The Federal Bureau of Investigation report reveals that Business email compromise scams caused losses to businesses for 5 billion dollars over four years.
Business email compromise (BEC) continues to be a profitable attack technique for crooks and a serious threat to businesses.
The FBI has published data related to this specific criminal practice, and financial figures are astonishing.
The fraud scheme is very simple, busy employees receive a request to transfer funds by representatives of high management of their company.
The request could be sent by an attacker that either compromises a company’s email accounts or sets up a phishing message that submits a fake invoice to the victim from someone posing as a contractor or business partner.
It is clear that businesses and personnel using open source e-mail are most targeted by Business Email Compromise, in many cases the criminals spoofed e-mails of individuals within enterprises who are entitled to submit such payment requests.
Individuals responsible for handling wire transfers within specific companies are privileged targets of criminals which compose well-worded e-mail requests for a wire transfer.
The attacker behind Business Email Compromise scams shows a deep knowledge of their victims, their requests are proportional to the economic capabilities of the target and of the specific individual used as the sender of the request. The criminals sent e-mails concurrently with business travel dates for executives whose e-mails were spoofed.
The statement issued by the FBI in 2015 reported three different versions of the Business Email Compromise based on complaints received since 2009:
Version 1
A business, which often has a long standing relationship with a supplier, is asked to wire funds for invoice payment to an alternate, fraudulent account. This particular version has also been referred to as “The Bogus Invoice Scheme,” “The Supplier Swindle,” and “Invoice Modification Scheme.”
Version 2
The e-mail accounts of high-level business executives (CFO, CTO, etc) are compromised. The account may be spoofed or hacked. A request for a wire transfer from the compromised account is made to a second employee within the company who is normally responsible for processing these requests. This particular version has also been referred to as “CEO Fraud,” “Business Executive Scam,” “Masquerading,” and “Financial Industry Wire Frauds.”
Version 3
An employee of a business has his/her personal e-mail hacked. Requests for invoice payments to fraudster-controlled bank accounts are sent from this employee’s personal e-mail to multiple vendors identified from this employee’s contact list. The business may not become aware of the fraudulent requests until they are contacted by their vendors to follow up on the status of their invoice payment.
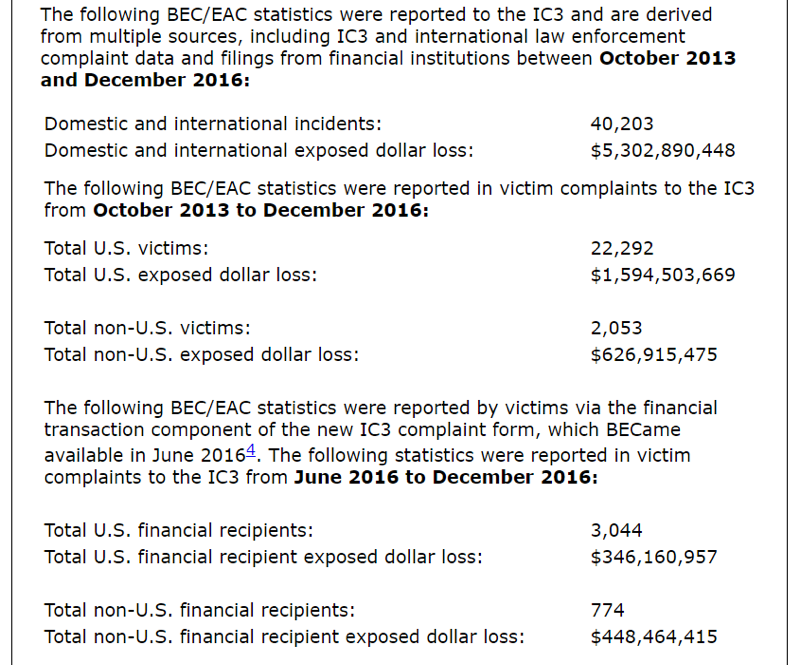
Data provided by the FBI is related to BEC crimes occurred between 2013 and December 2016, cyber criminals have earned $5,302,890,448 from 40,203 cases involving US and international businesses.
The FBI also confirmed that BEC scams continue to increase, 2,370 percent over the past year.
The FBI set up a reporting site for BEC scams and observed that between June and December of last year, US businesses reported losses of $346,160,957 in 3,044 attacks.
In the same period, non-US businesses reported losses of $448,464,415, but the overall number of BEC scams was much lower: 774. These data confirm that BEC scams are an emergency for US firms.
“The BEC/EAC scam continues to grow, evolve, and target small, medium, and large businesses. Between January 2015 and December 2016, there was a 2,370% increase in identified exposed losses. The scam has been reported in all 50 states and in 131 countries. Victim complaints filed with the IC3 and financial sources indicate fraudulent transfers have been sent to 103 countries.” states the Alert published by the FBI.
Based on the financial data, Asian banks located in China and Hong Kong remain the primary destinations of fraudulent funds; however, financial institutions in the United Kingdom have also been identified as prominent destinations.”

Stolen funds were mostly diverted to Asian banks located in China and Hong Kong, but Feds also confirmed that the use of British banks is on the rise.
The FBI report highlights that many recent attacks were preceded by a malware-based attack, mainly ransomware, likely because the crooks evaluate the ability of the firm to pay.
The FBI confirmed an increase of Real estate scams (+480 percent respect 2016).
The report also suggests company further security measures to prevent Business Email Compromise attacks, including the implementation of a two-step verification process. For example:
- Out-of-Band Communication: Establish other communication channels, such as telephone calls, to verify significant transactions. Arrange this two-factor authentication early in the relationship and outside the e-mail environment to avoid interception by a hacker.
- Digital Signatures: Both entities on EACh side of a transaction should utilize digital signatures. This will not work with web-based e-mail accounts. Additionally, some countries ban or limit the use of encryption.
Give a look at the report, it is full of interesting data.