Introduction
In today’s fast-evolving threat landscape, traditional breach detection systems often fall short in providing early warnings. CISOs are under pressure to not only respond to alerts faster but also to anticipate risks before they materialize. Public data, when harnessed correctly, provides a unique and critical early warning system for threats that have yet to trigger internal alerts. This article explores how leveraging public intelligence, including social media, open-source repositories, and curated feeds, can provide CISOs with valuable insights to stay ahead of potential threats.
Why Traditional Signals Come Too Late
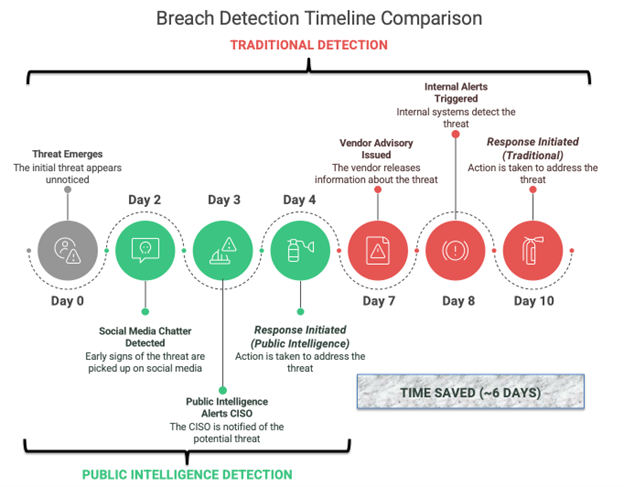
Reliance on traditional threat detection systems can leave gaps in identifying emerging threats early. Public data, including social media chatter and open-source repositories, often provides critical early signals that formal alerts miss. High-profile breaches like SolarWinds (2020) and Log4Shell (2021) revealed that the first signs of a breach frequently surface in social media and GitHub before they are acknowledged by vendors or internal security systems. Relying solely on vendor advisories and internal alerts puts organizations at a disadvantage, exposing them to prolonged risks.
With the average breach dwell time hovering around 10 days globally, early detection is crucial. Public intelligence can help shorten response times and reduce exposure by enabling organizations to act sooner than traditional detection methods allow.
Turning Public Data into Early Signals
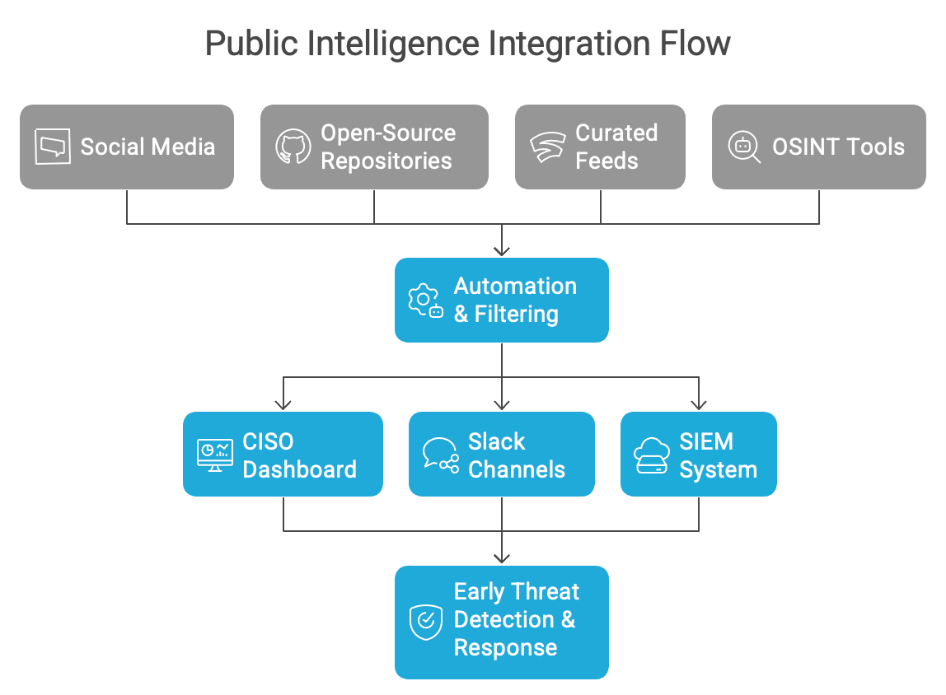
Proactive CISOs are integrating publicly available data into their early warning systems. Tools like Google Alerts, configured with phrases like “Fortinet zero-day” or “SAP breach,” offer instant visibility into emerging incidents. These alerts, routed to CISO dashboards or Slack channels, provide situational awareness without waiting on internal escalations.
Curated sources, such as Feedly Pro, can help filter out irrelevant content and focus on specific vendors, known exploit vectors, or niche research blogs. When paired with AI-powered assistants, these platforms can streamline the flow of critical insights and prioritize threats based on relevance to the organization’s infrastructure.
