The Silent Threat: Why Your AI Could Be Your Biggest Security Vulnerability
Imagine a digital Trojan horse sitting right in the heart of your organization’s most valuable asset – your AI systems.
What if the very technology promising exceptional insights and efficiency is simultaneously creating the most significant security breach in corporate history?
Luigi Caramico, founder and CTO of DataKrypto, describes AI as “the biggest and most sophisticated lossy compression system ever built,” and his words are a stark warning for today’s cybersecurity leaders. It’s a sponge that absorbs data without expanding, capable of regenerating precise information with alarming accuracy.
The AI Security Paradox
Modern CISOs face an unprecedented challenge. Our AI systems, designed to drive innovation and competitive advantage, are simultaneously our most significant vulnerability.
Caramico pulls no punches when he states, “AI is a disaster waiting to happen.”
The core issue? Visibility and vulnerability. Most AI models operate in clear text, meaning every single parameter – representing potentially millions of dollars in intellectual property and sensitive corporate knowledge – is fundamentally exposed.
When Caramico notes that “all AI is in clear” and that systems with “600 billion parameters” represent comprehensive organizational knowledge, it’s not hyperbole – it’s a critical security assessment. Consider the risks:
- Entire AI models can be stolen in a single breach
- Confidential prompts and responses are stored indefinitely
- High-privilege users can potentially access sensitive information
- Intellectual property is concentrated in a single, vulnerable point
Real-World Implications
Let’s examine a concrete example from our discussion.
Caramico describes a customer who collected over 100 million court documents – a massive intellectual asset. In the wrong hands, a competitor could instantly become a market leader by stealing this comprehensive dataset.
“If I’m number three and steal their documents,” Caramico explains, “I become number one overnight.”
The Encryption Revolution
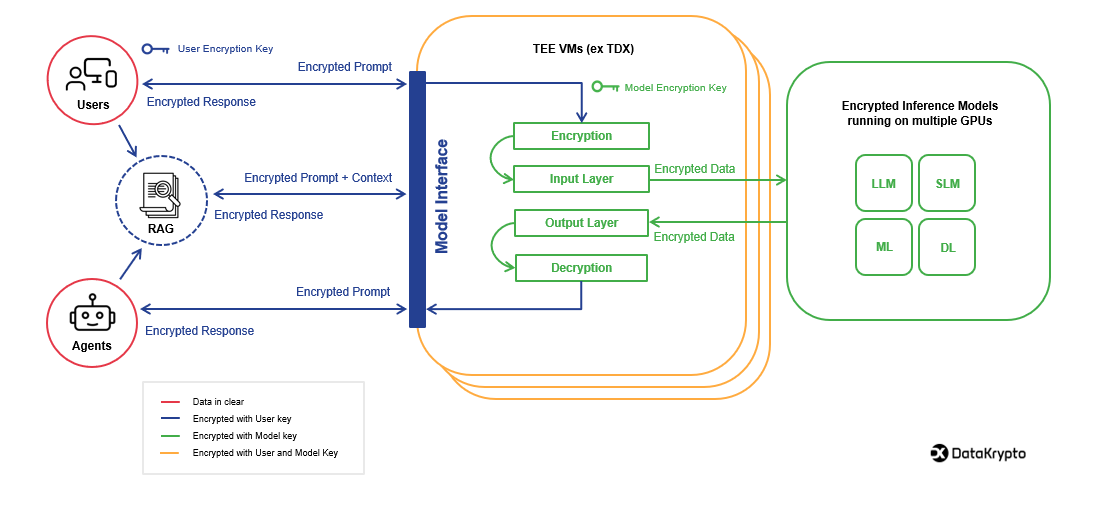
DataKrypto’s approach represents a paradigm shift in AI security. By leveraging Trusted Execution Environments (TEE) and advanced encryption techniques, they’ve developed a method to secure AI models without compromising performance. Key Security Innovations:
- Encrypting AI models at rest and in motion
- Ensuring only authorized users can access data
- Preventing system administrators from intercepting queries
- Protecting intellectual property from potential theft
The Technical Deep Dive
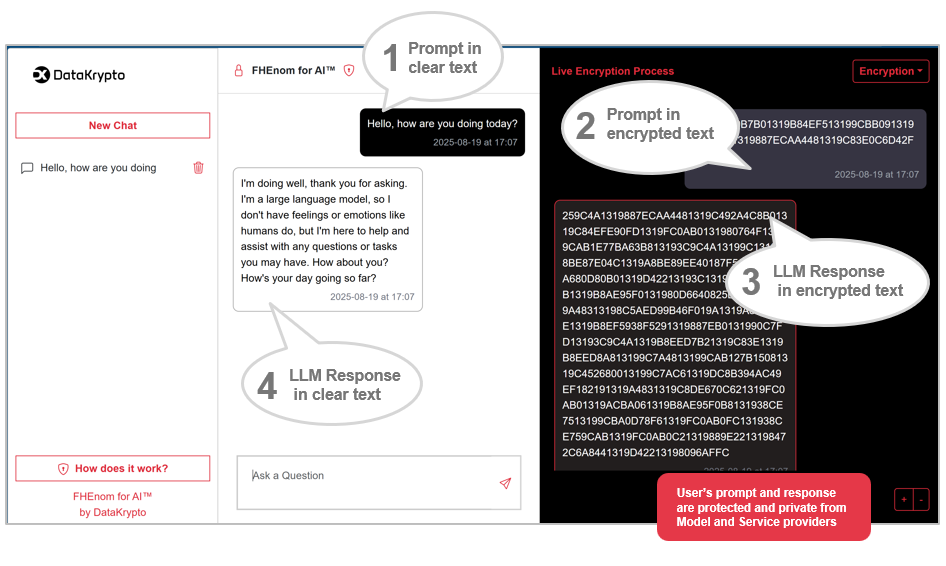
The solution isn’t just theoretical. By using technologies like Intel’s TEE, organizations can create a “black box” where encryption keys are stored securely within the chip itself. This means even if a bad actor breaches your network, the core AI model remains protected.
