The Android full-disk encryption can be easily cracked with a brute force attack, hundreds of millions of Android mobile are at risk.
Bad news for Android users that want to protect their data by enabling full-disk encryption (FDE) on their mobile devices.
The Android full-disk encryption can be easily cracked with a brute force attack, this implies that potentially hundreds of millions of Android mobile are exposed to the risk of hack.
The security researcher Gal Beniamini that analyzed the implementation of the Android full-disk encryption made the disconcerting discovery.
Unfortunately, there may not be a full fix available for current Android mobile devices in the market.
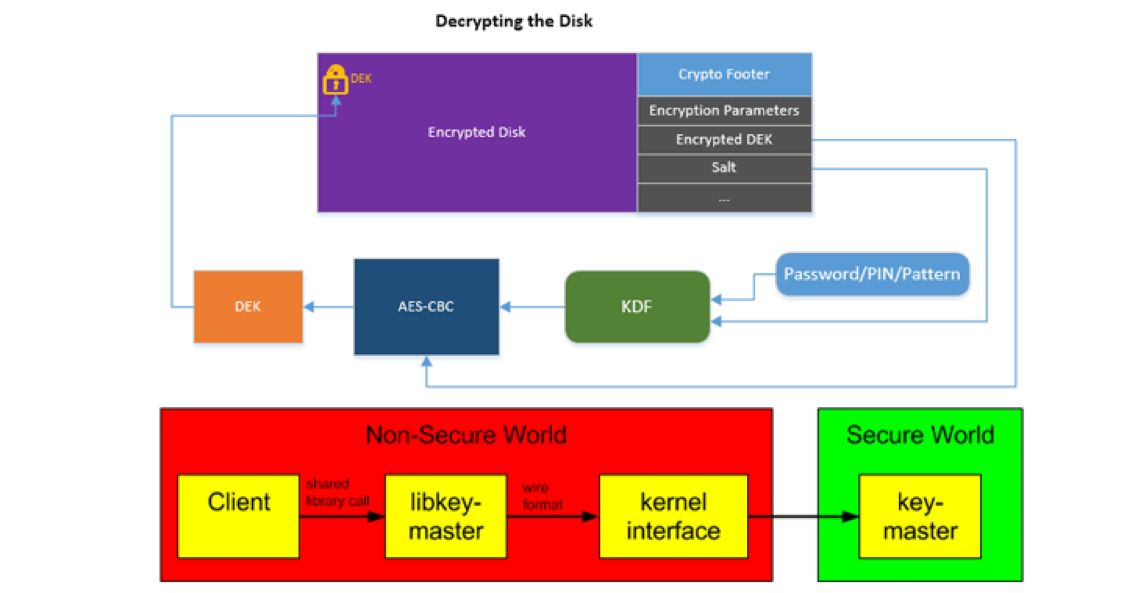
By enabling Android full-disk encryption, the user’s data on a mobile device is encrypted every time it is written to the disk, a process that leveraged on the user authentication code. Every operation on the data will request user enters his password.
Beniamini has discovered two security issues (CVE-2015-6639 and CVE-2016-2431) that reside in the way Android manages full disk encryption.
The expert published a detailed step-by-step guide on how to bypass the encryption on Android devices powered by Qualcomm Snapdragon processors and also the exploit code on GitHub.

The expert noticed that despite Qualcomm protect critical functions like encryption running them in the Snapdragon TrustZone, it is possible to exploit an Android security vulnerability to expose the keys from TrustZone.
Qualcomm runs a small kernel in TrustZone to implement the QSEE (Qualcomm Secure Execution Environment), a Trusted Execution Environment for running of small apps outside the main Android operating system. KeyMaster is also a QSEE app.
The KeyMaster also runs in the QSEE environment.
Beniamini demonstrated that an attacker can exploit a vulnerability in the kernel of the mobile device to load its version of QSEE app inside this secure environment, then by exploiting privilege escalation flaw it could compromise the QSEE environment and all the apps running in it, including the keys generated for the Android full-disk encryption.
Once accessed the key, the attacker could run a brute-force attack to access user password, PIN or lock, cracking Android’s full disk encryption.
The expert reported the following implications of this finding:
- The key derivation is not hardware bound. Instead of using a real hardware key which cannot be extracted by software (for example, the SHK), the KeyMaster application uses a key derived from the SHK and directly available to TrustZone.
- Qualcomm and OEMs can comply with law enforcement to break Full Disk Encryption. Since the key is available to TrustZone, Qualcomm and OEMs could simply create and sign a TrustZone image which extracts the KeyMaster keys and flash it to the target device. This would allow law enforcement to easily brute-force the FDE password off the device using the leaked keys.
- Patching TrustZone vulnerabilities does not necessarily protect you from this issue. Even on patched devices, if an attacker can obtain the encrypted disk image (e.g. by using forensic tools), they can then “downgrade” the device to a vulnerable version, extract the key by exploiting TrustZone, and use them to brute-force the encryption. Since the key is derived directly from the SHK, and the SHKcannot be modified, this renders all down-gradable devices directly vulnerable.
- Android FDE is only as strong as the TrustZone kernel or KeyMaster. Finding a TrustZone kernel vulnerability or a vulnerability in the KeyMaster trustlet, directly leads to the disclosure of the KeyMaster keys, thus enabling off-device attacks on Android FDE.
Beniamini is working with both Qualcomm and Google to solve the issue, but the problem might require significant hardware modification to be solved.
Let me suggest to give a look to the Beniamini analysis, it very interesting.