Securing the Digital Frontier: How Micro Storage Technology is Rewriting Cybersecurity Protocols
The physical security of digital assets has long been the forgotten stepchild of cybersecurity strategy. While CISOs obsess over network perimeters and complex authentication protocols, a quiet revolution is happening in the world of micro storage technology that could fundamentally transform how we protect critical infrastructure and sensitive data.
Swissbit, a German technology company, is at the forefront of this transformation. Their innovative approach to secure storage isn’t just about encryption – it’s about creating an entirely new paradigm of data protection that starts at the hardware level.

Roland Marx, Senior Product Manager at Swissbit, understands the critical challenge facing modern organizations. “Many manufacturers don’t really know much about security,” he explains. “They struggle with understanding how to implement robust protection mechanisms.”
The European Cyber Resilience Act has dramatically accelerated the need for comprehensive security solutions. This groundbreaking regulation mandates that products with digital elements must demonstrate robust cybersecurity features, or face being locked out of the massive European market.
What does this mean for CISOs?
It means that traditional approaches to data protection are no longer sufficient. The days of treating storage as a passive repository are over. Modern storage must be an active participant in the security ecosystem.
Swissbit’s technology represents a quantum leap in this direction.

Their micro SD cards aren’t just storage devices – they’re intelligent security platforms. Each card functions like a miniature fortress, with multiple layers of protection that can prevent physical and digital tampering. Consider the practical implications for critical infrastructure.
“You have critical infrastructure,” Marx notes, “and one attack path would be the physical one. Currently, you cannot do anything. Everybody is accepting because there’s no other way.”
But Swissbit has created a way.
Their technology enables what Marx calls “immutability” – a concept that has become crucial in defending against ransomware and unauthorized modifications.
The technology isn’t limited to massive industrial applications.
From industrial control systems to IoT devices, from medical equipment to smart city infrastructure, these secure storage solutions can be integrated across multiple domains.
What makes Swissbit’s approach unique is its versatility. Their products can be configured for various use cases, from securing boot processes on devices like Raspberry Pi to protecting configuration data in complex industrial systems. “We can provision secrets in a secure manufacturing room,” Marx explains. “We can put certificates in a secure area, similar to a smart card chip.”
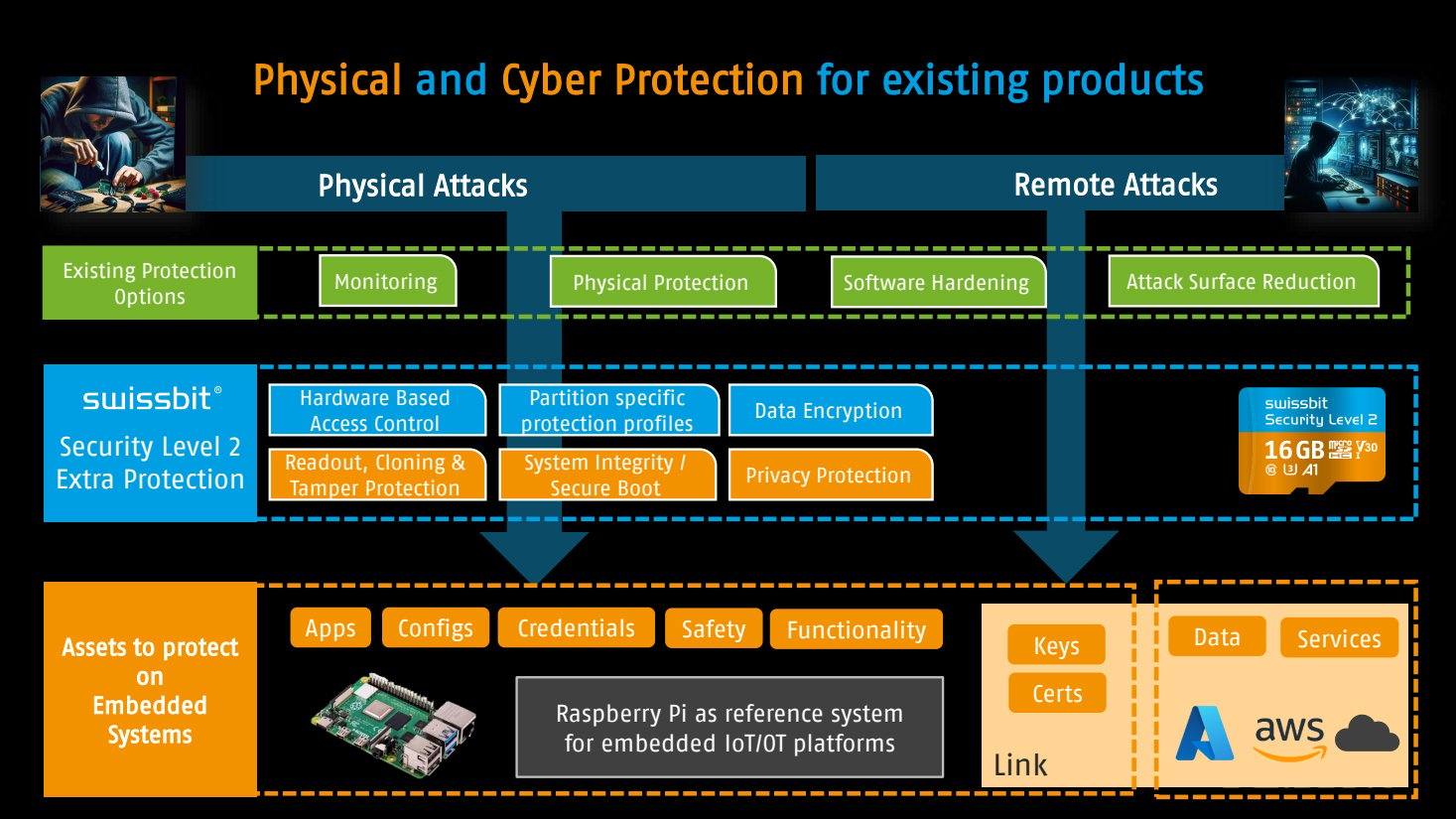