Caramico emphasizes that their technology ensures “you are the only person on the planet who can read the question and the answer” while keeping the model owner completely unaware of the specific interactions.
Practical Recommendations for CISOs
- Conduct a comprehensive AI security audit
- Evaluate current encryption methods for AI systems
- Consider advanced encryption technologies
- Implement strict access controls
- Develop a robust AI data protection strategy
The Human Element
Beyond technical solutions, CISOs must cultivate a culture of security awareness. Your team needs to understand that AI isn’t just another technology – it’s a potential treasure trove of sensitive information.
Call to Action
The time for passive security measures has passed.
As Caramico bluntly states: “Secure your AI before it’s too late.”
Every moment of inaction increases your organizational risk.
The AI revolution is here, and with it comes unprecedented security challenges. Encryption in AI isn’t just an option – it’s a necessity.
Learn more at https://datakrypto.com/
Author’s Note: This article is based on an exclusive interview with Luigi Caramico, founder and CTO of DataKrypto, a pioneering cybersecurity firm focused on AI data protection.
About the Author
 Pete Green is the CISO / CTO of Anvil Works, a ProCloud SaaS company and co-author of “The vCISO Playbook: How Virtual CISOs Deliver Enterprise-Grade Cybersecurity to Small and Medium Businesses (SMBs)”. With over 25 years of experience in information technology and cybersecurity, Pete is a seasoned and accomplished security practitioner.
Pete Green is the CISO / CTO of Anvil Works, a ProCloud SaaS company and co-author of “The vCISO Playbook: How Virtual CISOs Deliver Enterprise-Grade Cybersecurity to Small and Medium Businesses (SMBs)”. With over 25 years of experience in information technology and cybersecurity, Pete is a seasoned and accomplished security practitioner.
Throughout his career, he has held a wide range of technical and leadership roles, including LAN/WLAN Engineer, Threat Analyst, Security Project Manager, Security Architect, Cloud Security Architect, Principal Security Consultant, Director of IT, CTO, CEO, Virtual CISO, and CISO.
Pete has supported clients across numerous industries, including federal, state, and local government, as well as financial services, healthcare, food services, manufacturing, technology, transportation, and hospitality.
He holds a Master of Computer Information Systems in Information Security from Boston University, which is recognized as a National Center of Academic Excellence in Information Assurance / Cyber Defense (CAE IA/CD) by the NSA and DHS. He also holds a Master of Business Administration in Informatics.

