Protecting users against modern, invisible cyber threats
by Babur Khan, Technical Marketing Engineer at A10 Networks
A security strategy is only as strong as its weakest point. No matter how extensive your network defenses are, if there is even one blind spot, you are still vulnerable to attacks. This is true even for the Zero Trust model, at the core of modern cybersecurity. Fortunately, there is a way to fix it.
Zero Trust Model: The Perfect Security Strategy…with a Catch
Zero Trust security / Zero Trust model has become a critical element of network defense. Its rise has been driven by the way traditional concepts of secured zones, perimeters, network segments—even “inside” and “outside”—have been rendered outdated by the modern cyberthreat landscape. After all, you can’t count on walls to keep you safe from insider attacks by people with legitimate access, prevent multi-level attacks designed to bring networks down, or stop lateral movement during the course of an attack.
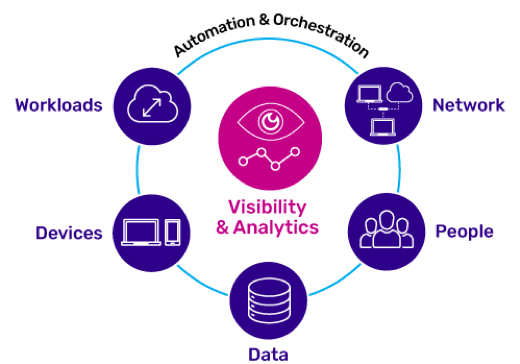
- The Zero Trust model responds to these challenges by adopting the approach of “trust nobody”—inside or outside the network. Cybersecurity strategies are redesigned accordingly along four key principles:
- Create network micro-segments and micro-perimeters to restrict east-west traffic flow and limit excessive user privileges and access as much as possible.
- Strengthen incident detection and response using comprehensive analytics and automation.
- Integrate solutions across multi-vendor networks with ease, so they can work together seamlessly, enabling compliance and unified security. The solutions should also be easy to use so that additional complexity can be removed.
- Provide comprehensive and centralized visibility into users, devices, data, the network, and workflows.
This sounds good in principle. Even the name “Zero Trust Security” is reassuring, with absolute terms that suggest absolute protection. But there is a catch: The Zero Trust model works only when you have full visibility into people and their activities. If something is invisible, there is no way for you to ensure that it does not pose a risk. And that is true for the vast majority of network traffic thanks to the widespread use of encryption.
Zero Trust Model / Zero Trust Security Blind Spot
Encryption is now ubiquitous across the internet. Google reports that over 90 percent of the traffic passing through its services is encrypted, and the numbers are similar for other vendors as well. This trend has been great for privacy—but it is devastating for security, whether you are implementing a Zero Trust model or something different. As encryption renders network traffic invisible to legacy solutions, your network’s security stack is effectively useless.
In response, many security vendors incorporate TLS inspection into their solutions. In effect, they decrypt traffic, inspect it, and then re-encrypt it before passing it on. But this “distributed TLS inspection” approach, in which decryption and re-encryption happens separately for each device in the security stack, brings problems of its own. Network bottlenecks and performance problems typically compromise service quality for business users and customers—an unacceptable penalty in today’s competitive business environment. What is more, the need to deploy private keys in multiple locations across the multi-vendor, multi-device security infrastructure expands the attack surface, increasing risk.
For the Zero Trust model to deliver on its promise, companies need a way to eliminate the Zero Trust model blind spot without sacrificing service quality.
Full Encrypted Traffic Visibility via TLS inspection
avoid the downsides of distributed encryption, a solution must provide full visibility to the enterprise security infrastructure through a dedicated, centralized SSL decryption solution. This needs to be complemented by a multi-layered security approach for optimal protection.
Solutions need to take a “decrypt once, inspect many times” approach, letting the entire security infrastructure inspect all traffic in clear text, at fast speeds, to avoid performance penalties and excess complexity. The following additional features also support the four key principles of Zero Trust discussed above:
User access control – SSL Insight can enforce authentication and authorization policies to restrict user access, log detailed user access information, and provide the ability to apply different security policies based on user and group IDs. Additional security services including URL filtering, application visibility and control, threat intelligence, and threat investigation help strengthen the security efficacy of the entire enterprise network.
Micro-segmentation – Granular traffic control, user and group ID-based traffic control, and support for multi-tenancy facilitate micro-segmentation.
Rapid incident detection and response – The Harmony® Controller SSLi app provides comprehensive, centralized visibility, and the ability to manage all SSL Insight deployments remotely from one location, ensuring that uniform policies are applied across the organization.
Flexible deployment and integration – As a vendor-agnostic solution, SSL Insight integrates easily with existing security devices by placing them in a secure decrypt zone.
Ease of Use – SSL Insight can be deployed within minutes in any network environment without causing any network outages or disruptions. Centralized management enables full visibility, uniform security policy enforcement, unified analytics, and SaaS traffic visibility across all SSL Insight deployments.
Without centralized and dedicated SSL inspection/TLS inspection, the Zero Trust model is unable to do what it was designed to do – protect our networks, users and data from threats residing inside and outside the network. SSL Insight provides a complete solution that not only enables the inspection of all incoming and outgoing traffic, but also provides additional security services that can help strengthen your Zero Trust strategy
About the Author
 Babur Nawaz Khan is a Technical Marketing Engineer at A10 Networks. He primarily focuses on A10’s Enterprise Security and DDoS Protection solutions. Prior to this, he was a member of A10’s Corporate Systems Engineering team, focusing on Application Delivery Controllers. Babur holds a master’s degree in Computer Science from the University of Maryland, Baltimore County. Babur can be reached at our company website https://www.a10networks.com/contact-us/contact-sales/
Babur Nawaz Khan is a Technical Marketing Engineer at A10 Networks. He primarily focuses on A10’s Enterprise Security and DDoS Protection solutions. Prior to this, he was a member of A10’s Corporate Systems Engineering team, focusing on Application Delivery Controllers. Babur holds a master’s degree in Computer Science from the University of Maryland, Baltimore County. Babur can be reached at our company website https://www.a10networks.com/contact-us/contact-sales/