Cloud Security’s New Frontier: How Generative AI is Transforming Threat Detection
The cybersecurity landscape is shifting beneath our feet. Traditional perimeter defenses are crumbling, and cloud environments have become increasingly complex battlegrounds where attackers constantly evolve their tactics.
Enter Chen Burshan, CEO of Skyhawk Security, a visionary who understands that modern cloud security requires more than reactive monitoring – it demands proactive, intelligent defense strategies.
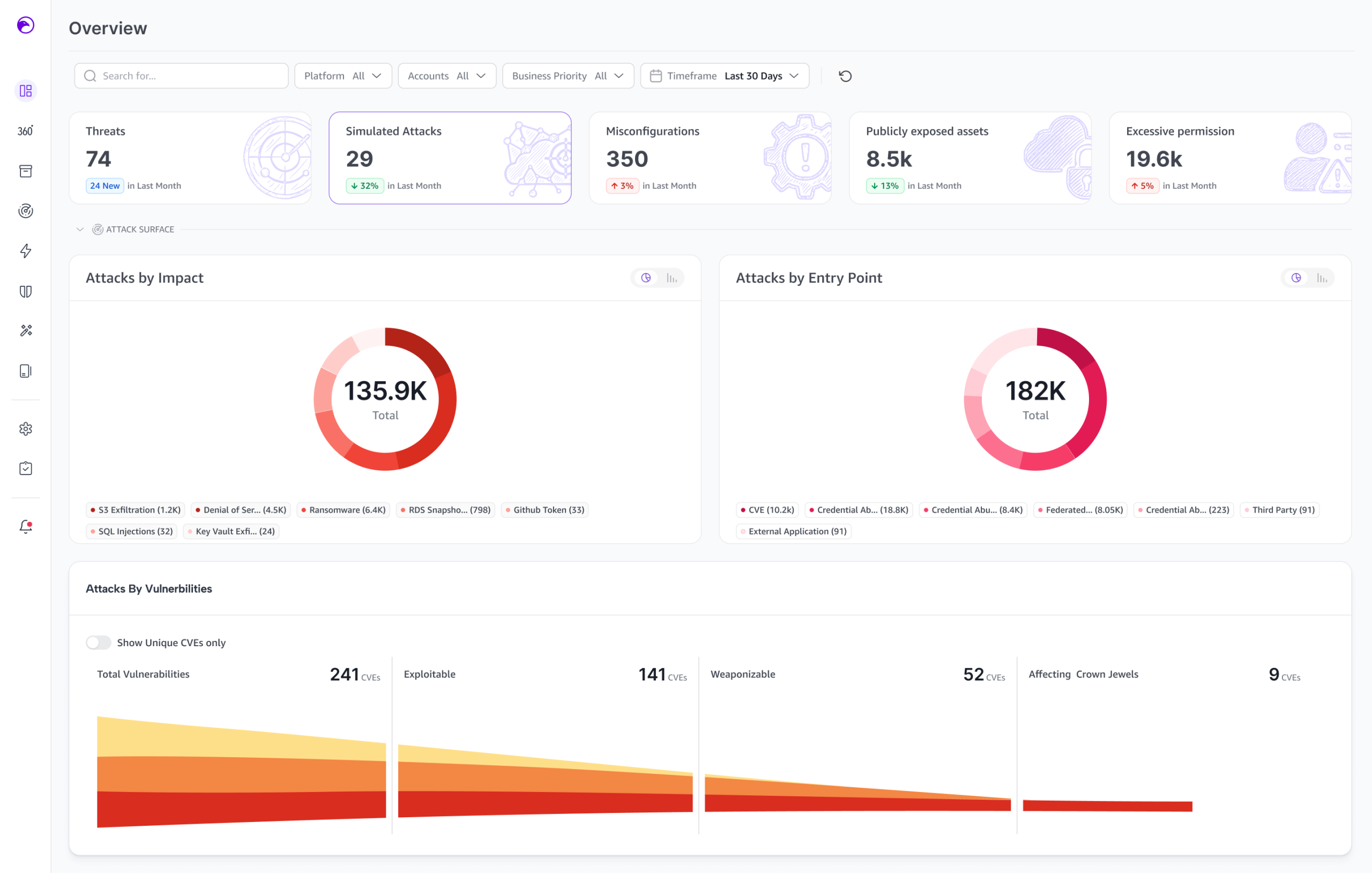
“Attacks on the cloud are almost doubling year over year,” Burshan explains. “There are no longer clear perimeters. In most cases, attackers aren’t breaking in – they’re simply logging in.”