Open-source intelligence (OSINT) tools, such as Have I Been Pwned and Shodan, further enhance threat detection by tracking credential leaks and scanning public infrastructure for exposed vulnerabilities. By integrating these insights into existing security platforms, CISOs can automate threat prioritization and streamline incident response.
Social Signals: Where Real-Time Starts
Real-time risk intelligence now lives on platforms like X (formerly Twitter), Reddit, and GitHub. Researchers often disclose suspicious patterns hours, sometimes days, before formal publication. By monitoring specific hashtags like #cyberattack and following influential cybersecurity figures, CISOs can track the pulse of live threat activity.
Reddit forums like r/netsec and GitHub repositories often share actionable insights from practitioners in the field, including proof-of-concept exploits or vulnerable configurations. These real-time signals, while often unstructured, provide early indicators of potential breaches.
To scale this process, automation tools like Zapier or n8n can route social mentions, GitHub commits, or blog posts into triage workflows. These signals can then escalate into SIEM systems or trigger automated checks, helping organizations act before internal alerts are raised.
From Noise to Response: The Okta and MOVEit Lessons
Real-world breaches like Okta (2023) and MOVEit (2023) illustrate the value of public intelligence in early threat detection. In both cases, unusual activity was flagged on social media before the vendors acknowledged the issue. Organizations that acted on these early public signals were able to mitigate risk by isolating vulnerable systems or locking down accounts before formal advisories were issued.
While traditional alert systems are essential, public signals can enable faster responses and reduce an organization’s exposure window. By tuning into social channels and open-source intelligence, CISOs can detect breaches long before they are formally acknowledged.
Aligning Public Intelligence with Executive Goals
The ability to act on public intelligence not only improves response times but also enhances an organization’s security posture and reputation. According to IBM’s 2023 breach cost study, companies leveraging automated threat intelligence saved an average of $1.76 million per incident. This underscores the value of proactively integrating public intelligence into a company’s security strategy.
Public intelligence also allows CISOs to brief executives and boards before a breach becomes public, demonstrating foresight and proactive risk management. This helps build trust across the organization, positioning security as a key enabler of business continuity.
Build a Lean, Scalable Framework
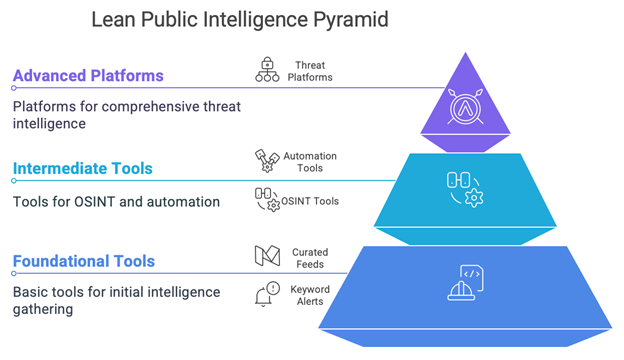
To get started with integrating public intelligence, organizations don’t need to overhaul their entire security strategy. Simple keyword alerts and curated feeds can provide immediate visibility into emerging threats. OSINT tools like Shodan, Have I Been Pwned, and others can be added as a layer on top of existing security infrastructure.
For more mature organizations, advanced threat intelligence platforms like Recorded Future or Flashpoint can be configured to reflect the specific technology stack in use, ensuring that alerts are tailored to the organization’s unique needs.
Over time, this lean approach can be scaled into a robust intelligence layer that augments the capabilities of existing SOC and threat response teams, improving both detection and response times.
Conclusion: From Reactive to Resilient
Today’s CISOs are not only technologists—they are intelligence leaders. By integrating public breach intelligence into their operations, CISOs can shift from a reactive security posture to a proactive, risk management strategy. Public intelligence provides early warning signals that allow organizations to act before threats escalate, reducing impact and response time.
As threats continue to evolve and regulatory demands grow, public intelligence will become an increasingly essential tool for modern cybersecurity. It’s no longer about faster detection—it’s about smarter, more adaptive leadership in a fast-moving threat landscape.
About the Author
 Aditya Gupta is a cybersecurity leader with over 21 years of global experience, specializing in identity security, breach response, risk management, and cybersecurity transformation. As Industry Principal and Segment Delivery Head for Americas at Infosys, he leads multi-million-dollar security programs for Fortune 100 clients. Aditya has won multiple industry awards, authored thought leadership articles, and served as a judge for global cybersecurity awards. He holds a Bachelor of Engineering and an MBA from FMS Delhi, along with certifications in CISSP, CCSP, and CCNA
Aditya Gupta is a cybersecurity leader with over 21 years of global experience, specializing in identity security, breach response, risk management, and cybersecurity transformation. As Industry Principal and Segment Delivery Head for Americas at Infosys, he leads multi-million-dollar security programs for Fortune 100 clients. Aditya has won multiple industry awards, authored thought leadership articles, and served as a judge for global cybersecurity awards. He holds a Bachelor of Engineering and an MBA from FMS Delhi, along with certifications in CISSP, CCSP, and CCNA