This isn’t just theoretical protection. The technology provides real-world defense mechanisms against increasingly sophisticated attack vectors.
For CISOs wrestling with compliance requirements, Swissbit offers a compelling solution. Their products can help organizations meet stringent European regulations without requiring complete product redesigns.
The company has developed a comprehensive matrix that maps their technology’s capabilities against specific regulatory requirements. This approach transforms complex compliance challenges into manageable, implementable strategies.
Key Considerations for Implementation:
- Assess current storage vulnerabilities
- Evaluate integration potential with existing systems
- Conduct thorough testing across different environments
- Develop a phased implementation strategy
The future of cybersecurity isn’t just about software patches and network monitoring. It’s about creating inherently secure systems where protection is built into the fundamental architecture of our digital infrastructure.
Swissbit’s approach represents more than a technological innovation. It’s a philosophical shift in how we conceptualize data protection.
Learn more at https://www.swissbit.com/en/
Call to Action
CISOs can no longer afford to treat storage as an afterthought. The time has come to view every storage device as a potential security endpoint, with its own intelligence and defensive capabilities. Investigate. Test. Implement.
Author’s Note: This exclusive interview was conducted live at the 2025 Black Hat Conference in Las Vegas, providing unprecedented insights into the future of secure storage technology.
About the Author
 Pete Green is the CISO / CTO of Anvil Works, a ProCloud SaaS company. With over 25 years of experience in information technology and cybersecurity, Pete is a seasoned and accomplished security practitioner.
Pete Green is the CISO / CTO of Anvil Works, a ProCloud SaaS company. With over 25 years of experience in information technology and cybersecurity, Pete is a seasoned and accomplished security practitioner.
Throughout his career, he has held a wide range of technical and leadership roles, including LAN/WLAN Engineer, Threat Analyst, Security Project Manager, Security Architect, Cloud Security Architect, Principal Security Consultant, Director of IT, CTO, CEO, Virtual CISO, and CISO.
Pete has supported clients across numerous industries, including federal, state, and local government, as well as financial services, healthcare, food services, manufacturing, technology, transportation, and hospitality.
He holds a Master of Computer Information Systems in Information Security from Boston University, which is recognized as a National Center of Academic Excellence in Information Assurance / Cyber Defense (CAE IA/CD) by the NSA and DHS. He also holds a Master of Business Administration in Informatics