This stark reality underscores a critical challenge facing today’s CISOs: how to detect and neutralize threats before they cause catastrophic damage. Skyhawk Security has developed a groundbreaking approach using generative AI to simulate potential attacks specific to each customer’s unique cloud environment.
Their platform doesn’t just detect threats – it anticipates them.
The Changing Threat Landscape
Modern cloud security isn’t about building higher walls. It’s about understanding the terrain, predicting movement, and neutralizing risks before they materialize.
“Attackers no longer break into the cloud through traditional methods,” Burshan notes. “Now, they can build generative AI-based attacks that are faster and more sophisticated than ever before.”
This technological arms race requires CISOs to think differently. Traditional vulnerability management approaches are drowning in false positives and noise, creating friction between security teams and developers.
Skyhawk’s solution transforms this dynamic by providing laser-focused, contextual threat intelligence.
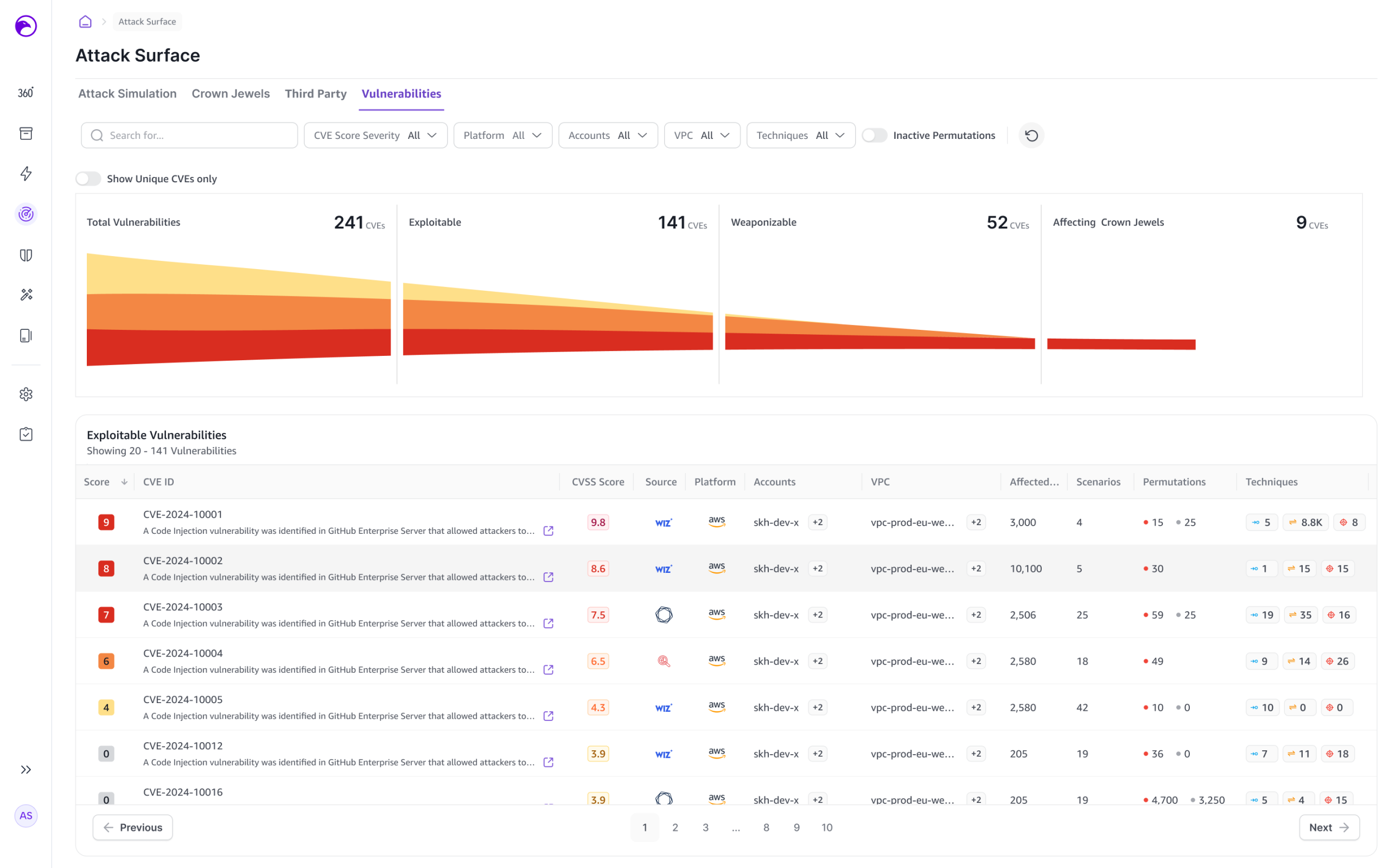
Reducing Noise, Increasing Precision
One Fortune 100 customer reduced their vulnerability findings from 500,000 to less than 300 – a 99% improvement in signal-to-noise ratio. Another organization trimmed over 60,000 potential issues down to a single critical concern. These aren’t just numbers. They represent real operational efficiency and dramatically reduced organizational risk.
