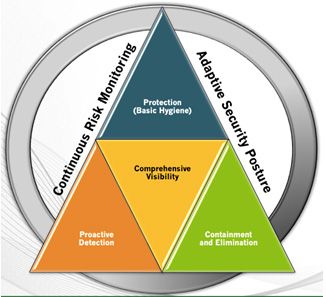
Figure 1: Requirements of Comprehensive Cyber Security
Let us look at what are the basic requirements of “Comprehensive Cyber Security”. The key requirements start with comprehensive visibility – if you can’t see the assets, the users, the traffic, and the vulnerabilities; you can’t protect the organization from attacks originating from them. Basic Security hygiene is important from protection from most common and known attacks perspective, but it’s not sufficient. Proactive detection based on behavioral science to detect anomalies has become the need of the hour. However, most machine learning and behavioral science-based solutions produce lot of false positives and create an alert fatigue. It’s very important to also have advance correlation engine, which correlates historical situational context along with machine learning anomalies to reduce the false positives and accurately find the real attacksrather than getting bogged down by least important issues. Once the attack is detected, the solution should also provide automated real-time response built in. The organization cannot rely on human intervention by Security Operations Center (SOC) analyst to analyze it before responding. The solution should respond automatically and stop the threat. The SOC analyst can analyze it and adjust later, but the attack needs to be stopped immediately in an automated manner. Furthermore, this solution and framework has to be continuously adjusted and adapted to changing posture of the organization in digital era where more content and applications are moving to the cloud and employees are preferring to work from anywhere, using any smart device to access the organization’s data which has to be omnipresent.
However, the ‘Defense in Depth’ model that most cyber security vendors are building through acquisitions of various silo productsis not addressing the requirements of the ‘Comprehensive Cyber Security’. It’s making the overall solution very costly because of the multitudes of silo products required to achieve it and the increased complexity to manage them. Moreover, it seldom actually achieves the stated primary goal, ‘To stop the data breaches’ at any cost.
So, let us look at what a ‘Comprehensive Cyber Security’ solution should have. First and foremost you need a fast-big-data streaming platform. But don’t confuse this with handling of large data-lakes. There is a lot of confusion, most vendors when they talk about fast big data, they think that it’s storing, ingesting and analyzing the petabytes of data using data-lake. This is a flawed strategy. You don’t want results after few hours or days. You want them in real-time, so you need fast big data streaming platform that produces results in real-time within seconds.
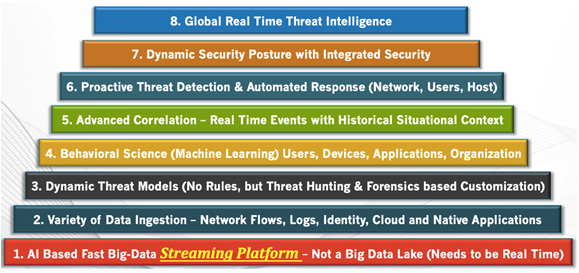
Figure 2: Comprehensive Cyber Security Solution Ingredients
Ingesting data from variety of datasources is a key to both from comprehensive visibility perspective and also from changing organization landscape as well. More and more organizations are adopting cloud and mobile world with smart devices. With changing landscape, the solution mandates Dynamic Threat Models (DTM), which automatically adapt to the change. Having inbuilt DTM engineis far better than relying on security analysts to write the correct set of rules and then keep on fine-tuning it to capture sophisticated attacks. Such a method is clearly error prone and handles the attacks after the fact. Some customization is important, but most of the attacks related threat models have to be in built into the solution.
Machine learning (ML) and Artificial Intelligence (AI) based behavioral science has a critical role to play in finding all sorts of anomalies in application, devices and users behavior, but it could lead to massive alert fatigue. Most Security Information and Event Management (SIEM) solutions have tried to retrofit ML algorithms into existing platforms and this strategy definitely leads to alert fatigue for the end user. That’s why an advanced correlation engine that correlates the anomalies with situational context and historical context is important to reduce the false positives and eliminate alert fatigue. Also any built-in threat models and ML/AI based engines need to adapt itself dynamically to changing organization posture with dynamic thresholds and changing global threat intelligence with dynamic periodic feed. Finally, the solution should not only proactively detect but also contain or eliminate the attacks by providing actionable intelligence and automated infrastructure to orchestrate and apply right set of policies.
Overall the comprehensive cyber security for digital era requires a platform that is built grounds up with the key ingredients required to protect any size organizations. Organizations and service providers must evaluate the vendors against these principle ingredients and requirements before they put their money on it.
About the Author
Lalit Shinde, Head of Partnerships and Business Development, Seceon Inc.
Lalit currently leads the strategic sales partnerships and business development for Seceon. He is an Industry Leader with over 24 years of expertise in Strategy, Product Management. Product Development and Business Development. He has a great track record of identifying market opportunities, developing breakthrough products and driving market share from product introduction to significant revenue. Before joining Seceon, Lalit was in leadership position with Juniper Networks in Strategy Planning, Product Management and Product Development roles. His technology expertise includes Network Security, Automation, Control and Data plane APIs, Network Orchestration and Controllers, SDN/NFV, Broadband and Business Edge Services, Routing, Switching and Security Products and Technologies. At Juniper, Lalit got the BNG router introduced into major Tier1 SPs in Europe, Americas and APAC region, developed product strategy with customer focus and won several multi-million $ deals. As an Engineering Manager, he also managed and developed the BNG team globally from scratch. Prior to Juniper, Lalit has worked with Cadence Design Systems and Texas Instruments as Lead architect in developing industry recognized award winning products. He received his MBA from NYU Stern School of Business. He also has MS in Computer Science from IISc, Bangalore and BS in Electronics and Telecommunications from VJTI, Mumbai.Lalit can be reached online at [email protected]and at our company website www.seceon.com.

