Network Security Reimagined: How Portnox is Solving the NAC Nightmare
Security professionals have long wrestled with network access control (NAC) solutions that promise more pain than protection. Traditional NAC deployments have been notorious for complex configurations, endless troubleshooting, and frustrated IT teams. Fortunately for us, Portnox, a cloud-native solution that’s rewriting the rulebook for network security.

In an exclusive interview with Denny LeCompte, CEO of Portnox, we uncovered a compelling narrative of how modern network access control can transform enterprise security without inducing administrative trauma.
The NAC Problem: A Historical Perspective
Network administrators have horror stories about NAC implementations. Cisco and HP Aruba solutions have become legendary for their complexity and operational challenges.
LeCompte understands this landscape intimately.
“When I talk to people who have deployed a NAC 10 or 15 years ago, they’ll tell me it was maybe one of the worst experiences of their network career,” LeCompte candidly shared.
The fundamental issue? Traditional NAC solutions were architectural nightmares – complex, on-premises systems that required extensive professional services and created more security friction than protection.
Cloud-Native Reimagination
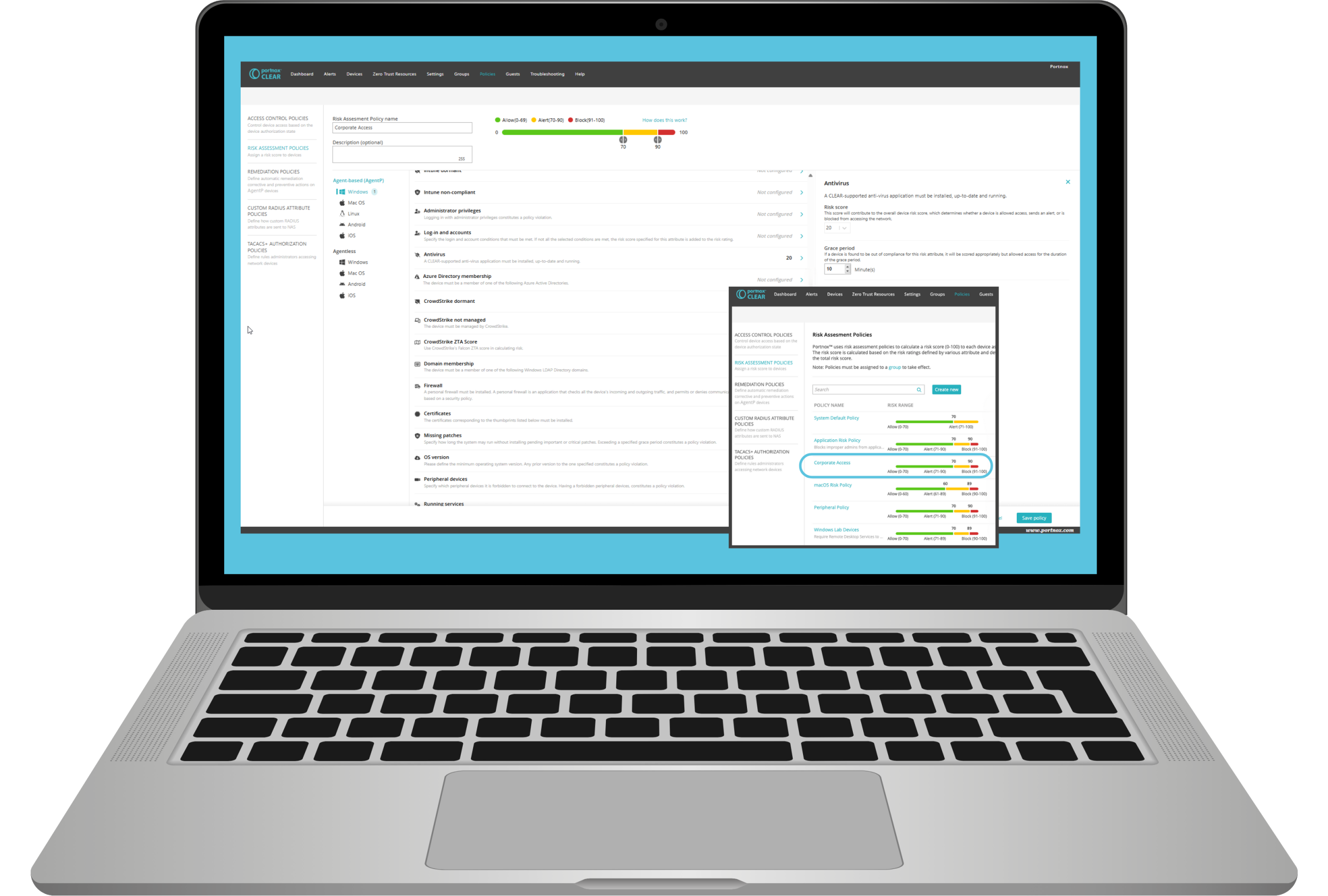
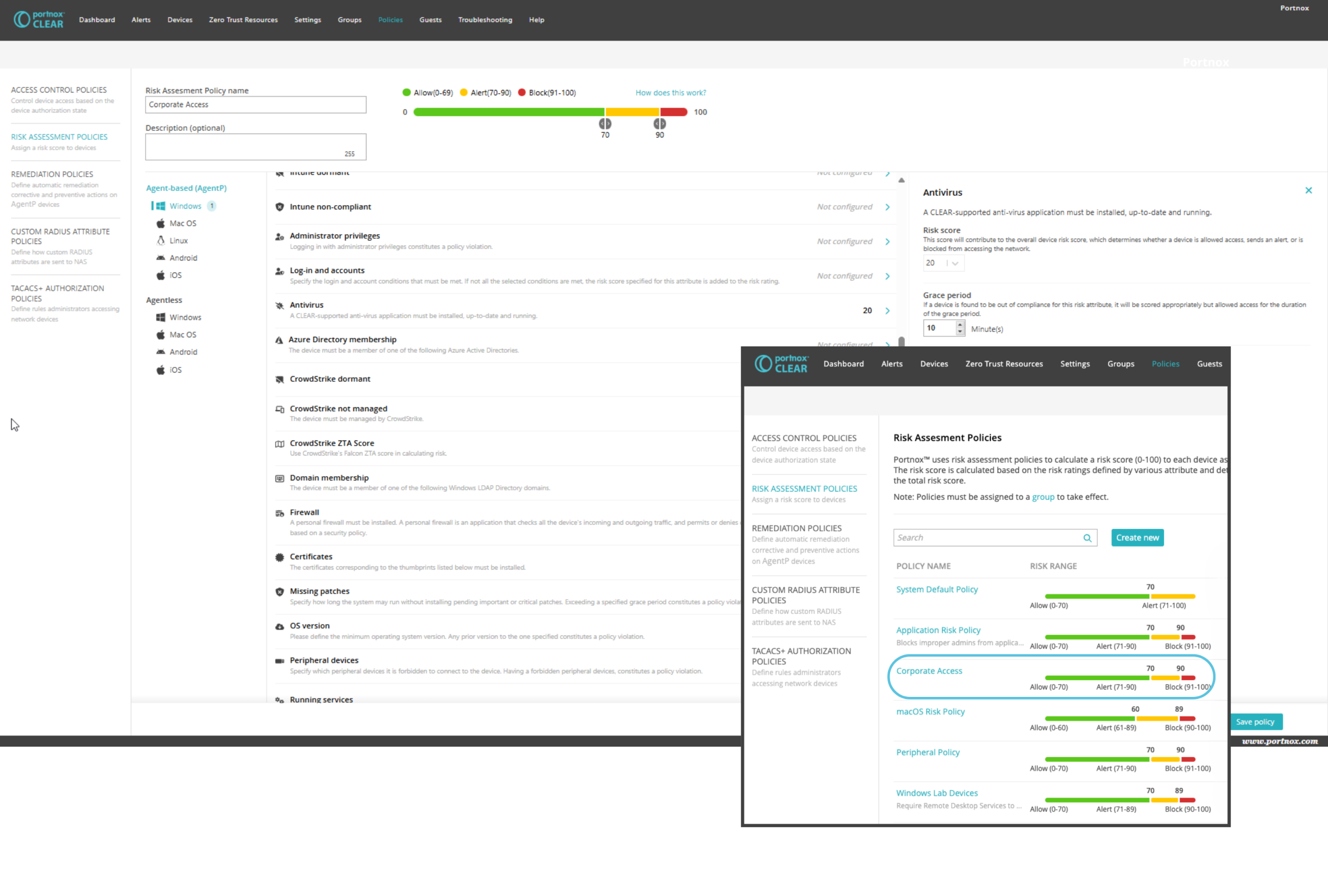
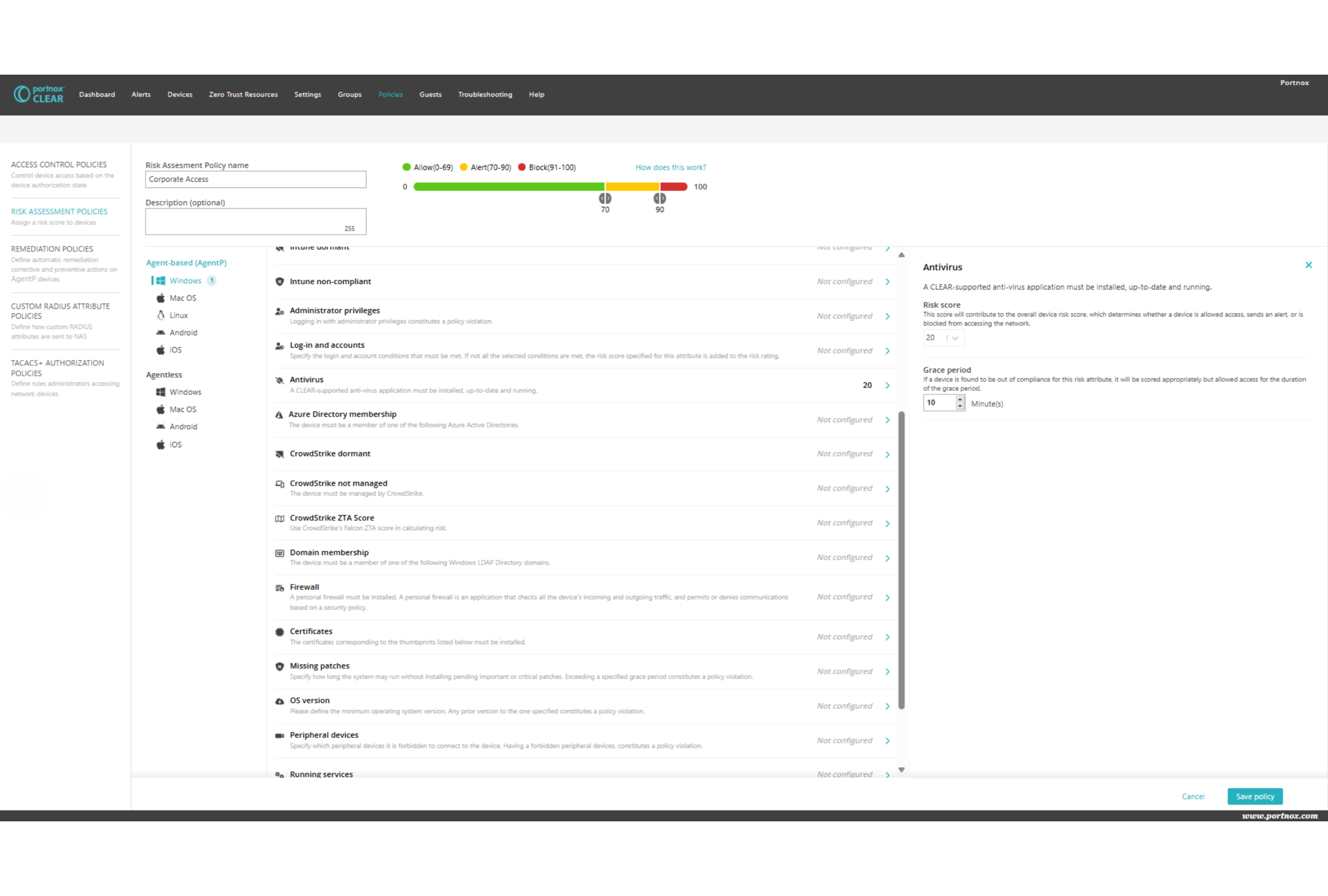
Portnox approached network access control differently. By designing a cloud-native solution built on the 802.1x protocol, they eliminated many traditional NAC headaches.
