Phishing isn’t what it used to be. It’s no longer fake emails with bad grammar and sketchy links.
With AI, modern phishing attacks have become slicker, more convincing, and dangerously well-timed. They can perfectly mimic a CEO or investor’s tone. They can even hijack real email threads or fake trusted login pages.
And one wrong click can mean catastrophic damage to your brand, data, and customer trust. That’s why playing defense isn’t enough anymore.
Preemptive cybersecurity, as the phrase suggests, is all about stopping phishing before it starts. Instead of waiting for damage to show up, this strategy proactively hunts down threats early, trains your team, and puts up barriers in the background.
The result is less risk, fewer breaches, and a lot more peace of mind.
In this post, we’ll look at how preemptive cybersecurity helps enterprises fight back and stay ahead of modern phishing attacks.
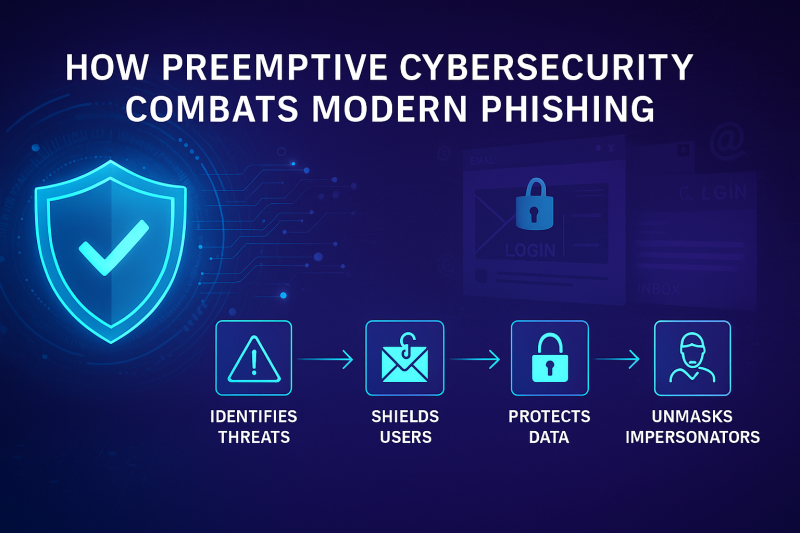
How Preemptive Cybersecurity Combats Modern Phishing
Modern phishing attacks are more targeted and personalized than ever. Preemptive cybersecurity provides a strong defense against this dark art because it doesn’t wait. It flips the switch from reactive to proactive, blocking the attacker before they even knock. Here’s how.
Preemptive cybersecurity:
- Identifies threats before they emerge: Preemptive systems scan patterns, behavior, and anomalies to catch red flags early. Even if it’s a zero-day phishing campaign, early detection means faster response.
- Shields users from spoofed emails, fake login pages, or bogus QR coded by filtering, flagging, and warning users and organizations before the damage is done.
- Protects customer data: If an attacker gains access through your employees, your customers are next. Preemptive strategies help seal those cracks before anyone slips through.
- Unmasks impersonators: From fake executive emails to lookalike domains, phishing thrives on deception. Preemptive tools help detect and take down impersonators (whether it’s a person or a brand) before they scam someone in your name.
So, how do you actually implement preemptive cybersecurity for your organization? There are a few ways and tools to make this happen.
Preemptive Cybersecurity Measures to Combat Modern Phishing
Here are four preemptive measures (and the tech stack) that are helping enterprises outsmart phishing attacks today.
1. Digital Risk Protection: Memcyco
When phishing evolves, most tools react. Memcyco doesn’t. It gets ahead of the threat.
Memcyco is built for preemptive cybersecurity, the kind that doesn’t just wait for alerts. It actively disrupts phishing, account takeovers (ATO), and digital impersonation attacks as they unfold.
Memcyco’s unique ability to infiltrate attacks as they evolve in real time sets it apart from other threat detection tools, delivering protection at each critical touchpoint in the fraud timeline. Its capabilities include identifying individual victims in real time, predicting and preempting ATO incidents, swapping real credentials with decoy data to sabotage the attacker, and disarming SEO poisoning schemes.
Memcyco goes beyond threat detection. It predicts, preempts, and breaks the phishing chain before damage is done.
2. Security Awareness Training: MetaCompliance

The best firewalls in the world can’t help if someone clicks the wrong link.
MetaCompliance fixes that. It turns your employees into your first line of defense with hyper-relevant, bite-sized training. It combines realistic phishing simulations and drills, interactive modules, and content tailored to different roles and departments.
Instead of standard, checkbox-style training, it engages employees by simulating real-life phishing tactics they can experience from the inside. They become exposed to targeted, up-to-date scam templates, and when someone fails a test, it delivers point-of-need training immediately, so behaviors are corrected before they become habits.
It also shows scoring dashboards and risk reports that highlight vulnerabilities, so you know your people’s progress over time. Over time, employees become your first line of preemptive defense.
3. Email and DNS Filters: TitanHQ
TitanHQ keeps phishing emails out of your inbox in the first place. Its SpamTitan (email filtering) and WebTitan DNS filtering combine to form a proactive gatekeeper.
SpamTitan scans and blocks phishing emails, spam links, malware, spoofed senders, or harmful attachments using multi-layered machine learning. It catches zero-day, polymorphic, and spear-phishing threats before they land in users’ inboxes, cutting the threat off at the source
Meanwhile, WebTitan DNS Filter sits at the DNS level. It breaks the phishing cycle by preventing users from loading fake or malicious websites. So if someone does click, the fake domain won’t load. AI-driven URL classification, SSL inspection, and real-time threat updates protect against newly minted phishing domains.
Altogether, TitanHQ stops phishing before it even reaches the inbox or yields a click, locking down the attack path with preemptive precision.
4. Zero Trust Endpoint Protection: IBM Trusteer Rapport
Phishing often aims for your weakest link: the endpoint. That’s where IBM Trusteer Rapport stands to protect.
It’s a preemptive cybersecurity lifeline at the device level. Trusteer Rapport detects and stops financial malware in real time and prevents users from entering phishing sites. It uses AI and behavioral machine learning to stop account takeover (ATO) attempts before they succeed.
Trusteer applies zero‑trust rules for every session, so if something feels off, access is blocked or flagged. It cleans existing infections and blocks drive-by downloads, man-in-the-browser (MitB) attacks, screen capture, and keylogging in real time. It also evaluates device, user behavior, network, and global fraud intelligence signals to spot anomalies before fraud happens.
Trusteer Rapport works quietly in the background, which means no slowdowns, no interrupting alerts. Users get a subtle green icon in their browser when they’re on a protected site (and grey if they’re not).
So even if a phishing link slips through the inbox, Trusteer Rapport acts as a last line of preemptive defense that stops fraud at the endpoint before it reaches sensitive data or user accounts.
Wrapping Up
Modern phishing doesn’t come simply knocking on your door. And it has AI on its side.
Preemptive cybersecurity flips the script by staying one step ahead, detecting threats before they land, training your employees to spot danger, and stopping attackers mid-play.
The preemptive cybersecurity tools mentioned above form a powerful shield, helping prevent phishing before it ever begins.