“We help customers focus on the 0.1% that truly matters,” Burshan emphasizes. “Not through theoretical analysis, but by cross-referencing telemetry and providing genuine severity insights.”
The Platform: A Continuous Learning Engine
Skyhawk’s platform operates like an intelligent, adaptive immune system.
By continuously simulating attacks on a digital twin of each customer’s environment, the system learns and improves autonomously. Developers and security teams are no longer adversaries. Instead, they become collaborative partners in maintaining robust cloud defenses.
A CISO’s Perspective on Transformation
The traditional model of security – where CISOs are responsible but lack full authority – is obsolete. Skyhawk’s approach democratizes security without creating chaos.
“Shift left” strategies often create more friction than they resolve. Skyhawk bridges this gap by providing clear, actionable intelligence that both security and development teams can trust.
The Future of Cloud Security
Looking ahead, Skyhawk plans to expand its analysis to the application level, creating an even more comprehensive cloud detection and response ecosystem. Their open platform architecture will continue integrating feeds from multiple vendors, ensuring customers always have the most current, relevant threat intelligence.
Practical Recommendations for CISOs
- Embrace AI-powered threat simulation
- Prioritize contextual threat intelligence
- Reduce false positive noise
- Create collaborative security cultures
- Continuously adapt and learn
Call to Action
CISOs can’t afford to remain static. The threat landscape moves too quickly, and generative AI has fundamentally transformed attack methodologies. Visit Skyhawk Security’s website. Schedule a demo. Experience firsthand how AI can revolutionize your cloud security strategy.
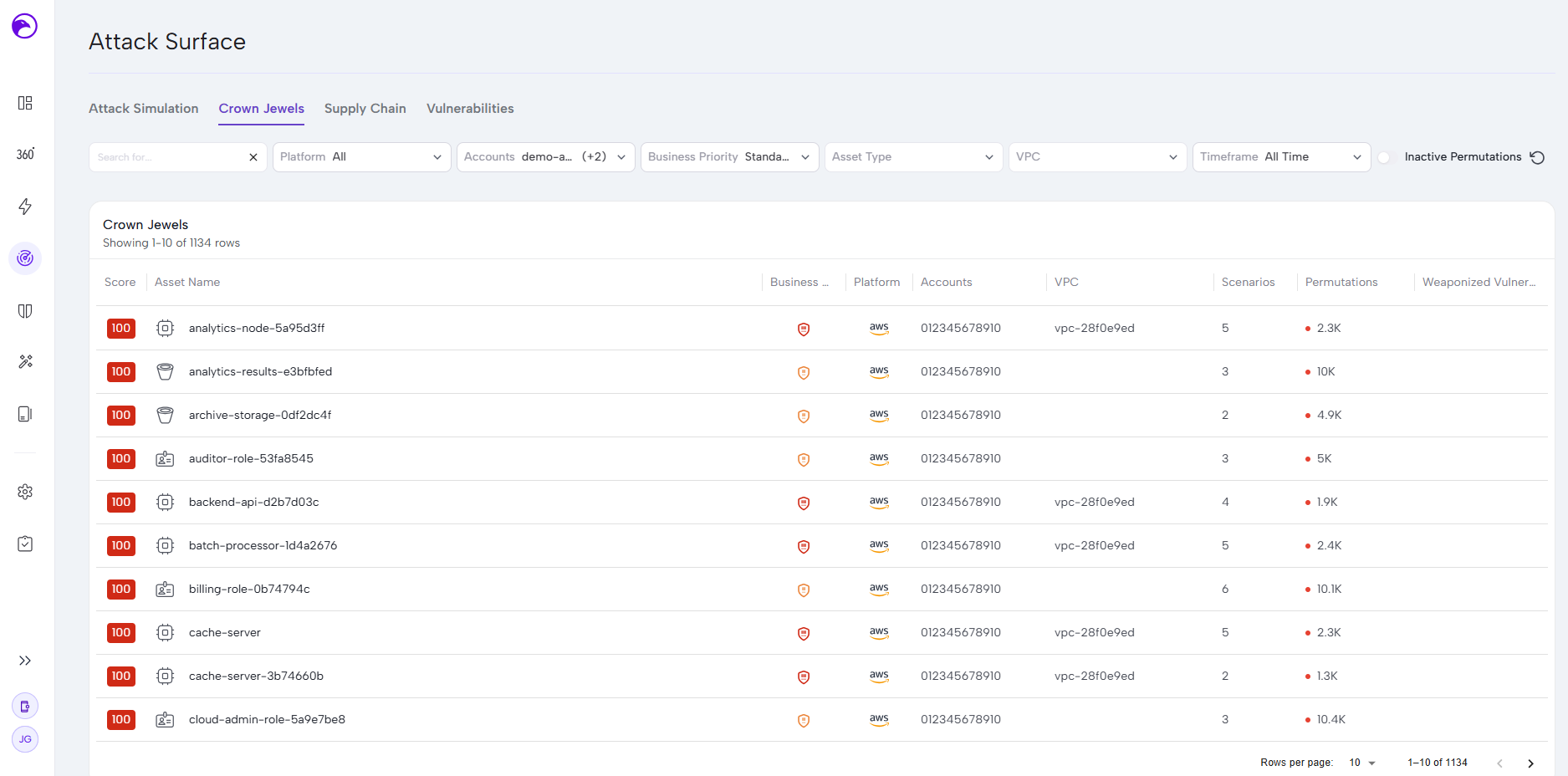
Skyhawk Launches Wiz Integration to Cut CNAPP Noise
In August, ahead of the Black Hat security conference in Las Vegas, Skyhawk Security announced a major product milestone: a new technical integration with Wiz, one of the industry’s leading cloud security platforms. This technical integration under Skyhawk’s analysis addresses one of the biggest pain points for CISOs today – the overwhelming flood of CNAPP (Cloud-Native Application Protection Platform) alerts that obscure truly critical risks.
