By Ankit Rajpurohit
- Data protection on the Internet
Our data is collected, stored, analyzed, sold, and exchanged like never before. And we should not forget that they are often stolen and abused.
Data has become a “currency” for many digital services that we receive “for free. Instead of currencies, people pay by sharing their data across countless applications. This trend of data as currency concerns every part of our lives – networked homes, connected cars, health and fitness management, map and traffic tools, online shopping. Consumers do not trust companies in terms of their data, but they do not know what to do about it.
Given the numerous excesses and cases of data leaks that filled the headlines, our position is that you need to start an open conversation with your consumers about how you use and protect their data.
That almost always triggers a bigger debate. How do we do that? What about data and privacy? How do we strike a balance between openness and sharing too much information?
For many brands, this may be the first situation in which they will have to work deeply on reputation and crises or problems. Companies may witness fans of their brand turn into “techruptors” – a pioneering audience that research shows will be at the forefront of the demand for change in the way companies operate and treat them. So we advise you to be proactive, inform yourself and prepare for the coming changes, and thus increase the chances of keeping the “techruptors” as your allies and fans.
- Misuse of personal data on the Internet
The expansion of social networks also has a “dark side” – there is a noticeable increase in criminal activities aimed at users. We are witnessing a qualitative and quantitative expansion of social networks. This expansion, however, also has a “dark side” – there is a noticeable increase in criminal activities directed at users.
Privacy is the cancer-wound of online social networking. Although it is not possible to say that all services on the Internet put privacy at the forefront, in social networks, privacy is most drastically, most concretely, and most often violated. Users themselves post personal information, data, and material that belongs to the private domain, and then share it with other users. In this way, they unknowingly and directly provide an opportunity for their data to be misused.
The user’s privacy is violated by the very publication of any information on the social website because it automatically belongs to the company and remains stored on its servers even when the user closes the account.
 By accepting strangers as friends on social networks, the user risks that his data, which he shares only with friends, will be used for various purposes. Private data such as e-mail addresses can reach spam lists so that the user receives e-mail of his own free will, which is usually of a commercial or propaganda nature. Visiting suspicious links on social networks, for example, puts the user at risk of becoming infected with “harmful” software, exposing the data to the public, and becoming a subject of fake multimedia content.
By accepting strangers as friends on social networks, the user risks that his data, which he shares only with friends, will be used for various purposes. Private data such as e-mail addresses can reach spam lists so that the user receives e-mail of his own free will, which is usually of a commercial or propaganda nature. Visiting suspicious links on social networks, for example, puts the user at risk of becoming infected with “harmful” software, exposing the data to the public, and becoming a subject of fake multimedia content.
Bearing in mind that most, if not all social networks are based on economic business principles, the technical platform of social networks is designed to collect from users the data necessary to meet and communicate with others, but also data that are segmented and used in filtering. marketing purposes.
It is noticeable that personal data from social networks are used to realize the initial stages of a certain criminal activity, while the sequel is realized classically, in the real world.
In this context, social networks are used to find collaborators and perpetrators of criminal activity, to recruit victims to prepare the crime, to gather relevant information, to assist in carrying out certain activities, to provide funds and the like. With the advent of social networks and the spread of electronic transaction services, criminals have, so to speak, begun not only to innovate methods for committing fraud but also to automate personal data collection techniques to make as much money as possible.
Cybercriminals use social engineering and phishing techniques to access the victim’s personal information. In this way, victims can suffer significant financial losses or, in more serious cases, even the loss of “electronic identity”, which is used for criminal purposes. The damage caused by data theft, therefore, should not be expressed only in financial loss but also in the loss of psychological integrity of personality, reputation, and credibility.
Users of social networks, due to the lack of education regarding the dangers to which they are exposed, recklessly leave information and multimedia content on their profiles that can be misused by differently motivated Internet users. In addition to being at risk of violating personal privacy and abusing private content, users are at risk of political or ideological manipulation.
The information posted on a social network can be misused by a criminal. Users, unaware of the dangers, leave information about their residential address, telephone numbers, information on whether they live alone or in a community, etc.
- How to get more secure codes
When we think about the privacy of our data, the first thing that comes to mind should be the password. Why? Because, in essence, the classic symmetric encryption is reduced to the code that the user enters and the data to which that code is applied using a certain algorithm a finite number of times. Let’s look at where we rely on codes today to protect ourselves from attackers and preserve privacy. First, we all use email, then social networks, maybe we are active on forums or use one of the cloud storage services, there is also access to our computer or phone, wireless (Wi-fi) network to which we are connected, et cetera. The list can be tediously long, and you have to take care of all these codes to access a particular account.
The Internet user has more than 10 different accounts, that number of exact codes is not easy to remember, and it can be especially difficult to remember which code is for which account. To make everyday life easier for the average user, there are password managers in the cyber world.
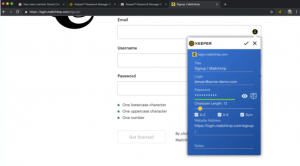
More importantly, there are those among them who are open source. Password managers, like Keeper Password Managers, will generate a random password/phrase of the desired length and security for your account, storing it in an encrypted database with other accounts. The database of all your accounts is encrypted with one code that you must remember. The advantage of the Keeper Password Manager, which you can read more about here, is that you remember one password instead of each account separately. There are also network password managers who synchronize the encrypted password database with a network server. That way, if you lose your device where you kept the passwords, you can still access your passwords stored on the server. Redundancy of all your ciphers is really necessary, especially if you are not good at remembering ciphers. How you generate and where you store the codes is definitely up to you.
Using secure passwords is not difficult, and programs like password managers make it as easy as possible. It’s definitely worth a little effort around your ciphers, not because we’re hiding something, but so we don’t get a headache when some hacker breaks in.
About the Author
 Ankit Rajpurohit is a tech lover and enthusiast who prefers to write about security steps, internet protection, and how to prevent your devices from hackers and potential harm. His main goal is to help people, through his articles, to upgrade their online protection.”
Ankit Rajpurohit is a tech lover and enthusiast who prefers to write about security steps, internet protection, and how to prevent your devices from hackers and potential harm. His main goal is to help people, through his articles, to upgrade their online protection.”