By Lydia Zhang, President & Co-Founder, Ridge Security Technology
Chief Information Security Officer (CISO) Emily Reed is responsible for safeguarding the digital assets of a thriving healthcare organization renowned for its advanced digital technology solutions.
On a busy morning, Emily’s routine was disrupted by an urgent message from her security team. They were made aware of other healthcare organizations that had recently succumbed to a critical vulnerability that attacked their MOVEit Transfer systems. A remote command execution flaw, this vulnerability can allow escalated privileges and potential unauthorized access to MOVEit server environments. Emily quickly gathered her team to examine the evolving situation.
Fortunately, Emily was aware of this vulnerability. She had preemptively purchased Ridge Security’s RidgeBot automated penetration testing product, recently upgraded with new plugins that automatically detect and exploit the MOVEit vulnerability.
Ridge Security’s Advanced Solution for CTEM Overcame the MOVEit Threat
RidgeBot is an AI-powered security validation platform for CTEM that proactively and continuously tests, validates, prioritizes, and resolves vulnerabilities and exposures. CTEM is a holistic and continuous approach focused on understanding the business context, identifying vulnerabilities and exposures, and prioritizing defenses based on real-world security risks. This approach is highly effective compared to traditional or reactive vulnerability management software.
RidgeBot scans a company’s entire network for software vulnerabilities and exposures and exploits them to simulate real cyberattacks. It detects and documents known threats, such as remote command execution, credential disclosure, sensitive information exposure, and database manipulation, providing clear evidence of the attack’s impact. These capabilities are performed within hours, based on the network size and complexity.
RidgeBot includes detailed prioritized risk assessment reports and has zero false positives. Report information, such as the attack topology, attack path, attack surface, vulnerability and risk details, and fix solutions, are also included. Information on the attack mechanism, such as the payload, exploit code and attack snapshot, is also provided.
Without wasting time, the team decided to put RidgeBot to the test. The first step was understanding the company’s digital landscape. They compiled an inventory of all IT assets, applications, and systems critical to their operations. This bird’s-eye view allowed them to identify potential weak points attackers might exploit. Emily realized the attack surface was larger than she had thought, which included legacy systems and third-party integrations.
With the complete inventory at hand, the team utilized RidgeBot for automated penetration testing. This system simulates the strategies of a skilled attacker by probing for vulnerabilities and exposures within the systems. The automation of this process allowed the team to apply real-world attack tactics and techniques at scale, identifying potential exploit points. RidgeBot conducted automatic scans across the applications, network infrastructure, and critical servers—areas that are typically vulnerable to attacks. It returned comprehensive data on the vulnerabilities it discovered, including the CVE number, CVSS score, and attack vectors, all in real-time. When the test reached 70% completion, RidgeBot flagged a critical risk, indicating that it had successfully exploited one of the vulnerabilities! Emily’s team was immediately alerted. They watched as one of their servers was compromised, with RidgeBot demonstrating its ability to execute commands on the server.
The entire team was on edge, sweat beading on their foreheads. Fortunately, this was a controlled environment, not an actual breach. Armed with detailed information from RidgeBot about the compromised server and the intrusion path, the team swiftly patched the server in question and reinforced the security policies to protect against similar attacks in the future.