According to Skyhawk, their Wiz integration reduces alert noise by up to 99%, allowing security teams to focus only on the threats that matter most. Instead of chasing tens of thousands of low-priority findings, customers can now zero in on a handful of genuine, high-severity risks. This shift represents more than efficiency – it directly translates into faster remediation cycles, tighter collaboration with development teams, and a measurable reduction in organizational risk.
The integration also builds on Skyhawk’s philosophy of contextual threat intelligence. By correlating Wiz’s visibility into cloud misconfigurations with Skyhawk’s AI-powered attack simulations, the platform doesn’t just highlight vulnerabilities – it validates whether those weaknesses could be exploited in real-world scenarios. This ensures that scarce SOC resources are spent on remediating risks that actually move the needle on security outcomes.
For CISOs and their teams, the takeaway is clear: cloud security must evolve from raw detection toward validated, prioritized intelligence. Skyhawk’s Wiz technical integration is an example of how Skyhawk reduce complexity while strengthening resilience – helping organizations cut through the noise to uncover hidden threats before attackers do. Learn more at https://skyhawk.security/
Author’s Note: This exclusive interview was conducted live at the 2025 Black Hat Conference in Las Vegas, providing unprecedented insights into the future of cloud threat detection and response.
About the Author
 Pete Green is the CISO / CTO of Anvil Works, a ProCloud SaaS company. With over 25 years of experience in information technology and cybersecurity, Pete is a seasoned and accomplished security practitioner.
Pete Green is the CISO / CTO of Anvil Works, a ProCloud SaaS company. With over 25 years of experience in information technology and cybersecurity, Pete is a seasoned and accomplished security practitioner.
Throughout his career, he has held a wide range of technical and leadership roles, including LAN/WLAN Engineer, Threat Analyst, Security Project Manager, Security Architect, Cloud Security Architect, Principal Security Consultant, Director of IT, CTO, CEO, Virtual CISO, and CISO.
Pete has supported clients across numerous industries, including federal, state, and local government, as well as financial services, healthcare, food services, manufacturing, technology, transportation, and hospitality.
He holds a Master of Computer Information Systems in Information Security from Boston University, which is recognized as a National Center of Academic Excellence in Information Assurance / Cyber Defense (CAE IA/CD) by the NSA and DHS. He also holds a Master of Business Administration in Informatics.