Key differentiators include:
- Zero on-premises infrastructure
- Standard protocol implementation
- Simple policy configuration
- Seamless third-party integrations
“Our product is totally in response to all the problems with classic NACs,” LeCompte explained. “We’ve made something that anybody should be able to configure without needing extensive manuals.”
Beyond Traditional Boundaries: Unified Access Control
Portnox isn’t just solving NAC challenges – they’re expanding the conversation into unified access control. Their recent Zero Trust Network Access (ZTNA) solution represents a strategic evolution in remote and hybrid work security. The ZTNA approach addresses critical modern challenges:
- Replacing legacy VPN technologies
- Providing certificate-based authentication
- Enabling secure access for contractors and BYOD environments
- Maintaining performance and user experience
Innovative Use Cases
The potential applications extend far beyond traditional enterprise environments. LeCompte shared a fascinating example from a construction company using their technology to manage complex, dynamic workforce environments.
“They’re putting GPS-enabled cameras in hard hats, tracking worker movements, and ensuring site safety,” he noted. “Everything is managed through their wireless network infrastructure.”
This example illustrates how modern network access control transcends traditional IT boundaries, becoming a strategic business enablement tool.
Security Posture: A Holistic Approach
Portnox’s solution doesn’t just control network access – it enforces comprehensive security posture requirements. Their approach allows organizations to implement granular policies across devices, users, and applications.
Key enforcement capabilities include:
- Blocking unauthorized applications
- Ensuring required security software is running
- Implementing continuous authorization checks
- Supporting multiple agent integrations
The Human-Centric Security Model
What sets Portnox apart is their commitment to user experience. They recognize that overly complex security measures often lead users to circumvent protection mechanisms.
“Security gets too hard. People start bypassing it any way they can,” LeCompte observed. “We want users to feel like nothing has changed.”
This philosophy represents a profound shift from traditional security approaches that prioritize control over usability.
Getting Started: A Low-Risk Path
For CISOs evaluating network access control solutions, Portnox offers a remarkably low-risk exploration path.
Their ZTNA product is currently available in a free, community-supported version.
LeCompte’s recommendation is straightforward: “Go try it. Go play with it. We feel confident that if people experiment, they’ll be impressed by how fast and easy it is to set up.”
Call to Action for CISOs
Modern network security demands innovative, flexible solutions. Portnox represents a new generation of access control technologies that understand the complex, dynamic nature of contemporary IT environments. Evaluate. Test. Transform.
Visit them online https://www.portnox.com/
Author’s Note: This exclusive interview was conducted live at the 2025 Black Hat Conference in Las Vegas, providing unprecedented insights into the future of network access control technologies.
About the Author
 Pete Green is the CISO / CTO of Anvil Works, a ProCloud SaaS company. With over 25 years of experience in information technology and cybersecurity, Pete is a seasoned and accomplished security practitioner.
Pete Green is the CISO / CTO of Anvil Works, a ProCloud SaaS company. With over 25 years of experience in information technology and cybersecurity, Pete is a seasoned and accomplished security practitioner.
Throughout his career, he has held a wide range of technical and leadership roles, including LAN/WLAN Engineer, Threat Analyst, Security Project Manager, Security Architect, Cloud Security Architect, Principal Security Consultant, Director of IT, CTO, CEO, Virtual CISO, and CISO.
Pete has supported clients across numerous industries, including federal, state, and local government, as well as financial services, healthcare, food services, manufacturing, technology, transportation, and hospitality.
He holds a Master of Computer Information Systems in Information Security from Boston University, which is recognized as a National Center of Academic Excellence in Information Assurance / Cyber Defense (CAE IA/CD) by the NSA and DHS. He also holds a Master of Business Administration in Informatics.