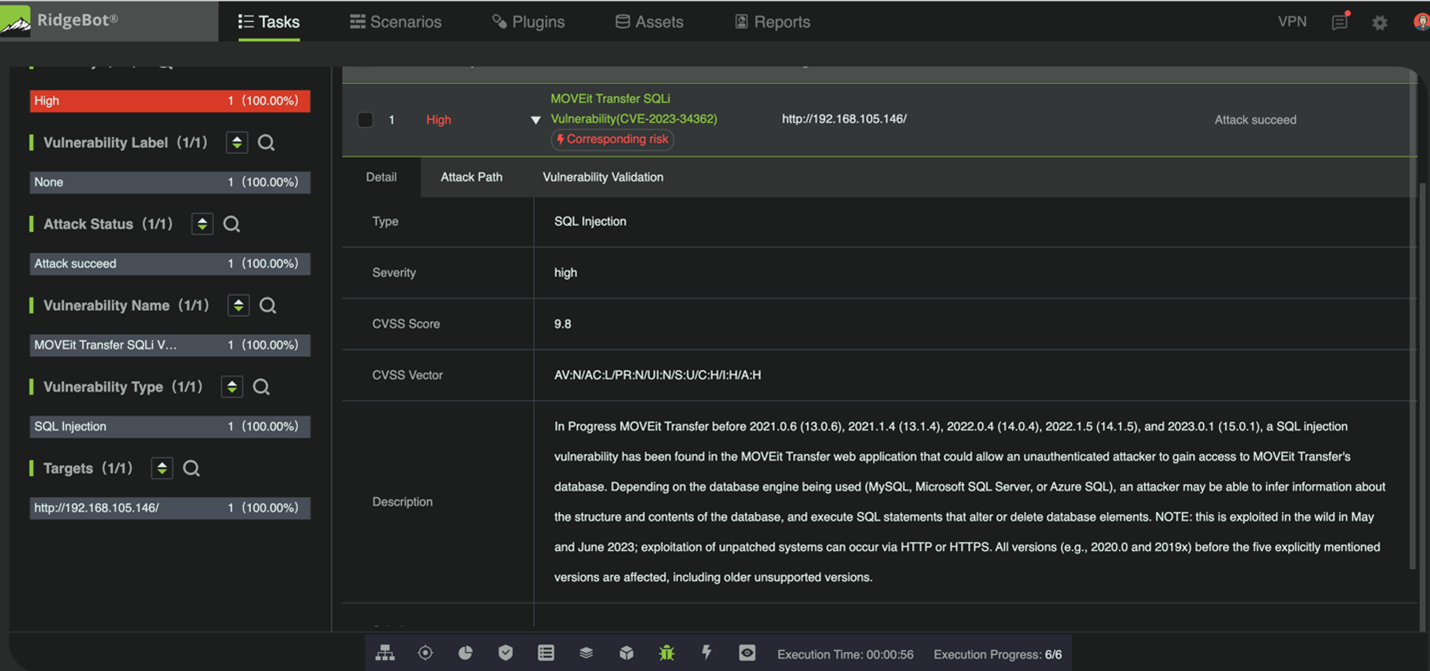
Figure 1: RidgeBot discovers MOVEit Vulnerability
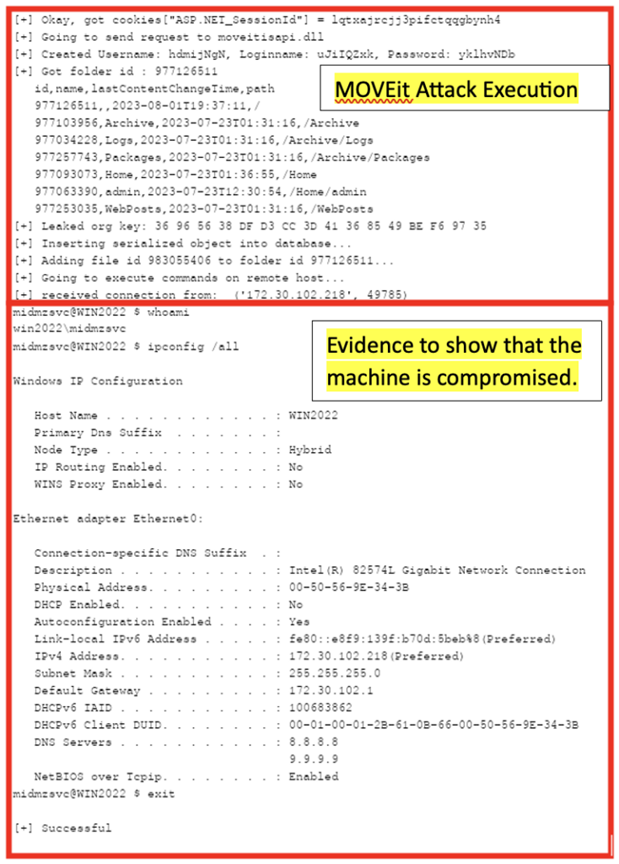
Figure 2: Evidence of MOVEit Exploit
Ultimately, RidgeBot automated penetration testing saved the organization from a potentially disastrous cyberattack. The attack surface was significantly reduced, critical vulnerabilities were fixed, and the organization’s defenses were fortified.
As this example portrays, deploying a comprehensive CTEM platform such as RidgeBot offers a range of compelling benefits, including real-time monitoring, continuous testing, and deep visibility into a company’s network vulnerabilities and potential risks.
Enhanced and Standardized Cybersecurity Risk Management
RidgeBot helps organizations improve their cybersecurity posture and resilience by providing information and recommendations on cybersecurity risk management, strategy, and governance.
Banks and other financial institutions are subject to compliance regulations, such as ISO 270001, PCI, SOC2, GDPR, and others. RidgeBot makes it faster and easier to support regulatory requirements and delves deeper with continuous testing for vulnerabilities and exposures associated with network changes, new software configurations, new apps, and adding new users and groups.
Automated penetration testing enables healthcare organizations to identify exposures, vulnerabilities, and weaknesses in their defenses. Unfortunately, many healthcare organizations only test annually or on an ad hoc basis. RidgeBot’s automated pentesting allows them to close the windows of opportunity for bad actors by running a test whenever they have a network change, configuration change, new application, and new users and user groups.
RidgeBot is easy to plug into DevSecOps processes and workflows, providing a streamlined and automated approach to security. Its plug-and-play nature allows for quick adoption within existing development, security, and operations processes, enhancing the overall efficiency and effectiveness of security practices.
By automating threat exposure management, RidgeBot ensures continuous protection throughout the software development lifecycle, from initial design to deployment and maintenance, aligning with the agile and fast-paced nature of DevSecOps environments. This integration simplifies securing applications and enables real-time response to potential vulnerabilities, maintaining a robust security posture in a dynamic and evolving threat landscape.
RidgeBot ensures consistent and thorough assessments, eliminating human error and saving valuable time. CTEM, with RidgeBot automated penetration testing, empowers organizations to stay ahead of cyber threats, bolster their security posture, and maintain a resilient digital environment. This dynamic combination enables proactive threat detection, rapid response to emerging vulnerabilities, and fortifying defenses based on up-to-the-minute data.
About the Author
 Lydia Zhang is President & Co-Founder at Ridge Security Technology.
Lydia Zhang is President & Co-Founder at Ridge Security Technology.
She holds an impressive entrepreneurial-focused resume that includes 20 years of leadership roles in network and cyber security. Prior to founding Ridge Security, Zhang held Senior Vice President and Product Management roles at Hillstone Networks and Cisco Systems. She holds double Master degrees of Computer Science and Communications management from University of Southern California.
Lydia can be reached online at https://www.linkedin.com/in/linglingzhang/ and at our company website https://ridgesecurity.ai





 We are in our 11th year, and Global InfoSec Awards are incredibly well received – helping build buzz, customer awareness, sales and marketing growth opportunities, investment opportunities and so much more.
We are in our 11th year, and Global InfoSec Awards are incredibly well received – helping build buzz, customer awareness, sales and marketing growth opportunities, investment opportunities and so much more.